
A phishing campaign using fake invalid account Stripe support alerts as lures has been spotted while attempting to harvest customers' bank account info and user credentials using booby-trapped Stripe customer login pages.
Stripe is one of the top online payment processors, a company that provides the payment logistics internet businesses need to accept payments over the Internet from their e-commerce customers.
This makes Stripe users the perfect target for threat actors looking to get their hands on their banking info, seeing that the company handles billions of dollars in payment every year.
Phishers have been targeting Stripe customers for a while now as seen from users and researchers' reports [1, 2, 3, 4, 5] and this just goes to show that users should always pay attention when handing over their personal information over the Internet.
Old tricks that still pay off
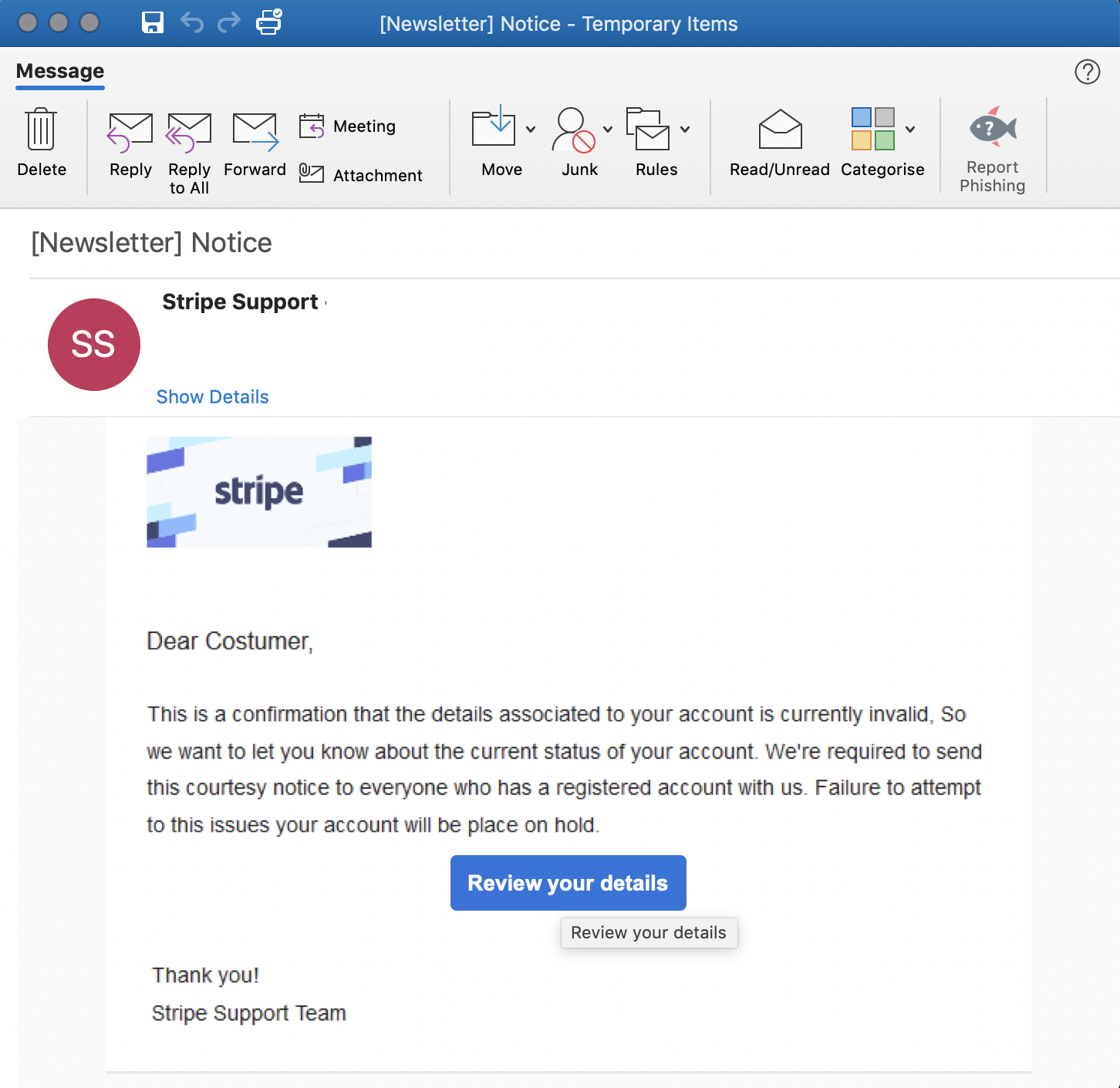
The Stripe phishing campaign was recently spotted by Cofense Phishing Defense Center (PDC) researchers. They found that the attackers hide the actual destination on the embedded "Review your details" button designed to redirect the Stripe customers to their phishing pages.
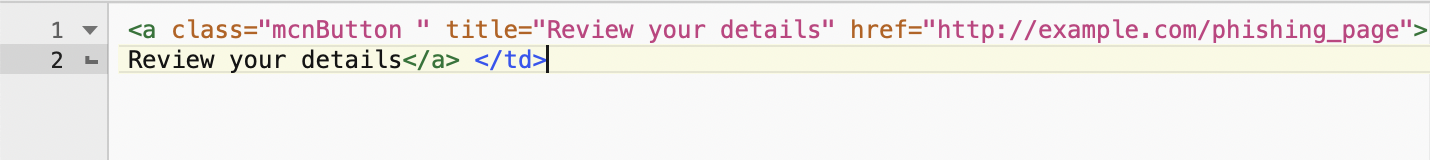
This known and proven to be effective technique uses an HTML-based trick to change the tooltip that appears when hovering the mouse pointer over the link by adding a custom title attribute.
