By Talal Haj Bakry and Tommy Mysk
UPDATE (MAY 5, 2020): TikTok rolled updates for iOS and Android in May that fixed this vulnerability.
If you enjoyed this work, you can support us by checking out our apps:
Videos
- Video manipulation of popular TikTok accounts
- Demonstration of posting spam on WHO’s feed
Summary
The TikTok app uses insecure HTTP to download media content. Like all social media apps with a large userbase, TikTok relies on Content Delivery Networks (CDNs) to distribute their massive data geographically. TikTok’s CDN chooses to transfer videos and other media data over HTTP. While this improves the performance of data transfer, it puts user privacy at risk. HTTP traffic can be easily tracked, and even altered by malicious actors. This article explains how an attacker can switch videos published by TikTok users with different ones, including those from verified accounts.
Introduction
Modern apps are expected to preserve the privacy of their users and the integrity of the information they display to them. Apps which use unencrypted HTTP for data transfer cannot guarantee that the data they receive wasn’t monitored or altered. This is why Apple introduced App Transport Security in iOS 9, to require all HTTP connections to use encrypted HTTPS. Google has also changed the default network security configuration in Android Pie to block all plaintext HTTP traffic.
Apple and Google still provide a way for developers to opt-out of HTTPS for backwards-compatibility. However, this should be the exception rather than the rule, and most apps have made the transition to HTTPS. At the time of writing, TikTok for iOS (Version 15.5.6) and TikTok for Android (Version 15.7.4) still use unencrypted HTTP to connect to the TikTok CDN.
After a short session of capturing and analyzing network traffic from the TikTok app with Wireshark, it is hard to miss the large amounts of data transferred over HTTP. If you inspect the network packets closer, you would clearly spot data of videos and images being transferred in the clear and unencrypted.
Consequently, TikTok inherits all of the known and well-documented HTTP vulnerabilities. Any router between the TikTok app and TikTok’s CDNs can easily list all the videos that a user has downloaded and watched, exposing their watch history. Public Wifi operators, Internet Service Providers, and intelligence agencies can collect this data without much effort.
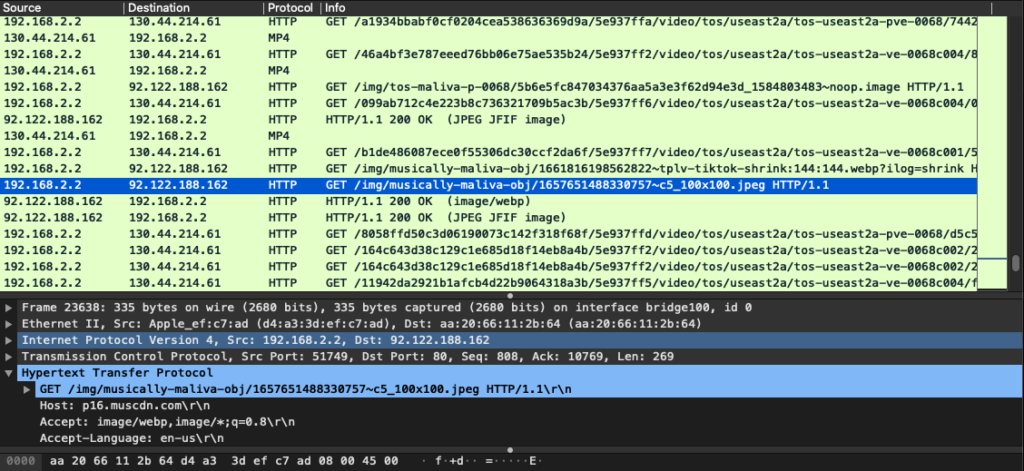
Figure 1 illustrates the network traffic as captured by Wireshark.
TikTok transports the following content via HTTP:
- Videos: all videos that the app shows
- Profile photos: the profile photos of TikTok accounts
- Video still images: the preview image of a video that is displayed while the video is being downloaded
The captured data shows that videos are downloaded from the following domain names:
- http://v19.muscdn.com
- http://v21.muscdn.com
- http://v34.muscdn.com
In addition, profile photos and still images are downloaded from http://p16.muscdn.com.
All the content types listed above are prone to tracking. For example, watch history can be created by capturing network traffic downloaded from http://v34.muscdn.com.
Moreover, a man-in-the-middle attack can alter the downloaded content. For example, swapping profile photos of accounts with forged photos. However, this is not as critical as swapping videos. While a picture is worth a thousand words, a video is certainly worth more. Thus, the attacker can convey more fake facts in a spam video swapped with a video that belongs to a celebrity or a trusted account.
