
Image: C Drying
The Evil Corp gang hacked into dozens of US newspaper websites owned by the same company to infect the employees of over 30 major US private firms using fake software update alerts displayed by the malicious SocGholish JavaScript-based framework.
The employees' computers were used as a stepping point into their companies' enterprise networks as part of what looks like a series of targeted drive-by attacks.
Symantec confirmed that "dozens of U.S. newspaper websites owned by the same parent company have been compromised by SocGholish injected code."
Some of the organizations targeted by WastedLocker could have been compromised when an employee browsed the news on one of its websites," Symantec says.
Researchers with Symantec's Threat Intelligence team who discovered these attacks say that the company who owns the compromised news sites was alerted and the malicious code was removed.
UPDATE on our #WastedLocker investigation. Dozens of US newspaper websites owned by the same parent company were compromised by attackers in order to infect potential targets. Symantec has notified the company and it has now removed the malicious code. https://t.co/28E9iNr0o3
— Threat Intelligence (@threatintel) July 1, 2020
Symantec previously said in a report published on June 26 that it blocked the Evil Corp gang from deploying WastedLocker ransomware payloads in attacks against 31 large private companies, including 30 US corporations, including "11 listed companies, eight of which are Fortune 500 companies."
"At least 31 customer organizations have been attacked, meaning the total number of attacks may be much higher," researchers at Symantec explained.
"The attackers had breached the networks of targeted organizations and were in the process of laying the groundwork for staging ransomware attacks."
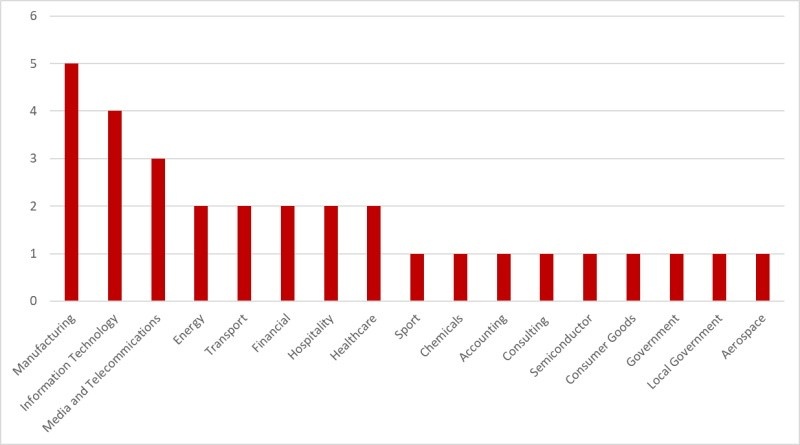
Evil Corp directed the attacks at a large array of industry sectors, focusing on manufacturing (five of the 31 targets), with information technology (four orgs) and telecommunications (three entities) also included in the top three most targeted sectors.
"Had the attackers not been disrupted, successful attacks could have led to millions in damages, downtime, and a possible domino effect on supply chains," Symantec added.
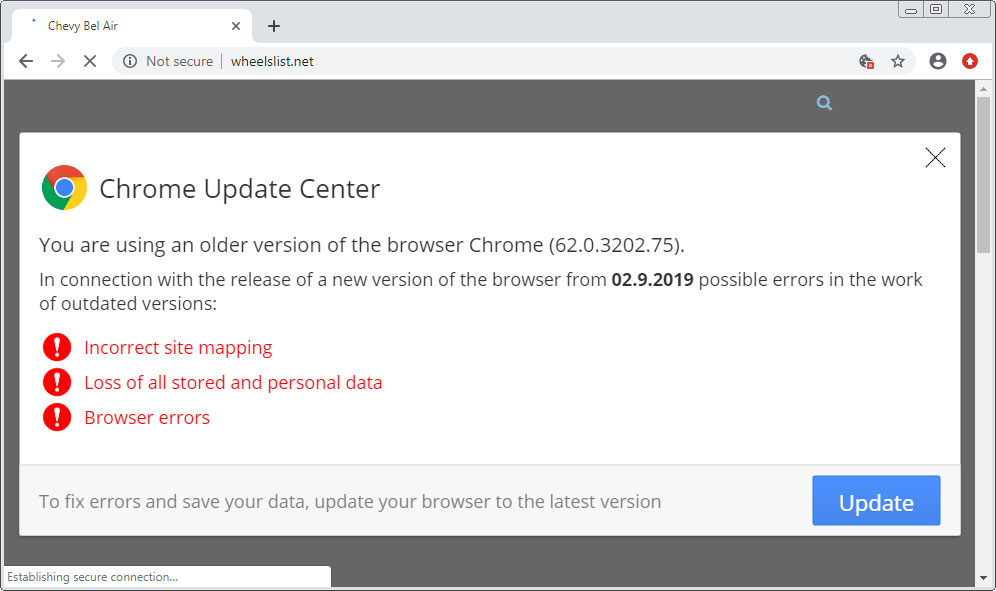
As the Symantec researchers explained, Evil Corp's attacks started with the SocGholish framework being used to infect targets who visited over 150 hacked websites (dozens of them being US newspaper websites as mentioned in today's update).
This is done by displaying fake software update alerts that deliver malware payloads onto the targets' devices in the form of fake program updates.
After a company's employee got infected, the hackers used the Cobalt Strike threat emulation software and several living-off-the-land tools to "steal credentials, escalate privileges, and move across the network" with the end goal of encrypting computers with the WastedLocker ransomware.
Before deploying the ransomware, they also disabled Windows Defender across the victims' entire network using PowerShell scripts and legitimate tools.
If the WastedLocker payloads are successfully deployed using the Windows Sysinternals PsExec tool, it encrypts the victims' data and deletes Windows shadow volumes to wipe backups and file snapshots to make recovery impossible.
The Evil Corp cybercrime group (aka the Dridex gang) is active since at least 2007 and it distributed the Dridex malware toolkit later used to spread other threat actors' malware payloads.
They were also involved in the distribution of Locky ransomware, as well as their own ransomware strain known as BitPaymer until 2019.
Two of its members were indicted by the US Department of Justice in December 2019 for involvement in international bank fraud and computer hacking schemes that resulted in the theft of more than $100 million.
Since then, Evil Corp refreshed their tactics and are now again in involved in the ransomware "business," deploying their new WastedLocker ransomware in targeted attacks against businesses and asking for ransoms of millions of dollars.


Comments
DyingCrow - 3 years ago
All the knowledge and all the work they put into all this stuff, and have a fake update notification that looks like something a 5 year old would write, most likely Google translated? lul
EmanuelJacobsson - 3 years ago
Humans are flawed beings, we arent perfect, even the best and smartest of us doesnt know everything-