Emotet has started a new spam campaign that pretends to be a scanned copy of Edward Snowden's new book. Unsuspecting users who open the attachment and enable its content will find that they have become infected with Emotet, most likely Trickbot, and possibly other malware.
After approximately four months of inactivity, Emotet woke up again on September 16th and since then has been spewing forth a legion of spam. These emails typically pretend to be invoices, financial documents, and other business documents with malicious Word attachments that infect you with a variety of malware.
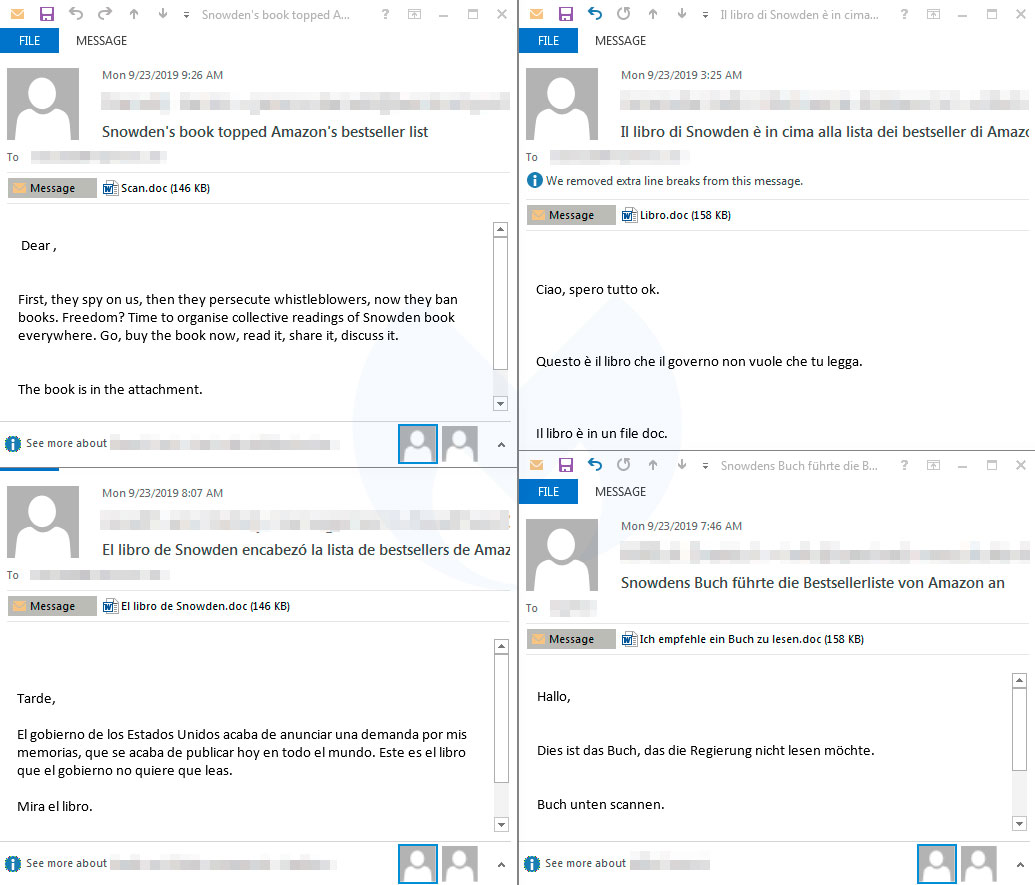
As part of Emotet's continuing evolution, security researchers at Malwarebytes discovered a new spam campaign that takes an original approach by pretending to have an attached scanned copy of Edward Snowden's new book "Permanent Record". The researchers saw Snowden themed emails in English, Italian, German, French, and Spanish.
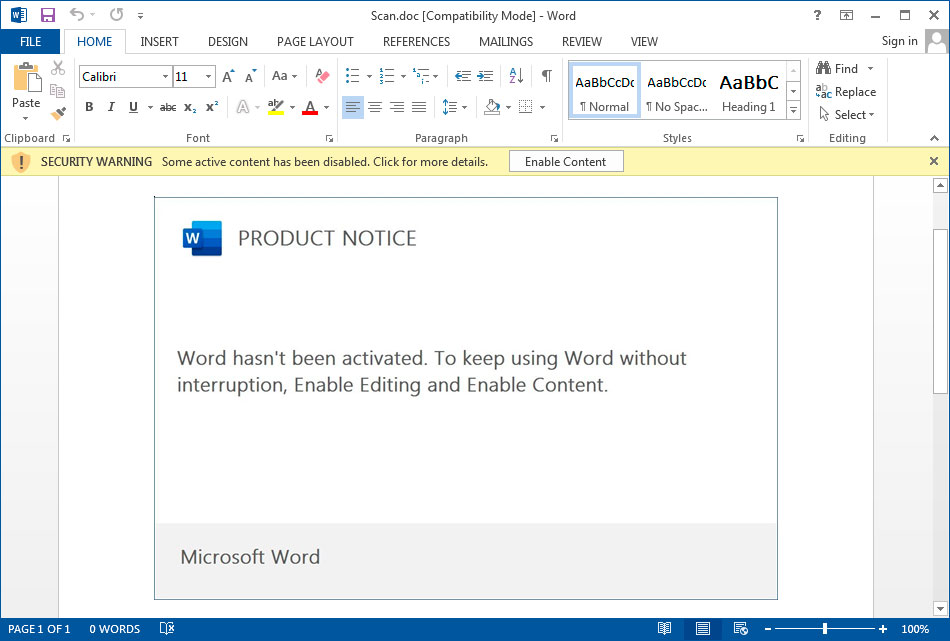
If the recipient opens the attachment, they will shown a message stating that "Word hasn't been activated" and that you need to click on Enable Editing or Enable Content to continue.
If the Enable Content button is clicked, a malicious macro will launch a PowerShell command that attempts to download Emotet from one of three embedded URLs.
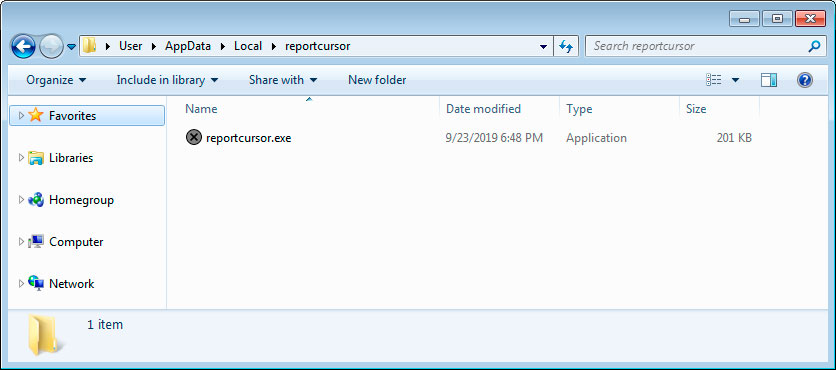
When successful, the Trojan will quietly run in the background and download and install other malware on the computer.
As always, never open attachments from anyone without confirming over the phone that they did indeed send you the file. You should also be cautious of enabling content or macros on any attachment you receive.
To be safe, you can also upload the attachment to VirusTotal in order to check for malicious macros.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now