
A new vulnerability has been found in the Camera apps for millions, if not hundreds of millions, of Android devices that could allow other apps to record video, take pictures, and extract GPS data from media without having the required permissions.
Android apps expose various intents, or functions such as the ability to take a picture, that can be executed by other apps on the device. In order to execute an exposed intent, another app has to have the needed permissions.
In a coordinated disclosure with Google and Samsung, researchers from Checkmarx disclosed today a new vulnerability that allows apps to take pictures, record videos, or get a device's location even if they do not have permissions to do so.
This vulnerability, known as CVE-2019-2234, is known to affect the Google Camera and Samsung Camera apps if they have not been updated since before July 2019.
Bypassing permissions to take pictures and record videos
After analyzing the Google Pixel's Camera app, Checkmarx researchers discovered numerous intents that could be combined to manipulate the device's camera in order to take pictures and record video.
Normally, an app needs to have the android.permission.CAMERA, android.permission.RECORD_AUDIO, android.permission.ACCESS_FINE_LOCATION, and android.permission.ACCESS_COARSE_LOCATION permissions in order to record video, take pictures, or access a device's location.
Checkmarx discovered that apps that have the 'Storage' permission, which gives the app access to the device's entire SD card and the media stored on it, also gives an app the ability to use the Camera app's exposed intents without the permissions listed above.
"A malicious app running on an Android smartphone that can read the SD card, not only has access to past photos and videos, but with this new attack methodology, can be directed to initiate (take) new photos and videos at will. And it doesn’t stop there. Since GPS metadata is usually embedded into the photos, the attacker can take advantage of this fact to also locate the user by taking a photo or video and parsing the proper EXIF data. "
This is problematic because many apps regularly ask for the Storage permission, such as car racing games, streaming services, and even weather apps.
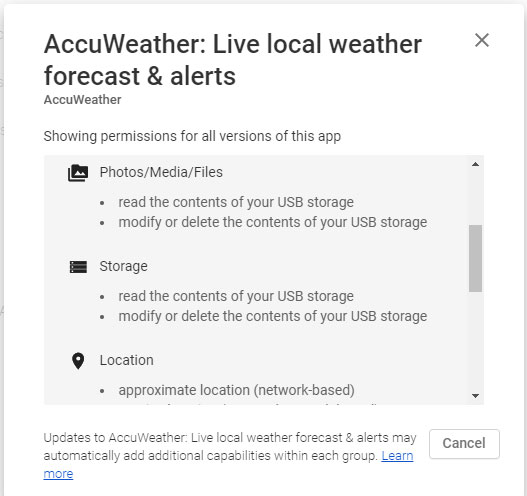
According to Checkmarx's report, the Storage permissions is the most common requested permission that they have observed.
"There are a large number of applications, with legitimate use-cases, that request access to this storage, yet have no special interest in photos or videos. In fact, it’s one of the most common requested permissions observed."
Even worse, this allowed the researchers to create a proof-of-concept app that pretends to be a weather app, but quietly sends a picture, video, and phone call recordings back to a demo command & control server under the researcher's control as shown below.
As you can see this vulnerability is quite dangerous as it could allow apps that normally do not have permission, to:
- Take pictures and videos even if the phone is locked or the screen is off.
- Pull GPS location data from stored photos.
- Listen in on two-way conversations even when recording video and taking pictures. Talk about sextortion potential!
- Silence the camera shutter so that victim's cant hear when pictures are taken.
- Transfer historical videos and photos stored on the SD card.
Google Camera app fixed in July 2019
Checkmarx disclosed this vulnerability to Google on July 4th, 2019 and by July 23rd, Google had elevated this vulnerability to a 'High' classification.
On August 1st, it Google confirmed the researcher's suspicions that this vulnerability affected Camera apps for other Android mobile device vendors and issued CVE-2019-2234 for the vulnerability.
Later in August it was determined that Samsung's Camera app was affected too and both vendors approved the publication of this vulnerability.
According to Google, this vulnerability in the Camera app was fixed in July 2019 via a Google Play Store update and a patch was issued to other vendors.
“We appreciate Checkmarx bringing this to our attention and working with Google and Android partners to coordinate disclosure. The issue was addressed on impacted Google devices via a Play Store update to the Google Camera Application in July 2019. A patch has also been made available to all partners.”
All users are strongly advised to upgrade to the latest version of Android and make sure you are using the latest Camera app for your device.


Comments
DanEdens - 4 years ago
Really amazing app called "Tasker" just got a recent update that allows you to disable other apps from using the camera entirely if anyone is interested. You can create a widget to toggle it or try various other methods.