A steady stream of card breaches at retailers, restaurants and hotels has flooded underground markets with a historic glut of stolen debit and credit card data. Today there are at least hundreds of sites online selling stolen account data, yet only a handful of them actively court bulk buyers and organized crime rings. Faced with a buyer’s market, these elite shops set themselves apart by focusing on loyalty programs, frequent-buyer discounts, money-back guarantees and just plain old good customer service.
Today’s post examines the complex networking and marketing apparatus behind “Joker’s Stash,” a sprawling virtual hub of stolen card data that has served as the distribution point for accounts compromised in many of the retail card breaches first disclosed by KrebsOnSecurity over the past two years, including Hilton Hotels and Bebe Stores.
Since opening for business in early October 2014, Joker’s Stash has attracted dozens of customers who’ve spent five- and six-figures at the carding store. All customers are buying card data that will be turned into counterfeit cards and used to fraudulently purchase gift cards, electronics and other goods at big-box retailers like Target and Wal-Mart.
Unlike so many carding sites that mainly resell cards stolen by other hackers, Joker’s Stash claims that all of its cards are “exclusive, self-hacked dumps.”
“This mean – in our shop you can buy only our own stuff, and our stuff you can buy only in our shop – nowhere else,” Joker’s Stash explained on an introductory post on a carding forum in October 2014.
“Just don’t wanna provide the name of victim right here, and bro, this is only the begin[ning], we already made several other big breaches – a lot of stuff is coming, stay tuned, check the news!” the Joker went on, in response to established forum members who were hazing the new guy. He continued:
“I promise u – in few days u will completely change your mind and will buy only from me. I will add another one absolute virgin fresh new zero-day db with 100%+1 valid rate. Read latest news on http://krebsonsecurity.com/ – this new huge base will be available in few days only at Joker’s Stash.”
As a business, Joker’s Stash made good on its promise. It’s now one of the most bustling carding stores on the Internet, often adding hundreds of thousands of freshly stolen cards for sale each week.
A true offshore pirate’s haven, its home base is a domain name ending in “.sh” Dot-sh is the country code top level domain (ccTLD) assigned to the tiny volcanic, tropical island of Saint Helena, but anyone can register a domain ending in dot-sh. St. Helena is on Greenwich Mean Time (GMT) — the same time zone used by this carding Web site. However, it’s highly unlikely that any part of this fraud operation is in Saint Helena, a remote British territory in the South Atlantic Ocean that has a population of just over 4,000 inhabitants.
This fraud shop includes a built-in discount system for larger orders: 5 percent for customers who spend between $300-$500; 15 percent off for fraudsters spending between $1,000 and $2,500; and 30 percent off for customers who top up their bitcoin balances to the equivalent of $10,000 or more.
For its big-spender “partner” clients, Joker’s Stash assigns three custom domain names to each partner. After those partners log in, the different 3-word domains are displayed at the top of their site dashboard, and the user is encouraged to use only those three custom domains to access the carding shop in the future (see screenshot below). More on these three domains in a moment.
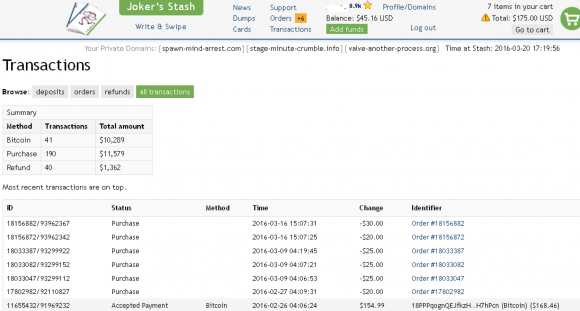
The dashboard for a Joker’s Stash customer who has spent over $10,000 buying stolen credit cards from the site. Click image to enlarge.
REFUNDS AND CUSTOMER LOYALTY BONUSES
Customers pay for stolen cards using Bitcoin, a virtual currency. All sales are final, although some batches of stolen cards for sale at Joker’s Stash come with a replacement policy — a short window of time from minutes to a few hours, generally — in which buyers can request replacement cards for any that come back as declined during that replacement timeframe.
Like many other carding shops, Joker’s Stash also offers an a-la-carte card-checking option that customers can use an insurance policy when purchasing stolen cards. Such checking services usually rely on multiple legitimate, compromised credit card merchant accounts that can be used to round-robin process a small charge against each card the customer wishes to purchase to test whether the card is still valid. Customers receive an automatic credit to their shopping cart balances for any purchased cards that come back as declined when run through the site’s checking service.
