
Hundreds of industrial companies are currently the targets of cyber-espionage activity from an advanced threat actor. The adversary uses a new version of an older info-stealer to extract sensitive data and files.
The attacker uses spear-phishing emails with malicious attachments often disguised as PDF files. Separ is the malware of choice, which steals login data from browsers and email clients, also hunting for various types of documents and images.
Victims in multiple countries
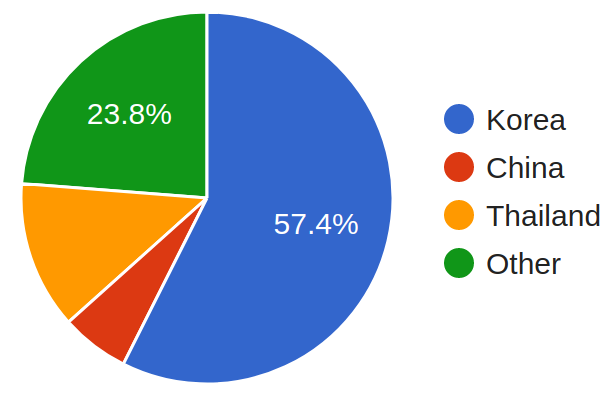
Dubbed Gangnam Industrial Style, the campaign compromised at least 200 systems. Almost 60% of the victims are in South Korea, including steel, pipes, and valves, manufacturers, an engineering company, and a chemical plant construction company.
A big player among the South Korean victims is a maker of critical infrastructure equipment supplying chemical plants, power transmission and distribution facilities, or firms in the renewable energy sector.
Companies in other countries that fit the same activity profile have also been hit, as researchers from CyberX's threat intelligence team Section 52 discovered compromised systems in Thailand (12.9%), China (5.9%), Japan, Indonesia, Turkey, Ecuador, Germany, and the U.K.
Industrial-themed phishing
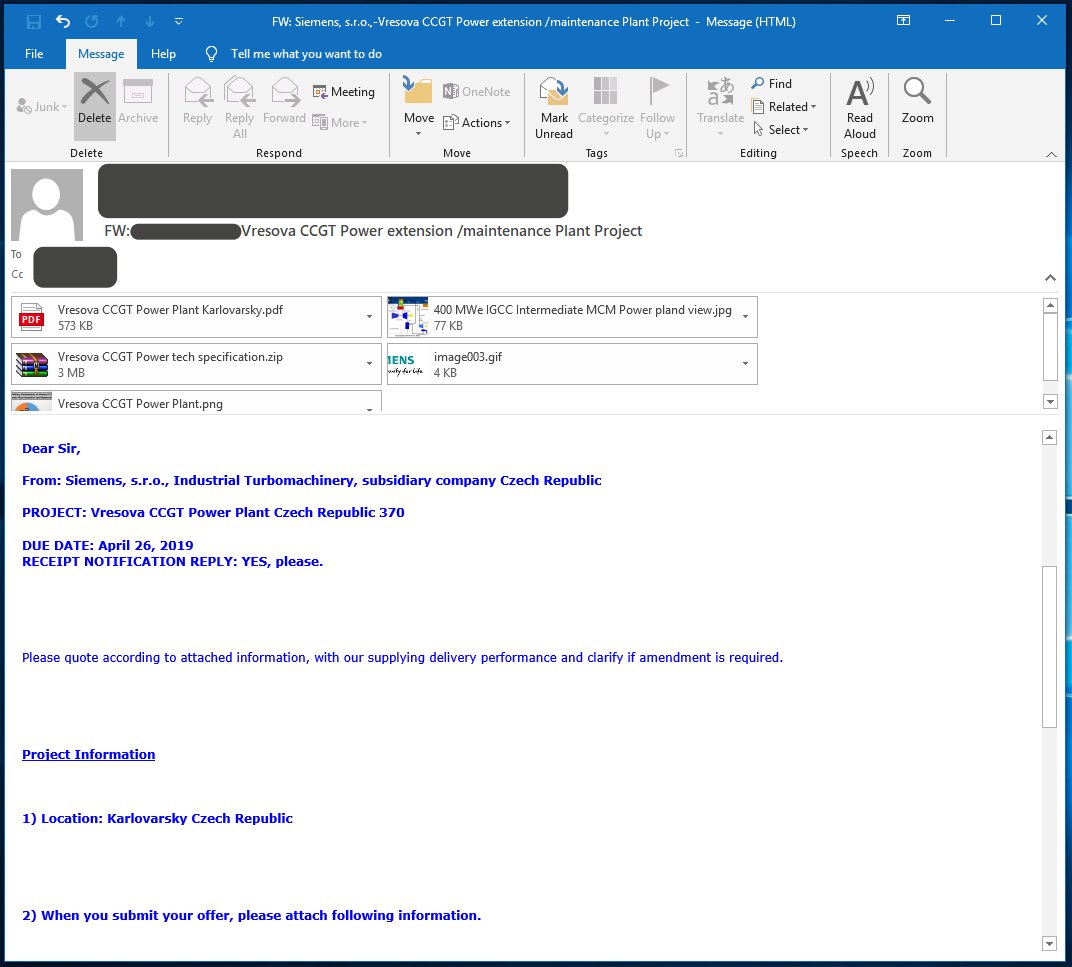
The malicious emails from the attacker are specifically created for the recipient. In one of them, the sender posed as an employee of a Siemens subsidiary making a request for quote (RFQ) for designing a power plant in the Czech Republic.
