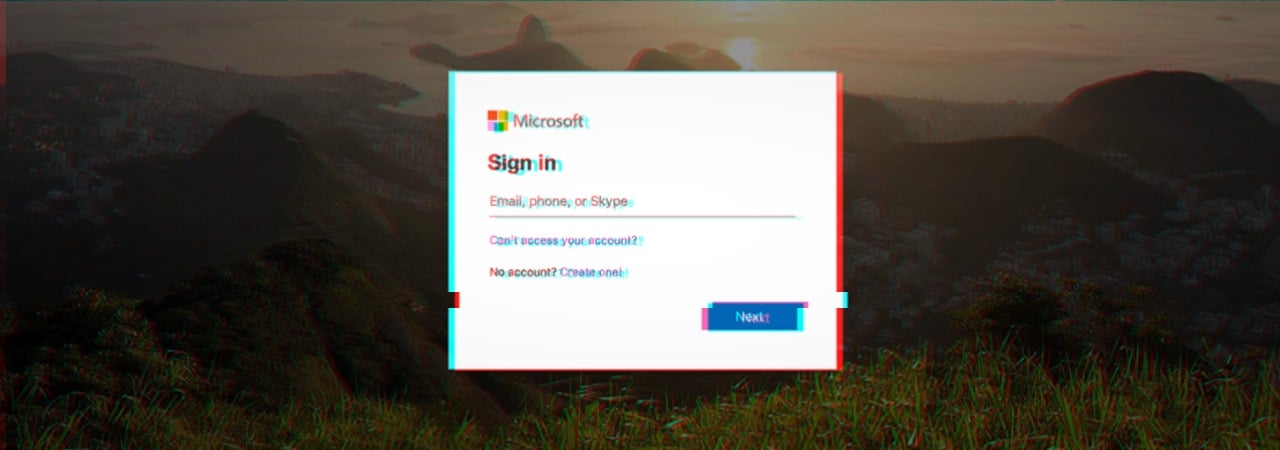
A new phishing campaign has been observed in the wild using captcha boxes to hide a fake Microsoft account login page from secure email gateways (SEGs).
Businesses use SEGs to protect against a wide variety of email-based attacks. They scan all messages, in or out, for malicious content and protect at least against malware and phishing threats.
Captcha blocks automated scanning
Captchas are challenge-based methods to determine if the user is human or a bot. Their purpose is to prevent abuse and are typically found on registration pages to prevent automated sign up action.
Ironically, the phishing campaign discovered by Cofense used this type of challenge to block automated URL analysis from processing the dangerous page.
"The SEG cannot proceed to and scan the malicious page, only the Captcha code site. This webpage doesn’t contain any malicious items, thus leading the SEG to mark it as safe and allow the user through." - Cofense
The attackers were after credentials for Microsoft accounts and created a page that mimics the original for selecting an account and logging in.
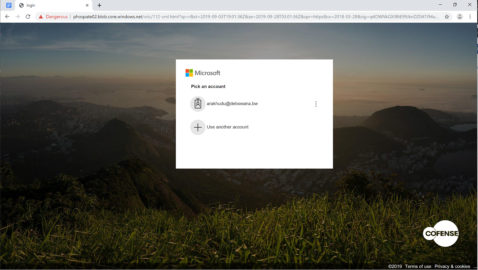
This is served after completing the human verification step. Needless to say that anything typed in the text fields is automatically sent to the attacker.
According to the researchers, the email delivering the phishing link is from a compromised account from 'avis.ne.jp' and pretends to be a notification for voicemail message.
A button promising to provide a preview of the alleged communication is embedded in the email; when clicked, it takes the victim to the page with the captcha code.
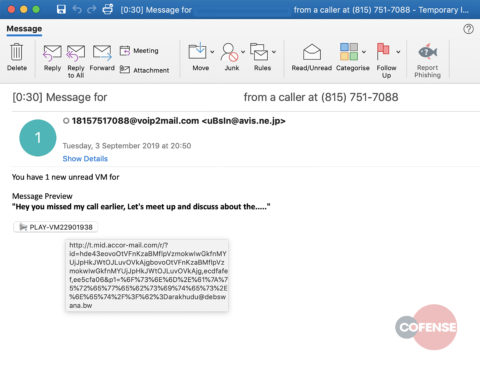
The researchers say that both the captcha and the phishing pages are hosted on the Microsoft infrastructure. As a result, they have legitimate top-level domains, which ensures no negative reaction from domain reputation databases, used by SEGs in their URL analysis process.
Ever creative cybercriminals find new ways to bypass security controls and exhibit social engineering tricks in their attempts to pass human inspection.
In past campaigns, fraudsters uses QR codes to redirect to phishing pages, a method that also flies under the radar of multiple security solutions
Another operation relied on email notifications about a Google Docs file being shared with the target. When users tried to open the document, they would see a fake 404 error and an instruction to download the file locally.
To make a different email-based scam more believable, threat actors used fake 2FA codes delivered via emails pretending to be from Instagram.

.jpg)
Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now