"The true destination of this hyperlink is obscured by adding simple title to HTML’s tag, which shows the recipient the title “Review your details” when the recipient hovers over the button instead of the URL," found the researchers.
Invalid account notifications are used as the phishing bait messages, with the fake Stripe support message saying that "This is a confirmation that the details associated to your account is currently invalid" and that "Failure to attempt to this issues your account will be place on hold."
Despite the obvious grammar mistakes hinting at the fact that the phishers behind this campaign are not native English speakers, their coding skills are still on point.
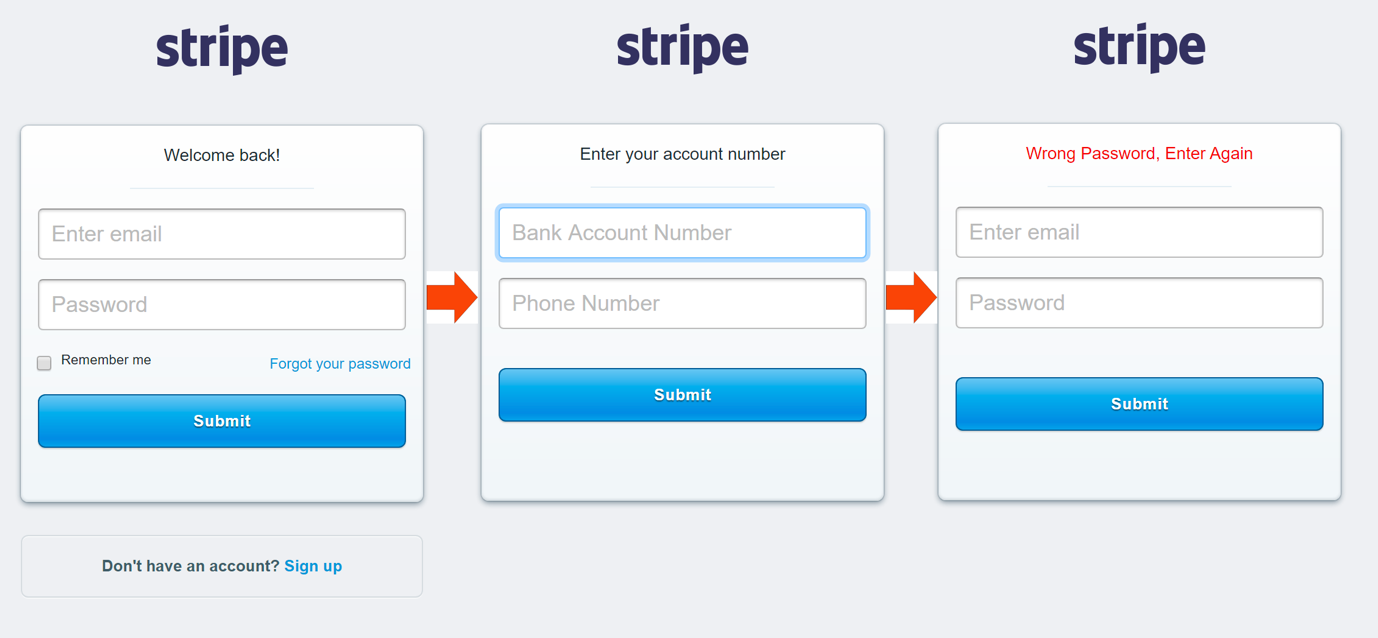
The button embedded within the phishing email works perfectly and it will send the targets who fall for the attackers' tricks to a cloned Stripe customer login page designed to collect their user credentials, bank account numbers, and phone numbers.
A chained series of fake login pages is used to harvest the victims' data, each of them designed to ask for a specific type of info, with the last one asking for their credentials one more time because they entered the wrong password.
The last page displays a “Wrong Password, Enter Again" message and it is used by the attackers to redirect their victims to Stripe's legitimate login page in an obvious attempt to avoid raising their suspicion and potentially blocking their accounts or changing the harvested credentials.
Stripe acknowledges on the company's support site that they also send email notifications to their customers once in a while, and they also provide the following tips that should help users avoid getting phished:
• Stripe emails will come from the “stripe.com” or "e.stripe.com" domains, and you can always reply directly to the message to get in touch with us.
• Only type your password into a website after confirming that it is the website you want, not one that was created to look like Stripe:
• Check the domain name for typos (such as “stirpe.com”).
• Check for our Extended Validation Certificate; this usually looks like a green lock next to the URL, and it lets you know that you are on the genuine Stripe website.
Stripe also recommends customers to protect their accounts using strong passwords and to add an extra layer of security by enabling two-step verification. Emails that look like a phishing attempt should be forwarded in-full to support@stripe.com or phishing@stripe.com.
Phishers juggling with phishing lures
While monitoring previous phishing attacks, phishers have been observed by security researchers while using a wide range of other phishing techniques.
For example, copyright infringement notices were used to bait Instagram users into giving away their credentials by filling out a 'Copyright Objection Form' within 24 hours to avoid account suspension.
In another phishing campaign, attackers infected U.S. taxpayers with the Amadey botnet malware via fake income tax refund emails that were also seen bypassing a secure email gateway.
Phishers also employed CAPTCHAs to block email gateways' automated URL analysis feature from analyzing the phishing landing page used to harvest Microsoft account information.
In June, another phishing campaign abused QR codes to redirect targets to phishing landing pages, thus effectively dodging security solutions and controls designed to stop such attacks in their tracks.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now