
Garmin Southern Africa (Garmin SA) disclosed today in a series of notifications sent to its customers that payment and sensitive personal information were stolen from orders placed on the shop.garmin.co.za shopping portal.
Garmin SA was previously a Garmin distributor named Garmin Distribution Africa (GDA) before being acquired by Garmin, a global leader in satellite navigation, on September 2011.
In a press release published on July 31, 2019, Garmin announced a "Record second quarter revenue of $955 million, a 7% increase, with aviation, marine, fitness and outdoor collectively increasing 12% over the prior year quarter."
Payment info including CVV codes stolen
"We recently discovered theft of customer data from orders placed through shop.garmin.co.za (operated by Garmin South Africa) that compromised your personal data related to an order that you placed through the website," said Jennifer Van Niekerk, South Africa Managing Director.
"The compromised data was limited to only Garmin’s South Africa site, and contained payment information, including the number, expiration date and CVV code for your payment card, along with your first and last name, physical address, phone number and email address."
Garmin SA recommends its customers to review and monitor all their payment card records for any unauthorized purchases.
Affected customers who received the data security incident notification are also urged to reach out to their bank or payment card providers if they see or suspect any fraud.
"As a valued customer, we apologize for this incident and assure you that Garmin takes our obligation to safeguard personal data very seriously," added Van Niekerk.
Possible Magercart skimming incident
While the cause of the breach is not mentioned in the notification email to the impacted Garmin SA customers, there are signs that the shop.garmin.co.za portal was the victim of a Magecart group.
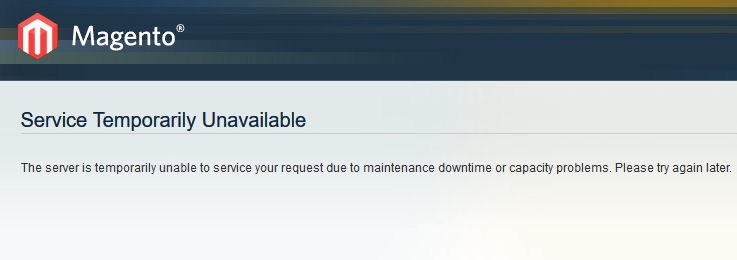
Currently, the breached shopping portal is now in maintenance mode and it displays a "Service Temporarily Unavailable" message with the following explanation: "The server is temporarily unable to service your request due to maintenance downtime or capacity problems. Please try again later."
Seeing that the portal runs on a Magento CMS there is a high probability that the Garmin SA customers' data was harvested with the help of a payment card skimmer embedded on the site's payment page according to
"While the cause is not mentioned, the kind of stolen data (typical checkout form fields) and the CMS (Magento) sound like a Magercart skimmer," said Malwarebytes security researcher Jérôme Segura.
Today Garmin disclosed a breach for its South African shopping portal 'shop[.]garmin[.]co[.]za' (now in maintenance mode).
— Jérôme Segura (@jeromesegura) September 12, 2019
While the cause is not mentioned,
the kind of stolen data (typical checkout form fields) and the CMS (Magento) sound like a Magercart skimmer. pic.twitter.com/tL65IbJwMq
Magecart groups are highly effective and continuously evolving cybercrime groups that have been around since at least 2015, operating campaigns as active as ever four years later.
As RiskIQ's head of threat research Yonathan Klijnsma said in a report from May 1 analyzing the expansion of Magecart activity to OpenCart and OSCommerce stores, "for every Magecart attack that makes headlines, we detect thousands more that we don’t disclose."
BleepingComputer asked Garmin SA to pinpoint the cause of the incident and to give an estimate of the total number of users impacted but had not heard back at the time of this publication. This article will be updated when a response is received.
H/T Jérôme Segura
Update September 13, 13:56 EDT: A Garmin spokesperson confirmed that the customers' credit card information was stolen from the shop.garmin.co.za e-commerce platform operated by a third-party using a card skimming script. Also, while roughly 6,700 South African customers were impacted by this incident, Garmin clients from other regions have not been affected.
Garmin recently became aware of a theft of customer data as part of a criminal cyberattack that affected customers who placed an order through shop.garmin.co.za. This e-commerce site was operated by a third-party on behalf of Garmin South Africa.
Promptly after learning of this incident, we immediately shut down the impacted system, began an investigation, and contacted the South African Information Regulator.
While Garmin does not store credit card information, the unauthorized party leveraged virtual skimming technology to capture customer details at the time of input, including credit card information.
The compromised data was limited to Garmin’s South Africa website which uses a separate e-commerce system operated by a third-party. This incident affected less than 6,700 customers in South Africa and does not affect customers who purchased from other Garmin websites in other regions.
We take our obligation to safeguard personal data very seriously and regret any inconvenience this may have caused our customers. We are in communication with our South African customers who may have been affected by this issue and are working on safeguards to prevent future attacks.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now