
Several countries have been targeted by a long-term campaign operated by financially motivated threat actors who used a backdoor and a remote access Trojan (RAT) malicious combo to take control of infected computers.
The two malicious payloads dubbed BalkanDoor and BalkanRAT by the ESET researchers who spotted them have been previously detected in the wild by the Croatian CERT in 2017 and, even earlier, by a Serbian security outfit in 2016.
However, ESET was the first to make the connection between them, after observing several quite significant overlaps in the entities targeted by their operators, as well as Tactics, Techniques, and Procedures (TTP) similarities.
Financially-motivated campaign
The malware cocktail is dropped on the victims' computers via malspam emails linking to malicious files. Once infected, the attackers can gain full control of the compromised hosts, either via command line with the help of the BalkanDoor payload or via a graphical interface with the help of BalkanRAT.
"This rather uncommon setup makes it possible for attackers to choose the most suitable method to instruct the computer to perform operations of their choice," adds ESET.
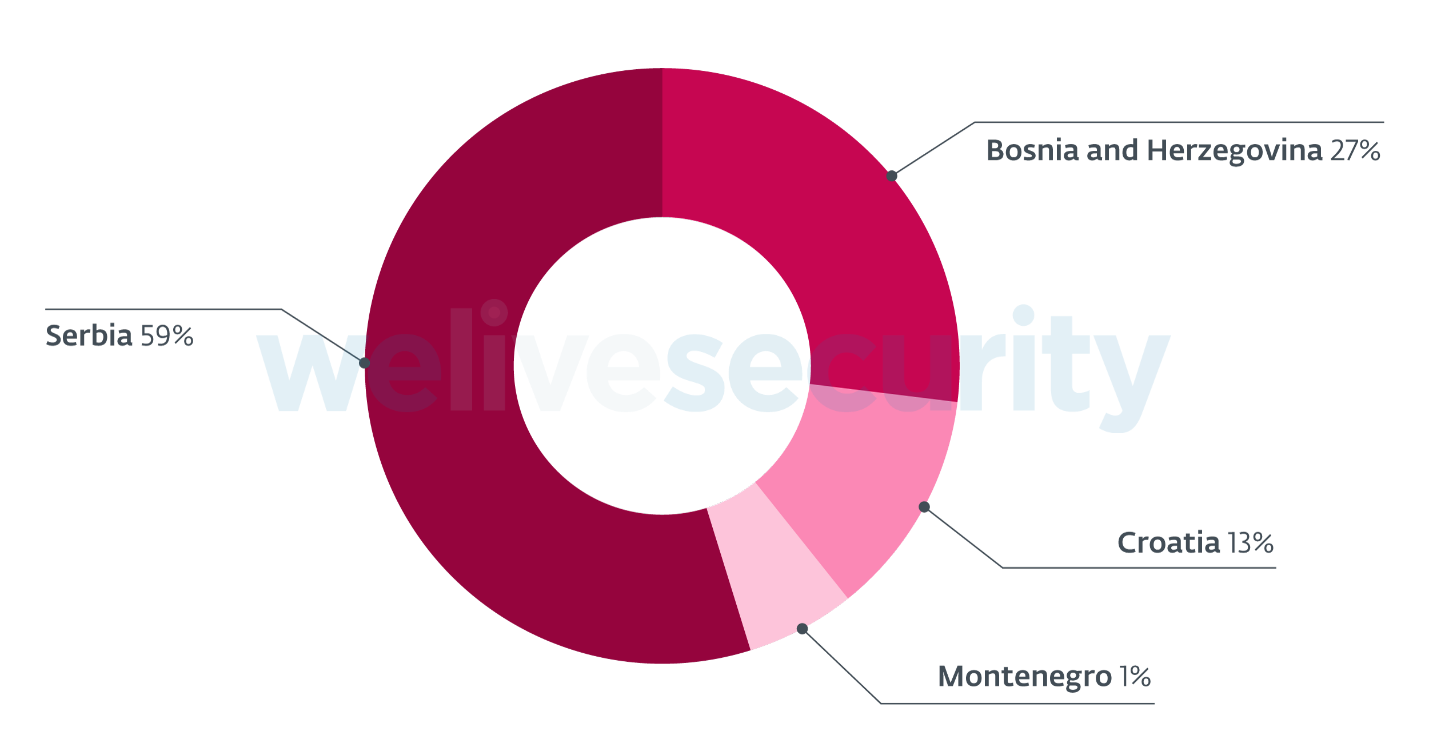
The hackers behind this campaign have been observed while attacking entities from Croatia, Serbia, Montenegro, and Bosnia and Herzegovina.
