
The point-of-sale (POS) systems of North American fuel dispenser merchants are under an increased and ongoing threat of being targeted by an attack coordinated by cybercrime groups according to a security alert published by VISA.
Three attacks that targeted organizations in this type of attack with the end goal of scraping payment card data were observed during the summer of 2019, according to the Visa Payment Fraud Disruption (PFD).
This alert follows a previous warning from November that also mentions such merchants being an increasingly attractive target for threat groups "due to the lack of secure acceptance technology, (e.g. EMV Chip, Point-to-Point Encryption, Tokenization, etc.) and non-compliance with PCI DSS."
Attacks against fuel dispenser merchants
PFD says that in the first incident it identified, unknown attackers were able to compromise their target using a phishing email that allowed them to infect one of the systems on the network with a Remote Access Trojan (RAT).
This provided them with direct network access, making it possible to obtain credentials with enough permissions to move laterally throughout the network and compromise the company's POS system as "there was also a lack of network segmentation between the Cardholder Data Environment (CDE) and corporate network."
The last stage of the attack saw the actors deploying a RAM scraper that helped them collect and exfiltrate customer payment card data.
During the second and third incidents, PFD states that the threat actors used malicious tools and TTPs (Tactics, Techniques and Procedures) attributable to the financially-motivated FIN8 cybercrime group.
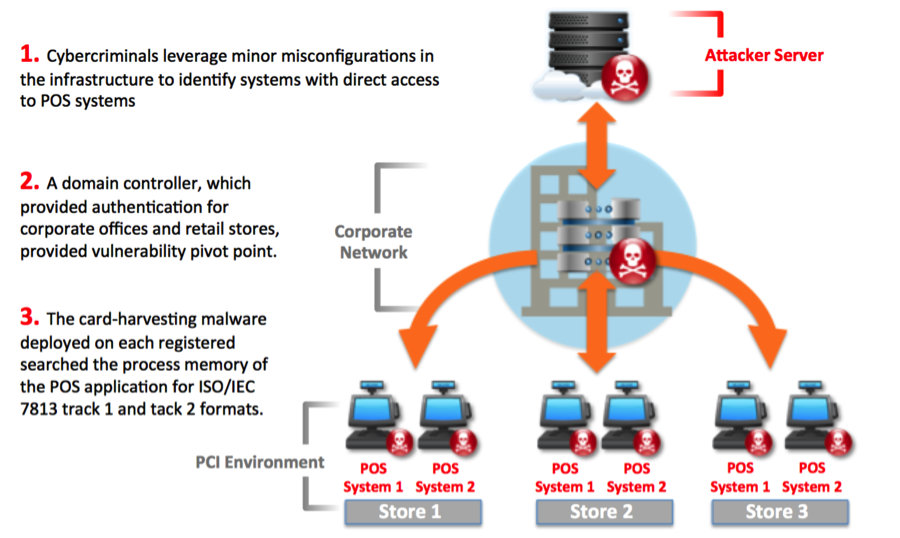
As part of the second attack, the attackers used an unknown vector to gain network access and infect the POS environment with a RAM scraper malicious payload that specifically targeted magnetic stripe transactions.
"The malware used in the attack also created a temporary output file, wmsetup.tmp, which was used to house the scraped payment data," VISA says. "This file was previously identified in attacks attributed to FIN8 and FIN8-associated malware."
PFD also discovered malware samples known to be used by FIN8 in previous campaigns in a third incident targeting a compromised
North American hospitality merchant.
However, they also spotted new malware based on the RM3 variant of Ursnif (aka Gozi/Gozi-ISFB), a modular banking malware usually delivered via spear-phishing attacks and exploit kits.
"While the malware used in this attack was not identified in the attacks against the fuel dispenser merchants, it is possible FIN8 will use this malware in future operations targeting fuel dispenser merchants," VISA adds.
Actors have been following mag stripes since 2015 when EMV rollout began. There’s evidence of targeting of gas stations in prior versions of AbaddonPOS. https://t.co/3KEMJAaYH1 pic.twitter.com/hBwepYsIC8
— PaulM (@pmelson) December 12, 2019
Magnetic stripe POS systems under increased threat
Based on the recent attacks that compromised POS systems at fuel dispenser merchants detected by PFD, threat groups have them on the short list of attractive targets.
"It is important to note that this attack vector differs significantly from skimming at fuel pumps, as the targeting of POS systems requires the threat actors to access the merchant’s internal network, and takes more technical prowess than skimming attacks," VISA PFD says.
"Fuel dispenser merchants should take note of this activity and deploy devices that support chip wherever possible, as this will significantly lower the likelihood of these attacks."
VISA provides merchants and acquirers with a series of measures designed to mitigate this type of threats:
• Secure remote access with strong passwords, ensure only the necessary individuals have permission for remote access, disable remote access when not in use, and use two-factor authentication for remote sessions.
• Enable EMV technologies for secure in-person payments (chip, contactless, mobile and QRcode).
• Provide each Admin user with their own user credentials. User accounts should also only be provided with the permissions vital to job responsibilities.
• Turn on heuristics (behavioral analysis) on anti-malware to search for suspicious behavior, and update anti-malware applications.
• Monitor network traffic for suspicious connections, and log system and network events.
• Implement Network Segmentation, where possible, to prevent the spread of malicious software and limit an attacker’s foothold.
• Maintain a patch management program and update all software and hardware firmware to most current release to limit the attack surface for zero-day vulnerabilities.
• In the event of a confirmed or suspected breach, refer to Visa’s What to do if Compromised (WTDIC), published in October 2019.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now