This carding site also employs a unique rating system for clients, supposedly to prevent abuse of the service and to provide what the proprietors of this store call “a loyalty program for honest partners with proven partner’s record.”
According to Joker’s Stash administrators, customers with higher ratings get advance notice of new batches of stolen cards coming up for sale, prioritized support requests, as well as additional time to get refunds on cards that came back as “declined” or closed by the issuing bank shortly after purchase.
To determine a customer’s loyalty rating, the system calculates the sum of all customer deposits minus the total refunds requested by the customer.
“So if you have deposited $10,000 USD and refunded items for $3,000 USD then your rating is: 10,000 – 3,000 = 7,000 = 7k [Gold rating – you are the king],” Joker’s Stash explains. “If this is the case then new bases will become available for your purchase earlier than for others thanks to your high rating. It gives you ability to see and buy new updates before other people can do that, as well as some other privileges like prioritized support.”
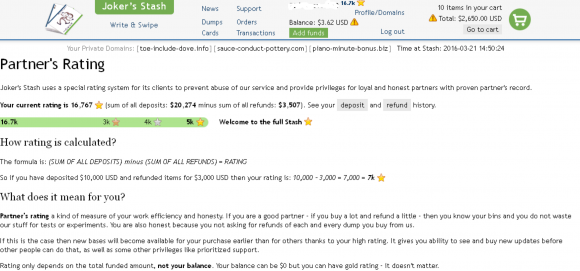
This user has a stellar 16,000+ rating, because he’s deposited more than $20,000 and only requested refunds on $3,500 worth of stolen cards. Click image to enlarge.
HIGH ROLLERS
It would appear that Joker’s Stash has attracted a large number of high-dollar customers, and a good many of them qualify for the elite, “full stash” category reserved for clients who’ve deposited more than $10,000 and haven’t asked for more than about 30 percent of those cards to be refunded or replaced. KrebsOnSecurity has identified hundreds of these three-word domains that the card site has assigned to customers. They were mostly all registered across an array of domain registrars over the the past year, and nearly all are (ab)using services from a New Jersey-based cloud hosting firm called Vultr Holdings.
All customers — be they high-roller partners or one-card-at-a-time street thugs — are instructed on how to log in to the site with software that links users to the Tor network. Tor is a free anonymity network that routes its users’ encrypted traffic between multiple hops around the globe to obscure their real location online.
The site’s administrators no doubt very much want all customers to use the Tor version of the site as opposed to domains reachable on the open Internet. Carding site domain names get seized all the time, but it is far harder to discover and seize a site or link hosted on Tor.
What’s more, switching domain names all the time puts carding shop customers in the crosshairs of phishers and other scam artists. While customers are frantically searching for the shop’s updated domain name, fraudsters step in to take advantage of the confusion and to promote counterfeit versions of the site that phish account credentials from unwary criminals.
Nicholas Weaver, a senior researcher in networking and security for the International Computer Science Institute (ICSI), said it looks like the traffic from the three-word domains that Joker’s Stash assigns to each user gets routed through the same Tor hidden servers.
“What he appears to be doing is throwing up an Nginx proxy on each Internet address he’s using to host the domain sets given to users,” Weaver said. “This communicates with his back end server, which is also reachable as one of two Tor hidden services. And both are the same server: If you add to your shopping cart in Tor, it shows up instantly in the clearnet version of the site, and the same with removing cards. So my conclusion is both clearnet and Tornet are the same server on the back end.”
By routing all three-word partner domains through server hidden on Tor, the Joker’s Stash administration seems to understand that many customers can’t be bothered to run Tor and if forced to will just go to a competing site that allows direct access via a regular, non-Tor-based Internet connection.
“My guess is [Joker’s Stash] would like everyone to go to Tor, but they know that Tor is a pain, so they’re using the clearnet because that is what customers demand,” Weaver said.
Interestingly, this setup suggests several serious operational security failures by the Joker’s Stash staff. For example, while Tor encrypts data at every hop in the network, none of the partner traffic from any of the custom three-word domains is encrypted by default on its way to the Tor version of the site. To their credit, the site administrators do urge users to change this default setting by replacing http:// with https:// in front of their private domains.
