
Dozens of cybercriminal gangs are publishing fake ads on popular online marketplaces to lure interested users to fraudulent merchant sites or to phishing pages that steal payment data.
Some of the brands abused through this scam are extremely popular in Europe and include LeBonCoin, Allegro, OLX, Sbazar, FAN Courier, Lalafo, Kufar and DHL.
Scam expanding to Europe
At least 40 cybercriminal gangs are using a scam-as-a-service that relies on Telegram bots to provide pages that impersonate popular classifieds, marketplaces, and delivery services.
Security researchers at Group-IB through the company's digital risk protection in Amsterdam first spotted the scam in Russia, in the summer of 2019. They named it Classiscam and observed it grow from 280 scam pages to about 3,000 in less than a year.
Since its discovery, the scheme expanded to post-Soviet and European countries like Bulgaria, France, the Czech Republic, Poland, and Romania.
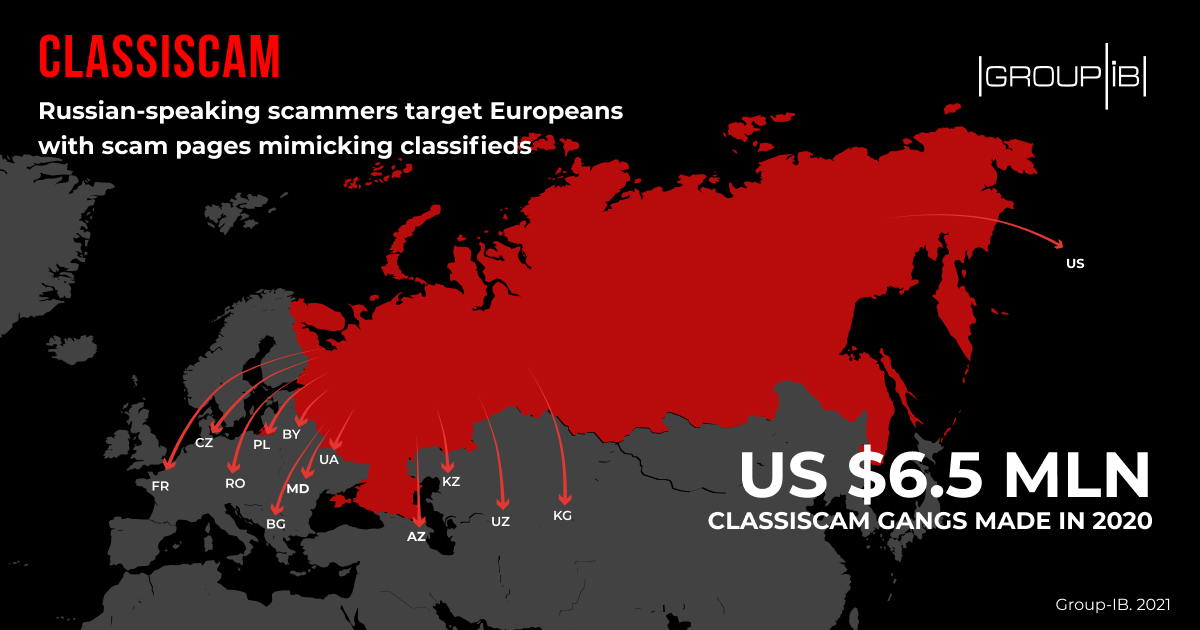
At least 40 gangs are running Classiscam, 20 of them being Russian, the most profitable ones making more than $500,000 every month. Group-IB calculated that the gangs operating in European countries make an average monthly profit of $61,000. It is estimated that the scammers made more than $6.5 million in 2020.
The scammers publish ads on popular marketplaces and classifieds claiming to offer various products (cameras, game consoles, laptops, smartphones) at low prices.
When someone interested in the deal contacts them, they move the conversation to a third-party messaging service. Group-IB says that the scammers use local phone numbers when speaking with the victim.
"Evildoers ask victims to provide their contact information to allegedly arrange a delivery. The scammer then sends the buyer an URL to either a fake popular courier service website or a scam website mimicking a classified or a marketplace with a payment form, which turns out to be a scam page. As a result, the fraudster obtains payment data or withdraws money through a fake merchant website" - Group-IB
It's important to note that the scammers can pose as both sellers and buyers. When pretending to be a customer, they send a fake payment form obtained from a Telegram bot that impersonates a marketplace. The seller then gets a fake form asking for card details in order to receive the alleged payment.