The circulation of misleading and fake videos in a popular platform such as TikTok poses huge risks. That encouraged us to stage a man-in-the-middle attack to swap videos and demonstrate the results. The following section delves deeper into the technical details of our work.
Methodology
We prepared a collection of forged videos and hosted them on a server that mimics the behavior of TikTok CDN servers, namely v34.muscdn.com. To make it simple, we only built a scenario that swaps videos. We kept profile photos intact, although they can be similarly altered. We only mimicked the behavior of one video server. This shows a nice mix of fake and real videos and gives users a sense of credibility.
To get the TikTok app to show our forged videos, we need to direct the app to our fake server. Because our fake server impersonates TikTok servers, the app cannot tell that it is communicating with a fake server. Thus, it will blindly consume any content downloaded from it.
The trick to direct the app to our fake server is simple; it merely includes writing a DNS record for v34.muscdn.com that maps the domain name to the IP address of our fake server.
This can be achieved by actors who have direct access to the routers that users are connected to. First, a record mapping the domain name v34.muscdn.com to a fake server has to be added to a DNS server. Second, the infected routers have to be configured to use that corrupt DNS server. Now, when the TikTok app tries to look up the IP address of v34.muscdn.com, the corrupt DNS server returns the IP address of the fake server. Then, the app will send all subsequent calls to the fake server that is impersonating TikTok’s v34.muscdn.com.
Those actions can be performed by any of the following actors:
- Wifi Operators: operators of public wifi networks can configure the router to use a corrupt DNS server
- VPN providers: a malicious VPN provider can configure a corrupt DNS server for its users
- Internet Service Providers (ISPs): Internet Service Providers such as telecom companies have full access to the internet connections of their customers. They can configure a corrupt DNS server for their customers to swap content or track user activities
- Governments and intelligence agencies: in some countries governments and intelligence agencies can force ISPs to install tools that track or alter data
If you distrust any of these actors, then what you watch on TikTok may have been altered. This also applies to any internet service that uses HTTP.
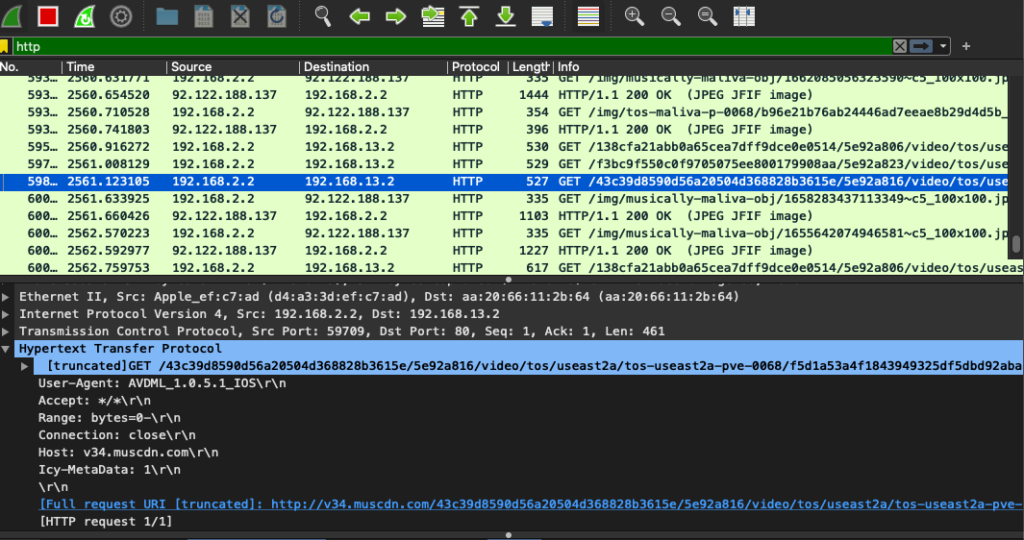
Figure 2 illustrates the HTTP network traffic directed to the fake server. The highlighted row shows a video request sent by the app to the destination IP 192.168.13.2, which is the IP address of our fake server. The fake server then picks a forged video and returns it to the app which, in turn, plays the forged video to the user as shown in the demo video. Note that only video requests are directed to the fake server. Requests to download profile photos and still images are directed to the real servers, i.e. we left them unchanged as per our scenario. In contrast, Figure 1 shows a similar video request sent to the real TikTok server with the IP 92.122.188.162.

