
Sophos has fixed a zero-day SQL injection vulnerability in their XG Firewall after receiving reports that hackers actively exploited it in attacks.
Sophos states that they received a report on April 22nd that there was a suspicious field value being displayed in a customer's Sophos XG Firewall management interface and began an investigation.
"Sophos received a report on April 22, 2020, at 20:29 UTC regarding an XG Firewall with a suspicious field value visible in the management interface. Sophos commenced an investigation and the incident was determined to be an attack against physical and virtual XG Firewall units. The attack affected systems configured with either the administration (HTTPS service) or the User Portal exposed on the WAN zone," Sophos warned.
This attack used a previously unknown zero-day SQL injection vulnerability, and depending on the configuration of the firewall, could have allowed attackers to steal data from the firewall including "usernames and hashed passwords for the local device admin(s), portal admins, and user accounts used for remote access."
Sophos states that passwords associated with external authentications systems such as LDAP and Active Directory services were not able to be accessed by the attackers.
Hotfix released
Yesterday, Sophos began pushing out this hotfix to all Sophos XG Firewalls that have the "Allow automatic installation of hotfixes" setting enabled on the device. For those who have this setting disabled, you can follow these instructions to install the hotfix.
"This hotfix eliminated the SQL injection vulnerability which prevented further exploitation, stopped the XG Firewall from accessing any attacker infrastructure, and cleaned up any remnants from the attack," explain in their security bulletin.
Sophos states that they completed the rollout of the hotfix to all XG Firewall units who have auto-update enabled at 2020-04-25 22:00.
How to tell if your Sophos XG Firewall was compromised
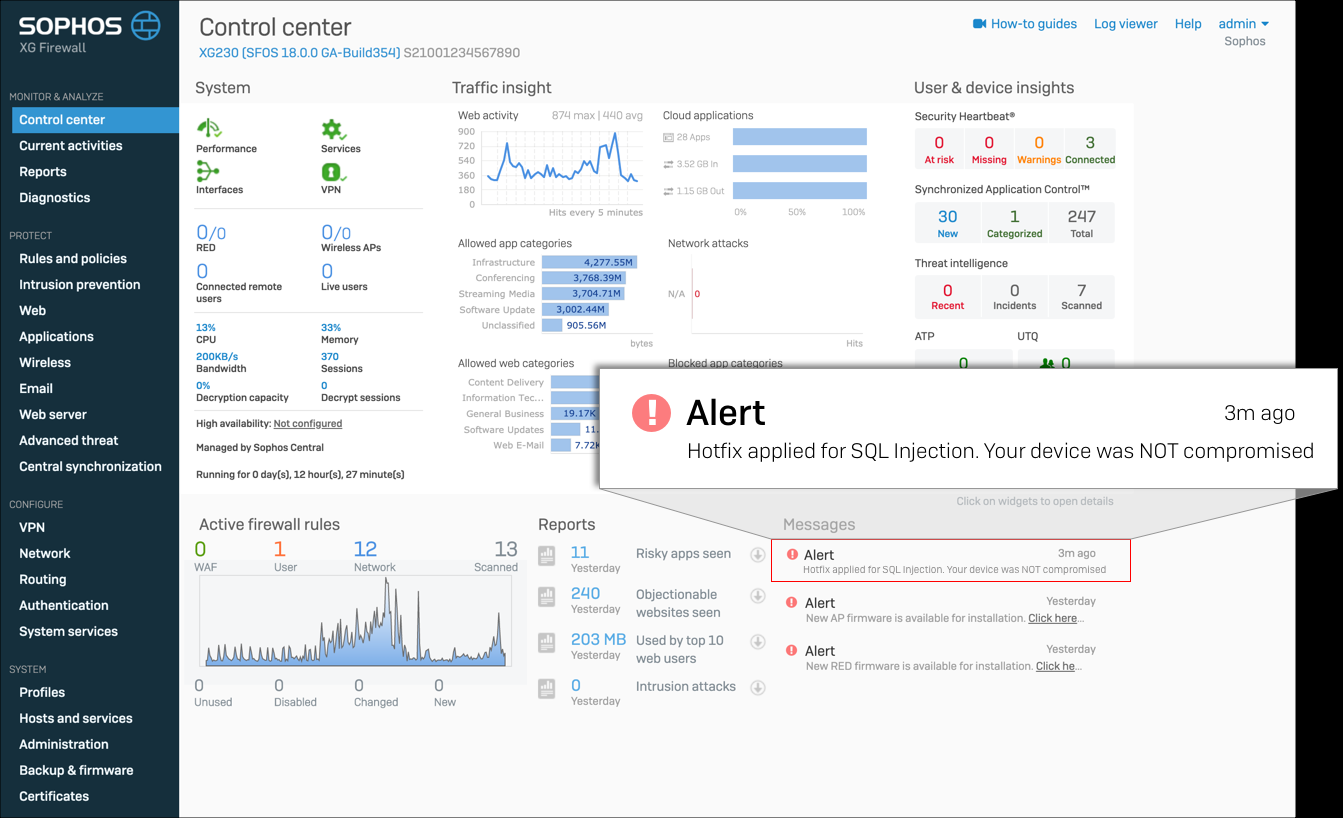
To help customers determine if their XG Firewall has been compromised, the hotfix will display an alert on the XG management interface stating whether your device was compromised or not.