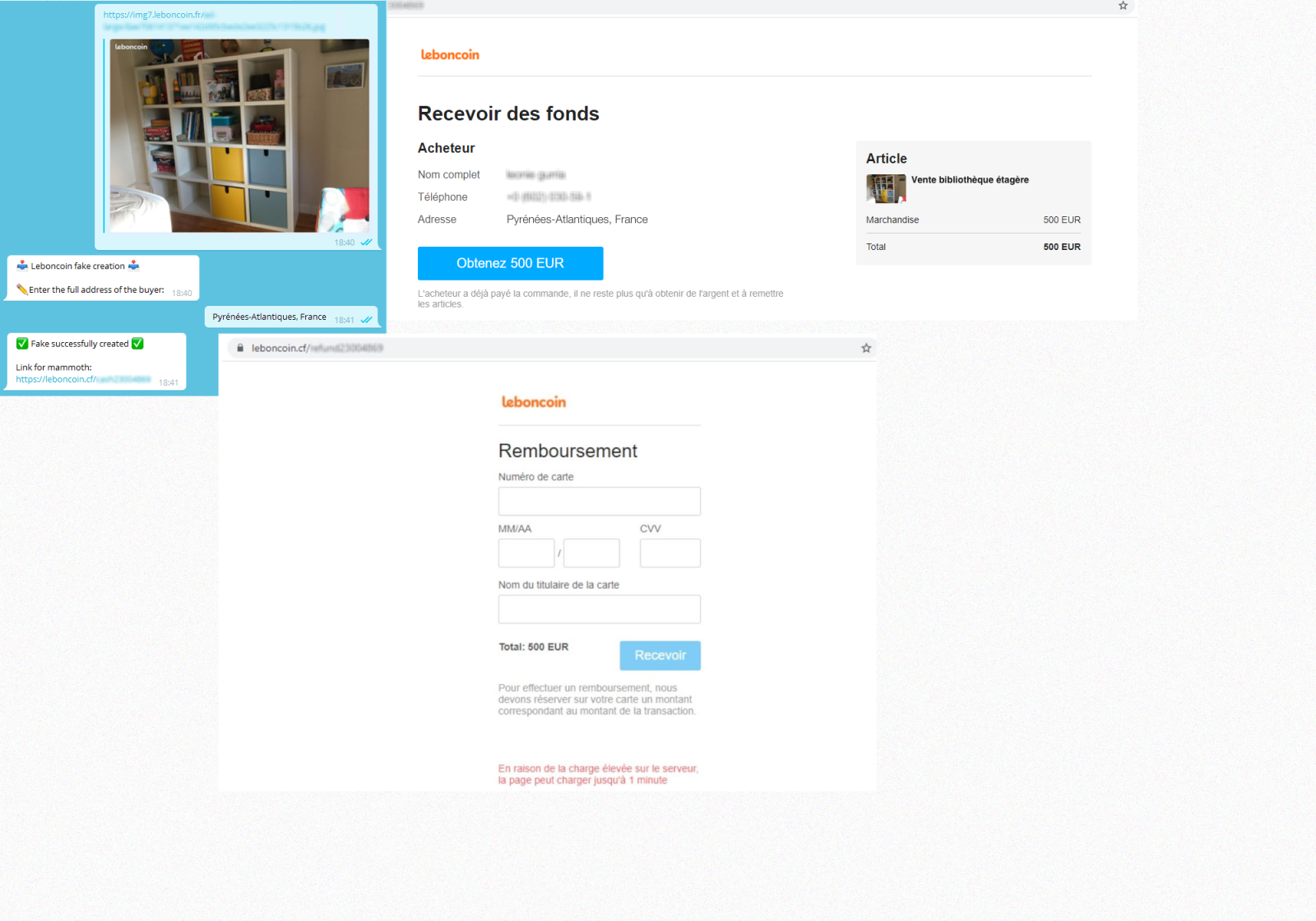
According to Group-IB, Classiscam does not require technical knowledge as the Telegram bots provide a complete phishing kit. The scammer just needs to send the chatbot a link with the bait product.
