
New details have emerged on the activity of the infamous Fxmsp hacker that last year was advertising access to the networks of three cybersecurity vendors.
Researchers tracking Fxmsp’s ventures on underground forums counted the network intrusions associated with this actor and revealed the presumed identity of the attacker.
Worldwide hacking activity
Fxmsp became widely known outside hacker forums about a year ago when cybersecurity boutique Advanced Intelligence (AdvIntel) published a series of reports on the actor’s attempts to close a $300,000 deal for selling access to networks belonging to Symantec, Trend Micro, and McAfee.
The actor and their accomplice slipped under the public radar soon after getting too much media attention, likely continuing activity over private messages.
Researchers at Group-IB examined Fxmsp’s exposure in the public areas of the forums where they were advertising their business, assessing that the actor breached networks of at least 135 companies in 44 countries.
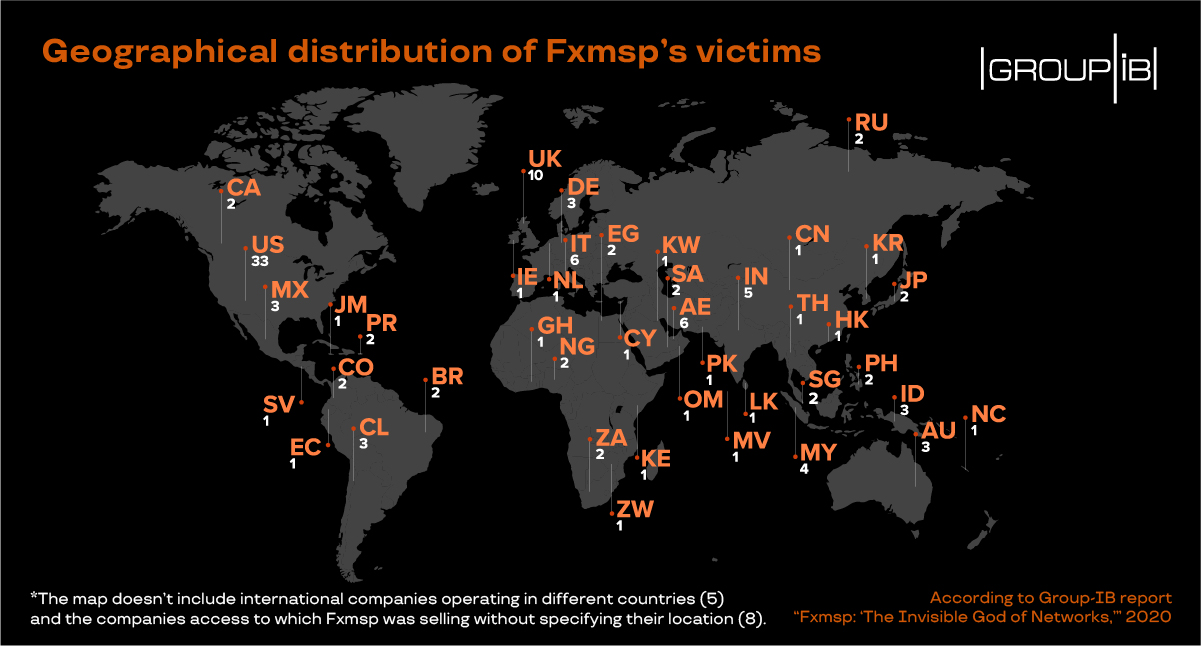
Among the targets are small and medium-sized enterprises (SME), government organizations, banks, and Fortune 500 companies. Group-IB’s conservative estimate is that in 3+ years (since 2016) Fxmsp made at least $1.5 million from selling network access.
In May 2019, AdvIntel assessed with high confidence that Fxmsp is a credible threat “with a history of selling verifiable corporate breaches returning them profit close to $1,000,000.”
This is not all the money, though, because transactions for access to 20% of the companies compromised were carried out in private and did not come with a public price tag.
Fxmsp stopped all their public activity in late 2019, Group-IB says, but not before advertising access to a power company in Europe that suffered a ransomware attack in 2020. One such company hit by ransomware this year is the Italian multinational Enel Group.
It may seem too big of a profit for hackers with little to no experience in marketing their assets. However, Fxmsp was not alone in this.
According to Yelisey Boguslavskiy, AdvIntel director of security research, Fxmsp was the hacking part of a crew (GPTitan) consisting of specialists "geared to secretly work in financial environments" to steal from high-profile networks data relevant to customers.
GPTitan was assisted in their work by two other crews, one in China and one in the U.S., a collaboration that led to the data breaches at the antivirus companies from the spring of 2019.
An independent source with knowledge about Fxmsp activity told BleepingComputer that the actor stopped acting alone and had expanded into a team.
The non-hacking part of Fxmsp was in charge of marketing and monetizing the network access and the data. A network of affiliates operating under the alias Antony Moricone offered to share breached information to hackers, financial shadow brokers, and 'grey' information traders who used it to shift to their advantage the decision-making process in companies they had an interest in.
![]()
Boguslavskiy does not dismiss the possibility that the aliases in the Antony Moricone crew be operated by a single individual on multiple forums, which is what Group-IB states in their report:
"Group-IB experts were able to identify Lampeduza’s nicknames on other forums: Antony Moricone, BigPetya, Fivelife, Nikolay, tor.ter, andropov, and Gromyko" - Group-IB
The name behind the alias
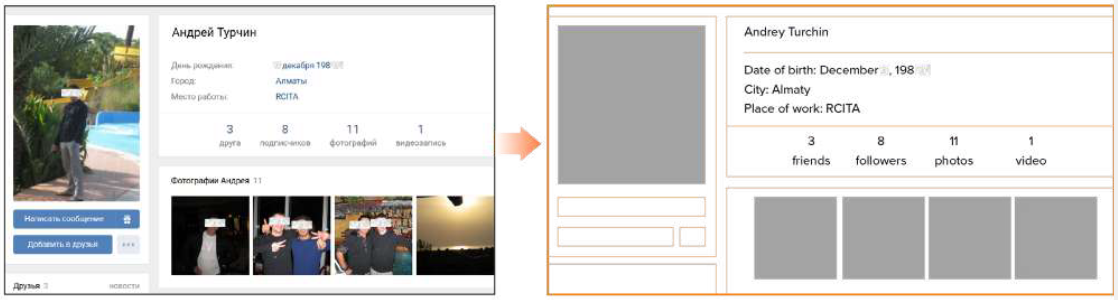
The researchers also revealed in a report today what may be the identity behind Fxmsp: Andrey Turchin (allegedly of Kazakhstan), the same as the one found by BleepingComputer in research last year.

Group-IB’s research, though was more comprehensive as it followed the breadcrumbs in forum posts from the actor and correlated them with domain name registration data and social media profiles on Russian networks (VK, My World).
Dmitry Volkov, CTO of Group-IB says about Fxmsp that they set a trend that led in the second half of 2019 to almost doubling the number of network access sellers specialized in corporate intrusions.
“Prior to Fxmsp joining the underground, the sellers would offer RDP access to separate servers, without even bothering to ensure persistence or performing reconnaissance in the network. Fxmsp took this service into a whole new level” - Dmitry Volkov
Volkov says that Fxmsp might still be active these days, keeping their business private. Even if they’re not on the scene anymore, they set an example for others.
According to trusted sources, Andrey was approached and possibly detained by Kazakhstan law enforcement. BleepingComputer has not been able to independently confirm this information.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now