Also, they are financially motivated based on the obvious focus of the spam emails which delivered various types of tax document attachments and the fact that their targets all seem to be part of the organizations' financial departments.
The malspam emails delivered to the victims used domains designed to impersonate legitimate websites from the targets' countries to host their malicious payloads, with the domains ranging from tax administration and ministries of finance sites to ones that were supposedly hosting the country's chamber of commerce.
ESET found that this campaign has been active since at least 2016 based on internal telemetry data, while the most recent BalkanDoor and BalkanRAT samples have been detected in July.
While the BalkanDoor backdoor malware does not come with an exfiltration channel to send collected data to its masters, BalkanRAT was observed by ESET "dropping a tool that can list available smart cards, via the SCardListReadersA/ SCardConnectA API functions."
"Smart cards are usually issued by banks or governments for confirmation of the holder’s identity. If misused, smart cards can facilitate illegal/fraudulent activities, e.g. digitally signing a contract, validating a money transaction etc," explains ESET's report.
The two malicious payloads
Even though the BalkanDoor malware comes with limited functionality seeing that it supports a limited number of commands, the researchers have observed multiple variants since 2016, all of them featuring a different combo of capabilities which would allow them to create remote shells, to take screenshots, to unlock the victim's screen without needing a password, or to download more payloads on the infected.
The backdoor is dropped on the targets' systems via the malspam campaign (sometimes using decoy PDFs) which will drop the BalkanDoor payload and gain persistence with the help of a malicious script that will add new Registry keys and Startup entries.
Once it launches on the infected machines, the malware connects to one of several command and control (C2) centers stored within a hardcoded list and waits for commands from its masters. The attackers have the choice of controlling multiple compromised computers at once using INI files containing the list of machines supposed to run a specific set of commands.
The BalkanRAT remote access Trojan is a more capable piece of malware as ESET found, with the RAT dropping the Remote Utilities software on the compromised computers, a legitimate remote administration tool which will enable the attackers to remotely control their victims' machines.
To conceal the dropped remote admin tool and avoid being detected by the user, BalkanRAT "can add exceptions to the firewall, hide the RDS’s window and its tray icon, and hide the presence of related processes in the task manager."
This malware's core component allows its masters to perform several tasks on the victim's computer, from installing the BalkanRAT payload and injecting a userland rootkit to conceal the malicious processes it spawns to adding the firewall exceptions designed to help hide the remote admin tool.
"Since the tool BalkanRAT misuses is legitimate, it leverages the genuine Remote Utilities’ infrastructure for this communication (rutils.com, server.rutils.com); due to this, the communication may seem legitimate to the user – and to security products," adds ESET.

While the RAT will most times hide only the processes used to perform its tasks, the researchers have also observed it hiding processes spawned by the BalkanDoor backdoor, a fact which further reinforces the connection between the two malware strains.
The campaign that targeted the financial staff of organizations from Croatia, Serbia, Montenegro, and Bosnia and Herzegovina during the last three years was also seen targeting Ukrainian notaries, allowing the attackers to misuse the notaries' compromised computing systems to perform illegal operations in their name.
"Just as attackers may confirm a fraudulent transaction on behalf of a notary, they may perform a fraudulent transaction while impersonating a manager in a company’s financial department," concludes ESET.
A list of BalkanDoor and BalkanRAT malware sample SHA-1 hashes are provided by the researchers at the end of their report, together with C2 server domains used in this campaign and MITRE ATT&CK techniques matrices for both malware strains.

.jpg)
Comments
vvlada - 4 years ago
We was writing about this back in may 2016 (in Serbian): https://www.it-klinika.rs/blog/prvi-phishing-na-srpskom.