The researchers say that there are more than 10 types of Telegram bots for brands in various countries. Operators also provide scripts that help scammers beginners log into foreign sites and talk to victims in their local language.
Splitting the money
By observing the Telegram bots, the researchers were able to observe the details of the deals made by the scammers. They found that admins take between 20% and 30% of the stolen money while affiliates that carry out the scam take the rest.
The scam sometimes involves callers that pretend to be customer support specialists. They get the smallest cut, up to 10% of the stolen money.
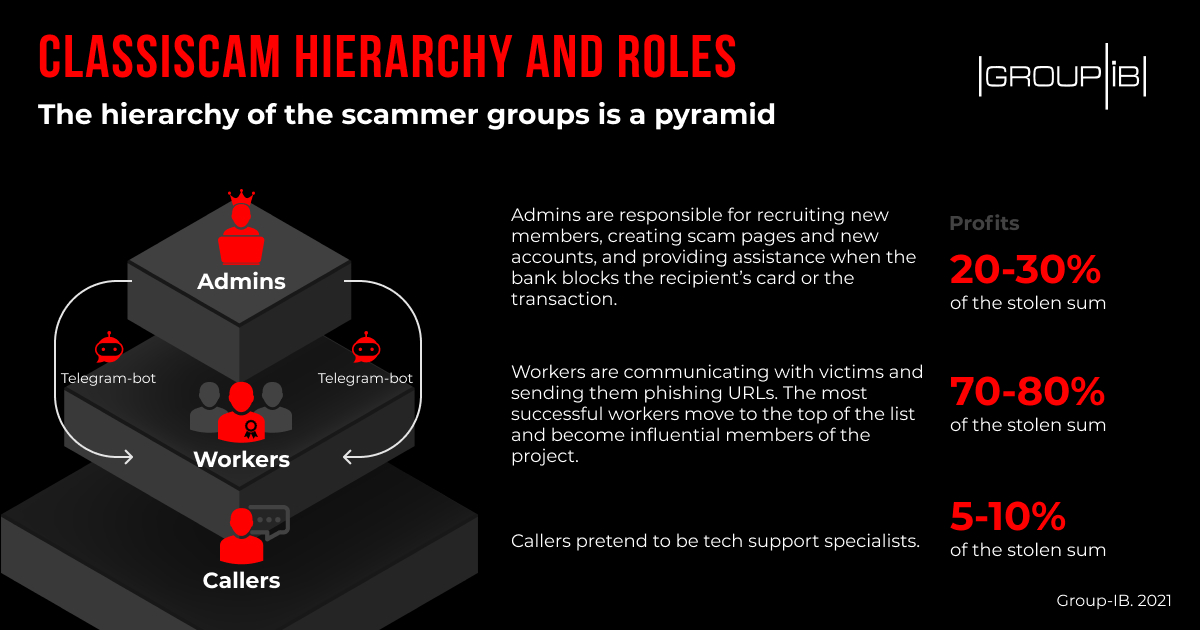
By the end of 2020, Classiscam engaged more than 5,000 scammers.
Keep safe
Group-IB tried to contact directly all of the brands abused by the Classiscam phishing operations but despite the size of the scam there was no reply, Dmitriy Tiunkin, Head of Group-IB Digital Risk Protection Department, Europe, told BleepingComputer.
"We always do our best to conduct proper outreach and hope that our findings have been well received and will be taken into account by the affected companies in mitigating the negative impact of Classicam" - Dmitriy Tiunkin
The researcher also told us that they are not aware of any law enforcement investigation into these thefts in Europe or the U.S. This may be explained by the fact that Classiscam has just started to expand to these regions.
Russian authorities, however, are monitoring the fraud and have already arrested scammers that posted fake ads [1, 2, 3].
To protect against Classiscam and fraud attempts, Group-IB makes the following recommendation to users:
- check URLs for payment details before providing the information, especially if the link is received through a messaging application
- keep the conversation on the official platform that intermediates the transaction so that it can serve as evidence in case of a fraud attempt
- do not agree to deals that involve a prepaid transaction; pay only after you get the goods
- be wary of large discounts and unbelievably low prices as they could act as bait for a phishing page


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now