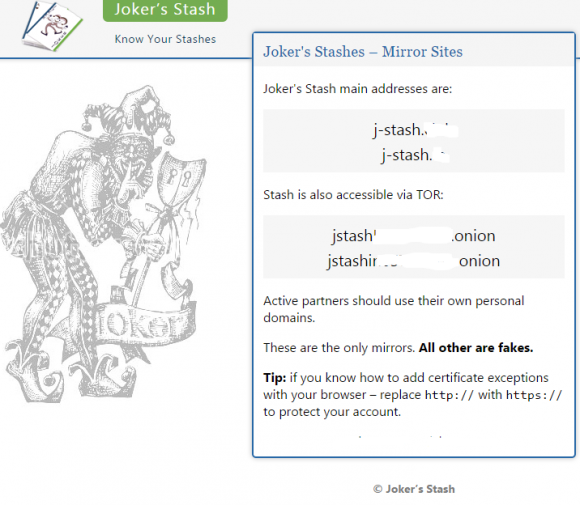
A web page lists the various ways to reach the carding forum on the clearnet or via Tor. The links have been redacted.
I’ll have more on Joker’s Stash in an upcoming post. In the meantime, if you enjoyed this story, check out a deep dive I did last year into “McDumpals,” another credit card fraud bazaar that caters to bulk buyers and focuses heavily on customer service.




Why is it again that the governments or NSA or white hackers can’t destroy these carding sites? I really don’t understand how these criminals are able to do this without being shut down?
They don’t have jurisdiction over other countries. The USA doesn’t own the internet.
What about white hat hackers? Isn’t there any good hackers out there who fight for the people? I just don’t understand how criminals are able to do this so easy like its a real biz.
Sure they can take them down, but 7 more will pop up when the original goes down. And actually gaining access to these services is not always feasible.
White hats are typically security professionals who have day jobs, they’re not rogue hackers that are out to take down others (usually). If they have the skills to be a white hat, they’ll probably take the job that pays for this. And then it goes back to resources and jurisdiction.
And they are trying to fight for us with fraud protections, securitng their sites (you never hear about the sites that were attacked and weren’t hacked), and other things that happen in the background. But they’re human and have their own interests, which is getting paid. They do that through their professional work as a security expert, and they aren’t going to venture out and start attacking illegal websites.
Unfortunately shutting down their site is just going to make a new one pop up, especially if the vendors aren’t imprisoned, since they’ll go back to hacking under a new handle and start selling more cards.
It’s a tough situation but it’s always a stacked game because an attacker only has to win once while a defender has to win every time.
Won”t SOMEONE do SOMETHING!?!?!?!?
Being brutally honest, who is going to pay me to take down those sites? And honestly when I do take down those sites it just cuts into more job opportunities for me. I’m not here to volunteer my time the same way you don’t volunteer your time for your job right? Not running a charity with all due respect.
Think about it, though! You could be the Batman of hackers!
And like any real Batman, you’d end up with a big price on your head, so unless you only used a perfect hidden identity you’d get some big trouble.
Batman isn’t real, Bob.
If you really want to see how these organizations work, read Brian’s book Spam Nation. Great read and really eye opening.
Fighting these outfits is usually just playing whack-a-mole – the real weak link here is a card payment system that was not originally created with modern security in mind. We’re still paying for it at the moment, but with the new security coming into effect – dynamic 3D-Secure, EMV, NFC, HCE, etc. – cards are going to become a tougher and tougher target, and carding shops like this will eventually starve.
White hat hackers have fought for us in the past but they would still be prosecuted under U.S. law if exposed. http://thehackernews.com/2016/02/botnet-antivirus.html
“They don’t have jurisdiction over other countries. The USA doesn’t own the internet.”
LOL, it’s not like that would stop them if they really wanted to do something =D
Well not to mention ‘hacking’ a site and taking it down could actually land the white hat in trouble, no matter how noble it may seem its still against the law. So many wont risk getting in trouble playing whack a mole and not changing anything.
So you’re calling for “white hat hackers” to form some sort of vigilante justice alliance, to break the laws protecting us all, just to knock a few carding sites offline.
What part of that isn’t dangerously stupid? Even your punctuation is moronic.
Whitehat hackers and “good guys” died 15 years ago, along with defensive security. Along with online pc gaming, p2p file sharing, and most forums and chat rooms. Don’t blame phones and tablets. The internet has become facebook and twitter because society has been boxed into a corner and those servers are the only ones left that can best moderate spamming trolls and withstand attacks. It becomes expensive and time consuming. Because nobody is looking out for anybody but themselves nowadays Family doesn’t even matter. Brian Krebs is very rare. And when it comes to so called “security professionals” most of them are just inferiority complexes full of security theatre, marketing, and politics.
They don’t even defend themselves they just hack other people. Offensive tools are called security tools and real defensive tools are now built mostly for enterprise only. The industry is in denial. Most of the problem is still social engineering though, so keeping you uninformed, illiterate, and insecure is as good for job security for the failing security industry as it is for the criminals.
>Along with online pc gaming, p2p file sharing, and most forums and chat rooms.