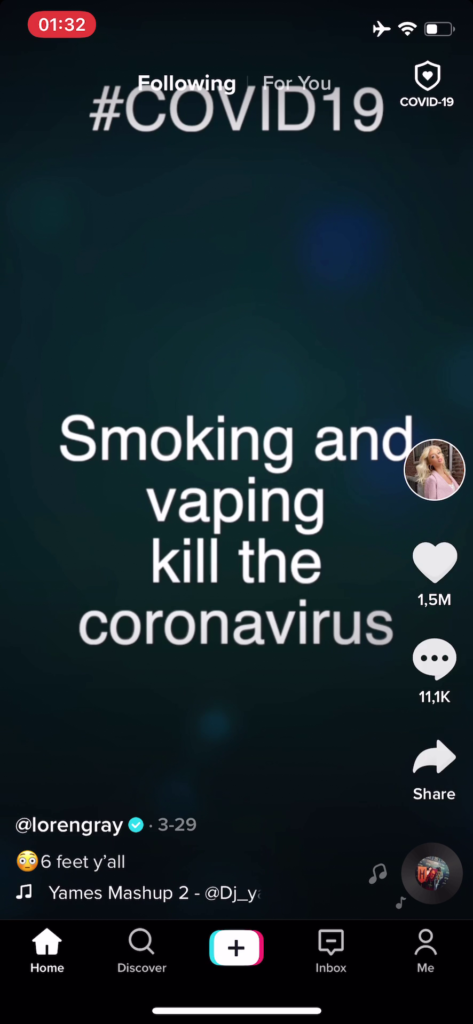
The forged videos we created present misleading information about COVID-19. This illustrates a potential source of disseminating misinformation and false facts about a contemporary critical topic.
As shown in the demo video and Figures 3-6, the forged videos appeared on popular and verified accounts like @who, @britishredcross, @americanredcross, @tiktok, @lorengray, and @dalia. (@lorengray has over 42 million followers and 2.3 billion likes)

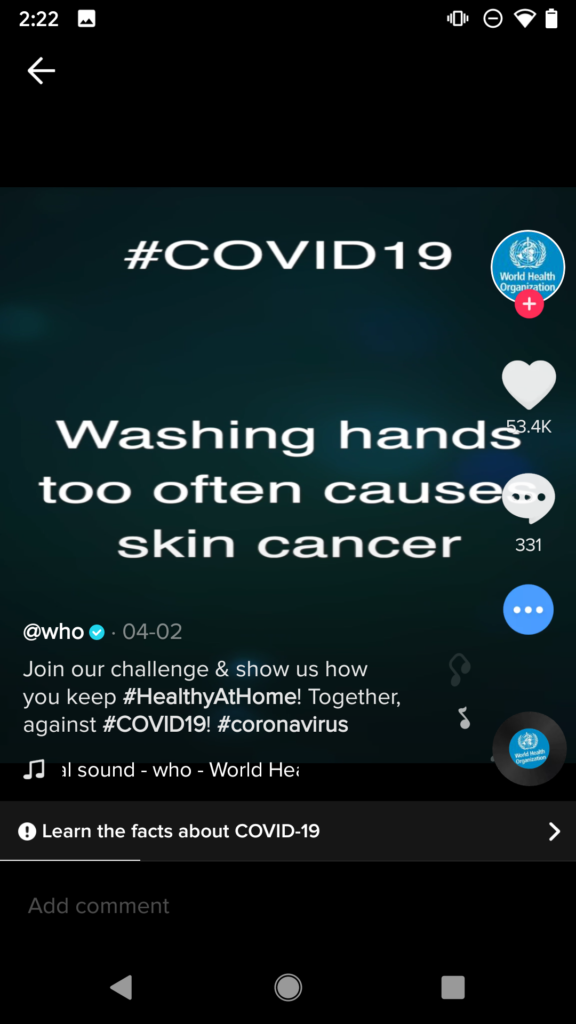
To recap, only users connected to my home router can see this malicious content. However, if a popular DNS server was hacked to include a corrupt DNS record as we showed earlier, misleading information, fake news, or abusive videos would be viewed on a large scale, and this is not completely impossible.
Conclusion
The use of HTTP to transfer sensitive data has not gone extinct yet, unfortunately. As demonstrated, HTTP opens the door for server impersonation and data manipulation. We successfully intercepted TikTok traffic and fooled the app to show our own videos as if they were published by popular and verified accounts. This makes a perfect tool for those who relentlessly try to pollute the internet with misleading facts.
TikTok, a social networking giant with around 800 million monthly active users, must adhere to industry standards in terms of data privacy and protection.