
Researchers monitoring activity on underground markets found that more than 460,000 payment card records were offered for sale in two days on a popular forum where such data is being traded.
The card info is split into four databases sold separately and offered in two rounds, on October 28 and November 27.
Black market price: over $550k
Initially, the seller advertised two databases, each with data for 30,000 cards and asked $3 for each card. The offer was discovered on Joker's Stash, a very popular market for buying and selling stolen payment card data.
The announcement said that 85% to 90% of the cards were valid and all came with all the details necessary for card not present transactions like online shopping.
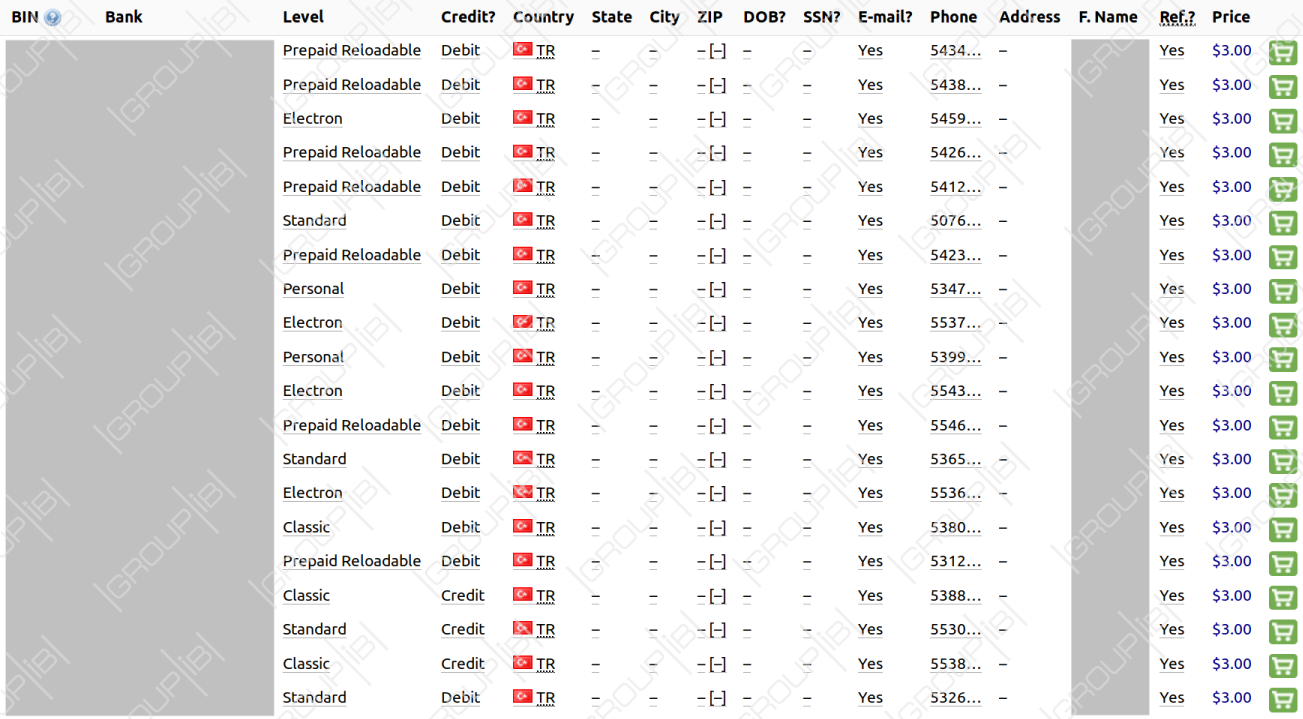
The names of the two caches (TURKEY-MIX-01 and TURKEY-MIX-02) indicate that the data is from cards issued in Turkey. Indeed, security researchers from Singapore-based cybersecurity company Group-IB were able to determine that the records were "predominantly related to TOP 10 Turkish banks."
Another month followed at the end of November when two databases were also offered. The same percentage for valid cards was advertised for these ones.
The number of cards included was much higher - around 190,000 in one and about 205,000 in the other, while the price for each was lowered to $1.