The message included a diagram and a publicly available technical paper on how to run the plant on fuel gas.
In another fake RFQ, the attacker simulated interest in building a coal-fired power plant in Indonesia and pretended to be the engineering subsidiary of a major Japanese conglomerate.

A new breed of Separ malware
CyberX security researchers analyzing the malware used in the Gangnam Industrial Style campaign noticed is the Separ info-stealer, publicly documented for the first time in 2013.
However, the variant used in these attacks is an evolved one compared to the capabilities seen by malware analysts in a previous Separ version from early 2019.
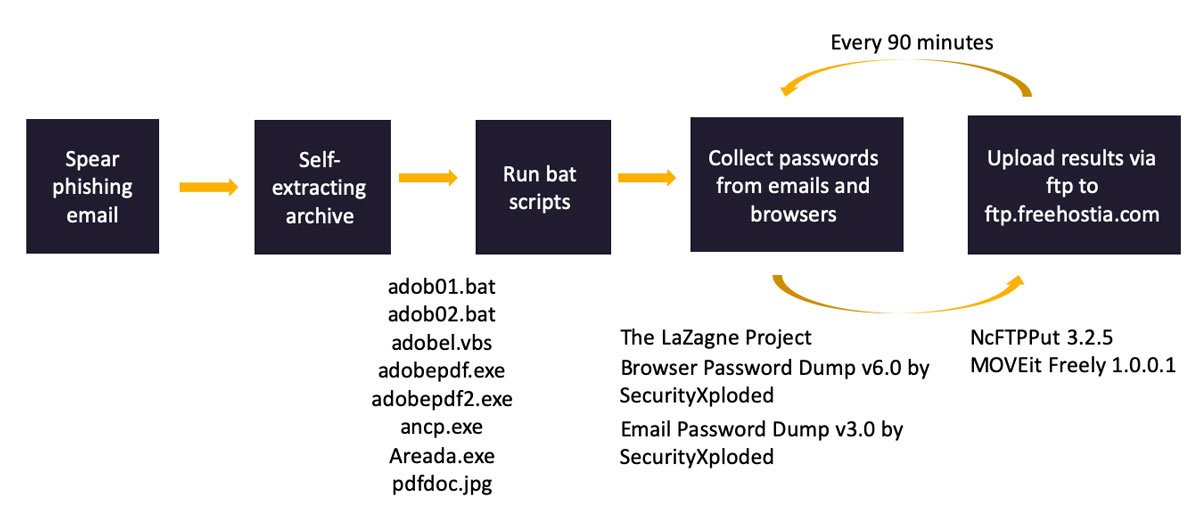
In a report today, CyberX notes that the malware relies on the Autorun feature to survive system reboots and comes with a host of mostly freely available tools:
- Browser Password Dump v6.0 by SecurityXploded
- Email Password Dump v3.0 by SecurityXploded
- NcFTPPut 3.2.5 – Free FTP client
- The LaZagne Project (password dumper)
- deltree (folder delete)
- Command Line Process Viewer/Killer/Suspender for Windows NT/2000/XP V2.03
- MOVEit Freely 1.0.0.1 – Secure FTP Client
- Sleep tool by tricerat
After installation, the malware steals credentials from browsers and email clients and looks for documents that may be important for the attacker based on their file extension.
All collected data is sent using the File Transfer Protocol (FTP) to the free web hosting service freehostia[.]com.
The researchers say that the Gangnam Industrial Style campaign is still active because they are seeing stolen credentials still being delivered to the attacker's command and control server.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now