
Check Point Software patched a vulnerability discovered in its Endpoint Security Initial Client software for Windows allowing potential attackers to escalate privileges and execute code using SYSTEM privileges.
The privilege escalation security flaw tracked as CVE-2019-8461 makes it possible for attackers to run malicious payloads using system-level privileges as well as evade anti-malware detection by bypassing application whitelisting, a technique commonly used to prevent the execution of either unknown or potentially malicious apps.
Threat actors commonly exploit this type of vulnerability during the later stage of their attacks, after the target machine was already infiltrated and they need to elevate permissions to establish persistence and further compromise the targeted machine.
Check Point Endpoint Security is a software that comes with multiple modules, including data and network security, advanced threat prevention and forensics, as well as remote access VPN software solutions, with parts of it being executed as a Windows service with top level NT AUTHORITY\SYSTEM permissions.
Loading arbitrary unsigned DLLs
SafeBreach Labs security researcher Peleg Hadar found that the security issue "could be used in order to achieve privilege escalation and persistence by loading an arbitrary unsigned DLL" into one of the Windows services used by the Check Point Endpoint Security software.
The vulnerability is induced by the lack of safe DLL loading caused by the use of an uncontrolled search path and by not validating if the DLLs it loads is signed with a digital certificate as Hadar details.
The researcher discovered that the Check Point Device Auxiliary Framework Service — one of the services used by the targeted software that runs with SYSTEM privileges and with an executable signed by Check Point — would attempt to load a missing DLL named atl110.dll from various folders within the Windows PATH environment variable.
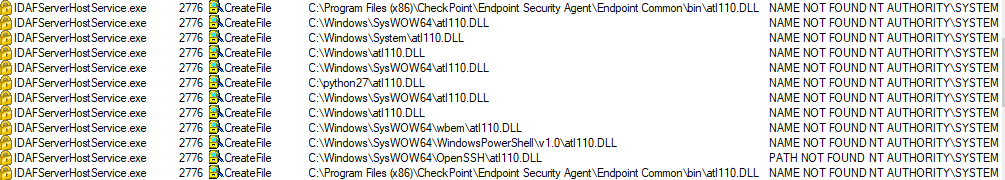
One of the directories probed by the service was C:/python27, a folder which comes with an access control list (ACL) providing any authenticated user with write permissions.
This allowed the researcher to load an unsigned DLL's privileges after loading it as a regular user, with the end result being that his code was executed from within a process digitally signed by Check Point as NT AUTHORITY\SYSTEM.
Check Point patched this vulnerability with the release of Endpoint Security Initial Client for Windows version E81.30 on August 27, following the vulnerability disclosure report sent by Hadar on August 1.
Check Point Endpoint Security Initial Client for Windows before version E81.30 tries to load a DLL placed in any PATH location on a clean image without Endpoint Client installed. An attacker can leverage this to gain LPE using a specially crafted DLL placed in any PATH location accessible with write permissions to the user. - Check Point
This is the third local privilege escalation vulnerability reported by Hadar to a security vendor during August after he found two more affecting Trend Micro's Password Manager and the free version of Bitdefender Antivirus.
Both of them could be exploited by attackers to load and execute malicious payloads in a persistent way and potentially evading detection during later stages of an attack.
Trend Micro and Bitdefender patched the security flaws (tracked as CVE-2019-14684 and CVE-2019-15295) after receiving Hadar's disclosure reports, with users receiving the updates via the automatic update features built within the two apps.


Comments
nqu35e - 4 years ago
This is not new, it had been going on, infact, I had persistent malware following me whatever window pc I lay my hand on, brand new is not excluded, it quickly get infected through default migration setting set by unknown administrators. Just forget antivirus, it will not detect anything because those users including window NT-AUTHORITY , is set to self granted escalating privileges to impersonate me and they log in automatically the moment I log in, it set deep in the registry, I can change the value to " 0 ", it will be enable to " 1 " at next reboot, I soon realised it is wise to log in with microsoft account, but still, the warning start coming in that the account problems, I should log in again with microsoft account, this mean, the pc is now in the hand of online administrator as network pc.
what I found out is that hacker had set me in memory and its' setting to automatically connect me in its domain network through window NT-AUTHORITY . if am setting new pc, after I finished setting online, I switch off the network, I do not want update start installing because NT-AUTHORITY, is set in firewall to download WED Drivers-only (Tcp-out),WED Drivers- only (Udp-out), I start by disabling all window NT-AUTHORITY, any users, these users is represented by SID like this one S-1-5-21-3149778896-3591747328-1830178181-500, I used to delete them but I found I was doing it the wrong way, my computer was still joining Domain netnetwork anyway, these users is security built in principal, you can not remove it, after block NT-AUTHORITY, I start replacing the SID with the same detail I log in with Microsoft account, it is me now built in local principal and even window NT-AUTHORITY now I replace with Me built in local principal, I set firewall rule no domain connection/join, those SID is users and they are so may set up carrying different functions including account unknown wich impersonate me and if I don't do it that way, I will be not having permission even open my own file and many restrictions and malware had been downloaded longtime, after finished with firewall, I now switch on network and update start, I will start enabling Service, because most service is set to manual or disable, I check all manually, this method give no chance to those users to download malware into the new pc.
what I remember is that, by the time first update is being downloaded, the users also busy downloading malware, by the time window finish installing update, malware is busy deleting drivers and replacing it with their own, they can set windows_ie_ac_001, this is new control window, this new window will be default and properly defended, No window update here and any Microsoft software will not install, most people will not realised that they are in the hand of hacker at this point, if you ever try to change permission here, the window will crush, any recovery/reset will not work, any restore point will be deleted, the window will be working normally and being run by account unknown.
One mystery, where the file those users downloaded, No scan can find it any way, antivirus will be disable/ corrupted and malware will use it for launching, I remember it took over kaspersky and was launching from there inside protected white list protected programs and application, I tried to uninstall it but it can not be done.
I believed the malware keep itself in (TEM), temporary internet file, because it is well protected, its' padlock and can't be deleted, I also change the environment while setting in system protection setting box, I replace (Tem ) with my own built in principal,as it is in firewall. now no trojan for the fist time in my pc, McAfee is doing great job, it is blocking any connection, saying they do not have permission from me to connect to my network. NT-AUTHORITY will be take easily by hackers and window security will recognised hacker and blocking the real pc owners, the method I used above is when the window is fresh install, if the window rebooted several time, you will be block from making any changes to the system, even opening firewall, it will say you do not have permission to open it.