
A phishing attack using a novel technique to steal credentials from American Express customers was recently found in an email inbox protected using Microsoft’s Office 365 Advanced Threat Protection (ATP) by Cofense Phishing Defense Center researchers.
The phishing campaign targeted both corporate and consumer cardholders with phishing emails full of grammatical errors but with a small but deadly twist: instead of using the regular hyperlink to the landing page trick, this one used a base HTML element to hide the malicious URL from antispam solutions.
This allows the attackers to specify the base URL that should be used for all relative URLs within the phishing message, effectively splitting up the phishing landing page in two separate pieces. It also helps to hide it from the target since, on hover, the hyperlink will only show the end part of the malicious link, without the domain used to host the landing page.
The malicious mail "asks the would-be victim to verify his or her personal information 'Due to a recent system maintenance' and says that failure to comply would lead to a 'temporary suspension' of the account," says the Cofense report.
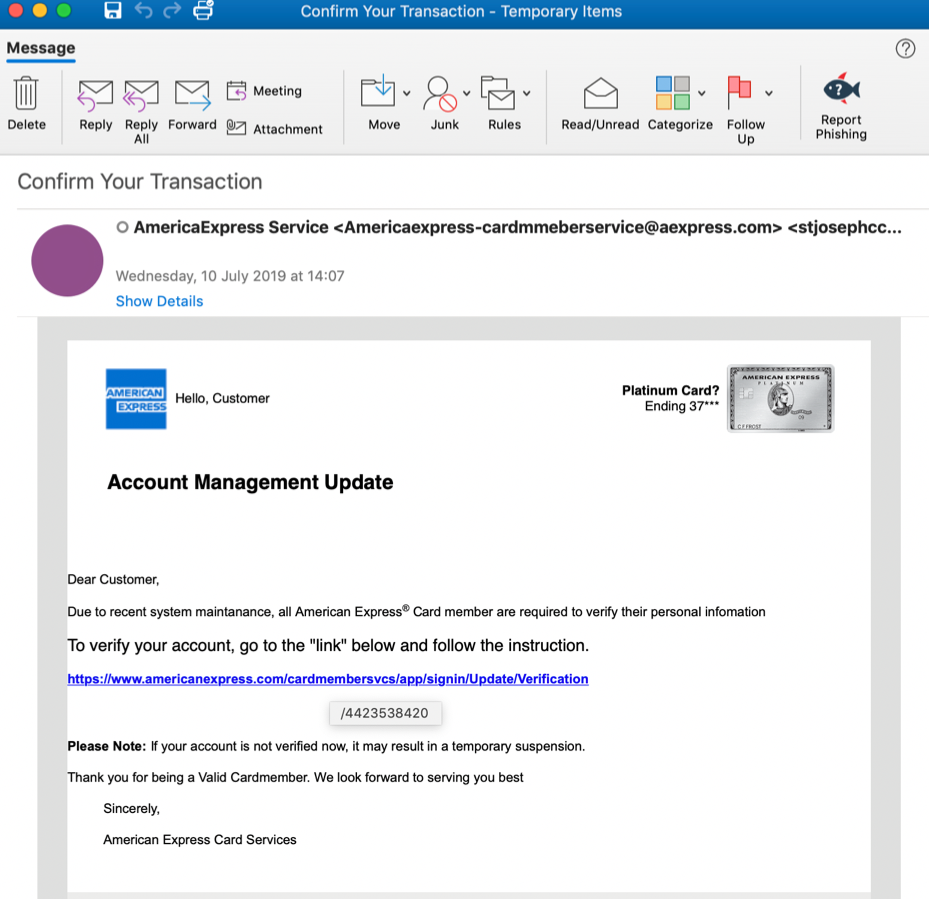
This is designed to induce a feeling of urgency with the attackers hoping that their victims will lower their guard and be a lot less vigilant as they open links they otherwise wouldn't even consider clicking.
Using the target's short term panic is a tactic all scammers use to increase the chances that their victims will be a lot more prone to make errors and be less careful when asked to send them sensitive information.
"The victim is urged to click on the hyperlink: hxxps://www.americanexpress[.]com /cardmembersvcs/ app/ signin/ Update/ Verification," says Cofense. "At first glance, this looks like it could be a legitimate site, but instead contains an embedded 'base href' URL which leads to the phishing page."