Devices that were not compromised, the hotfix will display an alert stating "Hotfix applied for SQL Injection. Your device was NOT compromised."
Firewalls that have been compromised by the vulnerability, the management interface will display a message warning "Hotfix applied for SQL injection and partially cleaned."
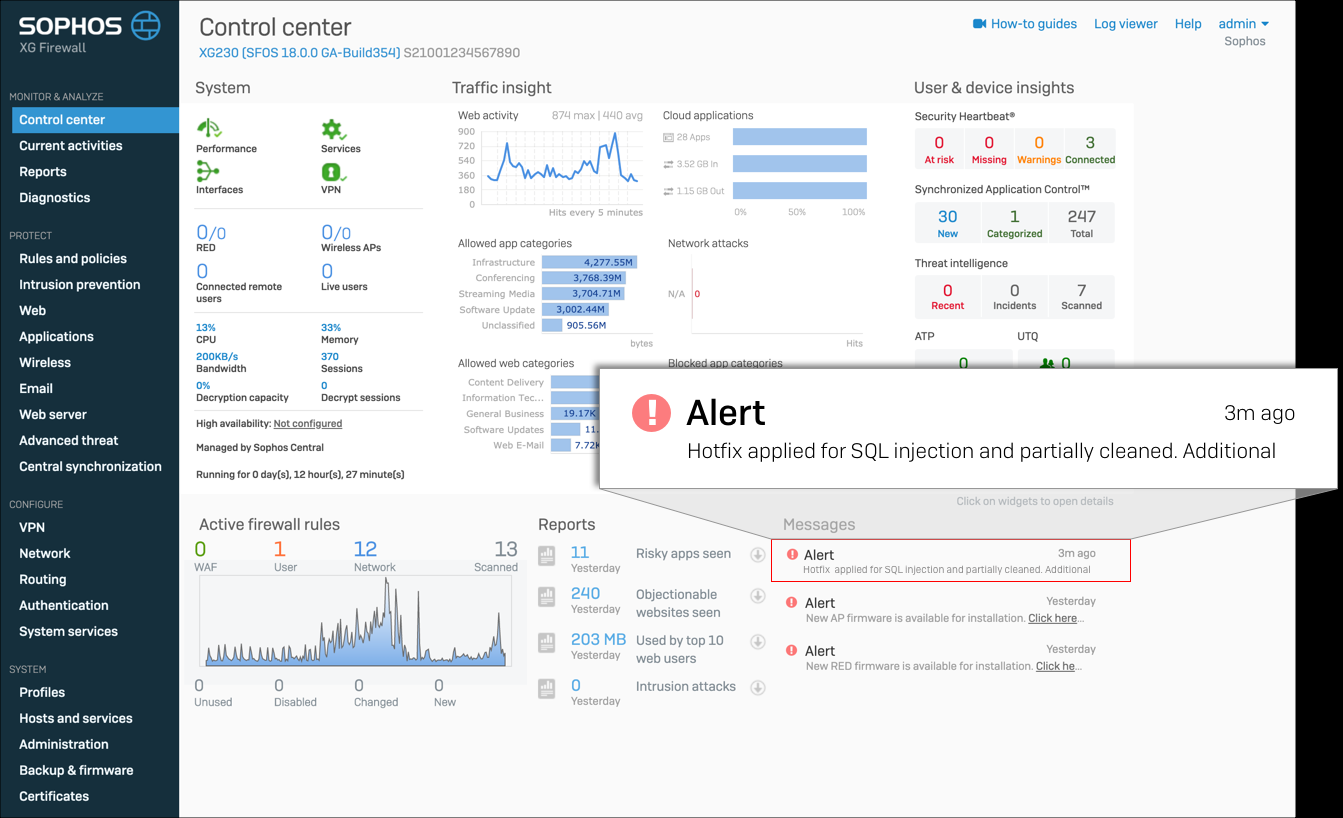
For devices that were compromised, Sophos also recommends that you perform the following additional steps to make sure the firewall is secured.
- Reset portal administrator and device administrator accounts
- Reboot the XG device(s)
- Reset passwords for all local user accounts
- Although the passwords were hashed, it is recommended that passwords are reset for any accounts where the XG credentials might have been reused
Sophos also warns that even after applying the hotfix and performing remediation steps, this alert will continue to be shown in the management interface.


Comments
igioz - 3 years ago
thanks a lot for this article, better than sophos forum itself.