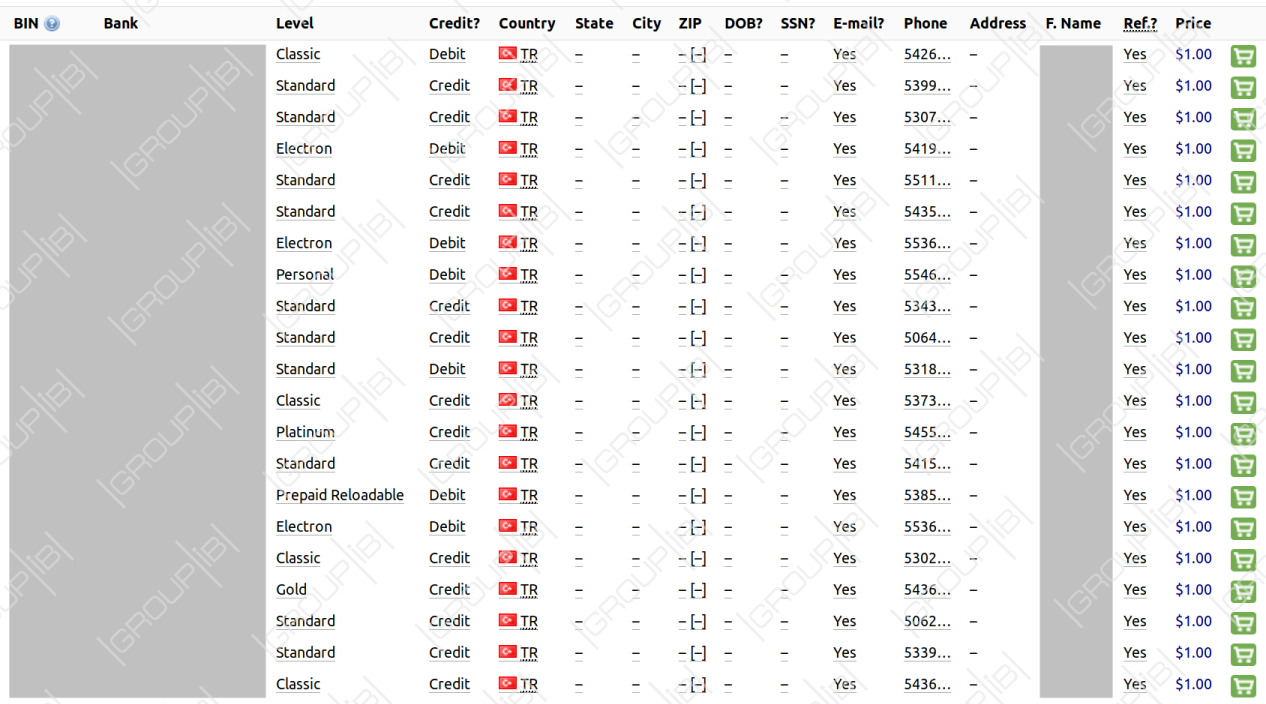
The records in all four databases are known raw cards, 'CCs,' or 'fullz' and included the expiration date, CVV code (card verification value), card number, and the name of the owner. Apart from this, info like email address, name, and phone number.
As they are not on the card's magnetic stripe - so it couldn't have been obtained from compromising PoS systems or ATMs - these additional details indicate that the data was collected as a result of online attacks.
Phishing could be one way to steal it. MageCart attacks on e-commerce stores are more likely, though, considering how widespread they are these days.
MageCart relies on JavaScript code, which Group-IB calls JS-sniffer, that typically loads on checkout pages and copies the card data filled in by users that complete a purchase.
While the source of the data is still to be determined, Dmitry Shestakov, the chief of Group-IBs research unit says that the company notified relevant Turkish authorities about the sale of these payment records.
As part of the company's standard procedure, the researchers notified the local CERT (Computer Emergency Response Team) immediately after the discovery and also alerted the affected parties so they could initiate mitigation actions.
"We always do our best to conduct proper outreach. It is extremely important that CERTs all over the world, official or private, could exchange threat intelligence data quickly In order to be able to swiftly and reliably react and localize threats and work together to ensure that they wouldn’t occur again." Group-IB representative
Group-IB's report shared with BleepingComputer notes that the four parts of the TURKEY-MIX database appeared out of the blue and had not been promoted before on other card shops or forums on the dark web.
The researchers say that Turkish cards are far from being common on specialized forums, this sale being the only big one for cards issued in Turkey.
Stolen cards can serve a variety of illegal purposes, using them to buy goods that are later converted to cash being the most common one. They also help cybercriminals pay for services needed in their activity or create fake digital identities.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now