The phishing page is hosted on the domain used in the HTML tag, with the domain being the "building block for any URL when a href tag is called further down the page."
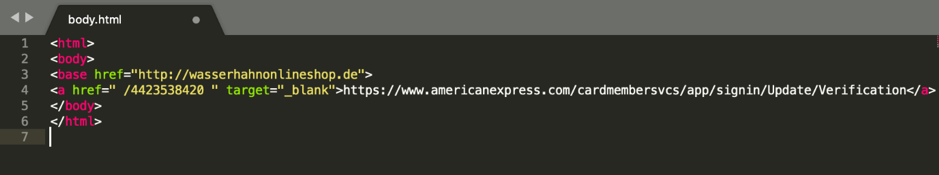
The malicious hyperlink redirects the users to the /4423538420 link which gets stitched at the end of the base href element and becomes the full landing page address.
"This tactic helps the attacker evade URL filters and gateways that have active URL scanning services, which currently do not have the capability to combine these inert pieces into a scannable malicious URL," says the report.
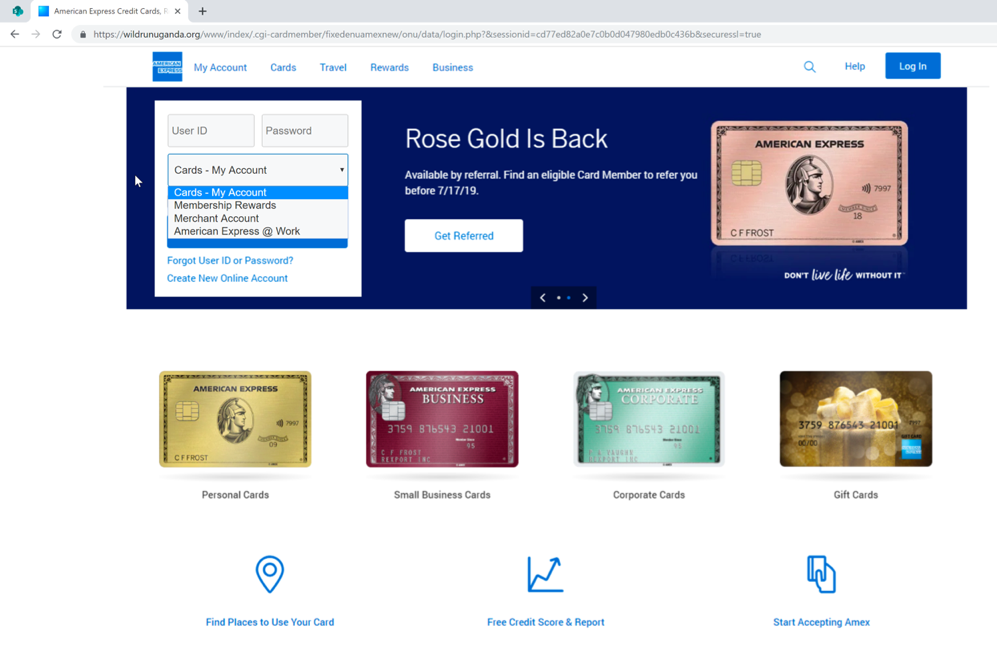
The actual landing page the victims are sent to is an American Express login portal lookalike, with the following four types of AMEX accounts being targeted by the crooks, as the drop-down menu on the top left side of the phishing page clearly shows:
- Cards – My account (a personally held American Express account)
- Membership Rewards accounts
- Merchant Accounts
- American Express @ Work (corporate accounts)
"The broad stroke attack would be very efficient when sent en masse, especially with its clever technique for bypassing URL filters and email gateways," concludes the Cofense research team.
This is not the first time AMEX customers have been targeted by phishing campaigns with two of them going after American Express clients to steal their credit card and social security information as discovered by the Office 365 Threat Research team in March.
Back in December, scammers running another AMEX-focused campaign used a credit card security issues "hook" and prompted the targets to open an attached HTML phishing form which sent the inputted info back to the crooks.
It also is important to keep in mind that companies, especially financial organizations such as banks, will not request highly sensitive information via online forms.
Furthermore, if one receives an email with links to websites that ask for personal information, it is strongly recommended to contact the organization using a phone contact to confirm the contents of the email.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now