Attackers have targeted precision companies in Italy with phishing that is difficult to spot. The final payload is a fileless trojan that harvests credentials.
The campaign used a legitimate-looking Microsoft Excel spreadsheet embedded with exploit code that moves silently to infect the computer.
Devil is in the details
The cybercriminals made all efforts to craft an email the victim company would typically receive from a customer. From body to sender's address and the document attached, everything was spot on.
The spearphishing email was sent on October 26 to individuals in the sales department of the precision company. It had attached an Excel spreadsheet containing a list of spare parts identified with real catalog codes, quantities, and shipping addresses.
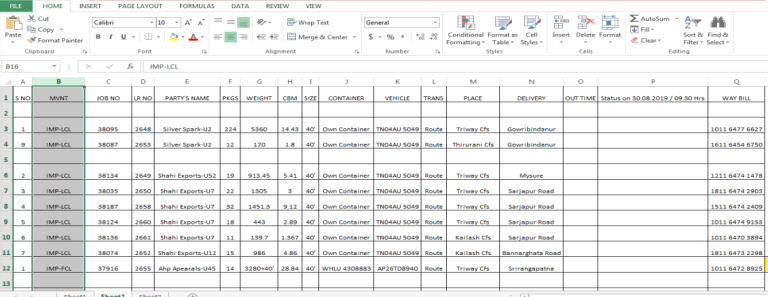
Such emails are not uncommon for precision companies. In this case, the fake customer asked for an estimated cost for the order. Nothing unusual.
The attention for details goes beyond this, though, as the attacker also impersonated an organization likely to actually need the spare parts listed in the spreadsheet.
Analyzing this spearphishing attack, security researcher Marco Ramilli, founder of the Yoroi cyber defense company, noticed that the email sender's address was 'steel@vardhman.com.'
The Vardhman Group of companies is based in India and is a large textile producer. Its activity profile fits that of the clientele a precision engineering company would have.
The exploit
Unlike the run-of-the-mill methods of infection that involve a Microsoft Office document, the cybercriminals behind this campaign did not embed malicious macro code in the Excel file, which would call for user interaction.
Instead, they opted for a stealthier variant: an exploit for a remote code execution security bug that would run automatically run code on the victim computer without user intervention as soon as the document was opened.
The vulnerability is an old one (CVE-2017-11882) in the Equation Editor component of Microsoft Office software, responsible for inserting or editing OLE objects in documents. It was fixed two years ago in Microsoft Office software but exploits are publicly available along with code to generate them.
Password-stealing payload
Ramilli observed that the exploit delivered the portable executable (PE) file 'educrety.exe' from an external domain and ran in the computer memory. This way, the malware would be more difficult to detect because it would not be stored on disk.
The executable is currently detected by 45 out of 67 antivirus engines available on the VirusTotal scanning platform and was also seen under the names 'prestezza.exe' and 'cardsharper.exe.'
The researcher found that the PE was an info stealer that searched for passwords and access tokens in the system registry and sent them to the command and control (C2) server. The malware has a large list of locations to check, including registry keys for SSH clients (PuTTY, KiTTY) and email clients (IncrediMail, PostBox, Outlook).
Data collected from the victim computer is pushed to a command and control server located at 'corpcougar.com.' Coincidentally or not, that server also hosts a phishing kit for Microsoft services. The fake login page imitates the original pretty well but a closer look at the links at the bottom reveals its true colors.

Ramilli believes that these spearphishing attacks are the work of a threat actor called 'SWEED,' known for using info-stealing malware like LokiBot, Agent Tesla, and Formbook, previously documented by Cisco Talos researchers.
"I did find many similarities including original attack vectors, used Microsoft Office Exploit, implementation of LokiBot and victims type to “SWEED” so that I believe this attack could also be attributed to the same threat actor."
In his blog post, the researcher provides indicators of compromise related to these spearphishing attacks against precision engineering companies in Italy.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now