Um … wut?
because there’s no oil or land. Governments (very organized crime) only care if there is oil or land, then they will trade you and your children’s blood. Crimes like this are just a nuisance. It’s only money, they just print more.
Ah geez……… I feel hosed, no matter what I do and have done to protect myself. Great read, though!!
No worries Sarah, the merchants and banks are the ones that have to deal with the pain for the most part. Granted it will trickle down to us in higher fees im sure. Just don’t use a card that you cant afford to have compromised, ie: ATM card etc.
Well said, and if you are not getting paid to use that credit card then you are doing something wrong. CC companies are offering 5% cash back on many things and at minimum 1% on everything else. They are paying you to use their cards and you are not responsible for thefts so why should you care or complain. If you don’t want this then go to cash only, otherwise stop worrying and start getting paid.
The old its a victimless crime line eh? Every been late on a bill? Ever needed the credit card money and not have it for an emergency? Do you enjoy the hassle?
Brian- do you ever wonder if you are “Trumping” carder sites like this? I mean, if I were a minor miscreant looking to get into the card fraud world, your work would make it pretty easy for me to find good sites to buy from. You writing such a (good) article, basically is free advertising for carders like Joker’s World. Eh?
Perhaps, yes. But greater scrutiny usually serves the public good in the end. Besides, none of these sites last forever, and their curators are top targets for law enforcement.
Open your eyes, Krebs is behind all of this, he’s always been!
– How does he always get the breach stories before anyone else and knows exactly how they happened?
– How does he know in which stores do the cards appear for sale?
– How does he know so much about the technical inner workings of the store?
Easy…
– Cause the breaches yourself
– Report about them
– Write a feature about the store where the cards are being sold, so that everyone knows where to go buy. Fill 80% of the article with scare tactics, drama and other things nobody can fact-check or prove wrong.
– Accept BTC donations for your “security blog” front to launder your earnings.
Simple and effective
Lame and funny. Like Kaspersky… They find new viruses (Virii) because they are the creators.
“For example, while Tor encrypts data at every hop in the network, none of the partner traffic from any of the custom three-word domains is encrypted by default on its way to the Tor version of the site.”
This isn’t making any sense to me at all. Is it just meant to highlight the lack of default encryption between the client and the web proxy? Because if the back end of the proxy is being routed through TOR, then the traffic from the domain to the actual host is being encrypted by virtue of being routed through TOR.
I think the point is, the Tor server and the web server are the same machines, or very close in network terms. That’s the security flaw.
Well, it’s already been disclosed that anyone with sufficient access to a massive number internet backbones can discern the location of a Tor server via a correlation attack. Only nation states, or nation states working in cooperation, could perform this kind of analysis though, since it’s huge in scope.
Wouldn’t it be interesting if some of these sites were actually run by either the government or the banking / card industry and they’re selling real cards in attempt to track down/catch who is buying them?
Where is the .club domain registered out of?
Am I naive enough to think that these shops sell the dumps only once?
If you are not the very first one to buy one, then you most likely have a bunch of blown card numbers that may or may not work.
If you read some of Brian’s other articles on this (like the excellent McDumpal’s one he linked) you’ll see that reputation is VERY important to these operations. Pretty safe to assume that any ‘reputable’ carding operation will only sell cards once. Of course, that doesn’t mean your card hasn’t been compromised multiple times and could be sold by other carding shops.
+1
bobl, that’s part of the ‘game’: customers who buy first have a higher chance of receiving a higher number of valid CC numbers, whereas those who buy down the line will end up with a higher rejection rate.
This creates an incentive system for buyers: spend a lot, spend early and you won’t have to request a lot of replacements, which increases your rating and allows you to make even fresher purchases.
Wow, I love it when you get your teeth into a story! Long form journalism is still the best thing to read. I always enjoy the work you do and am grateful for your research and format of writing.
Thanks again and I look forward to more on this topic.
I am always happy I send you a pittance every once and awhile, It’s better spent here than on the regular news.
Just wondering though, it would seem trivial for the Joker dude to figure out whose screen prints are in your article.
Recently I purchased some gift cards at a Wal-Mart in Alabama and could not use a credit card…only a debit card or cash. Perhaps a policy and computer program change in reaction to these recent credit card scams.
No change. From the credit card company’s point of view, using a credit card to buy a gift card is getting a cash advance without paying the often higher cash advance interest rate and any cash advance fees. That’s also why when you buy something with a credit card and return it, you can only get a credit on the card used for the purchase, rather than getting cash back.
The articles clearly states that the stolen card numbers are used to buy gift cards at Walmart yet you’re saying it didn’t work for you. Maybe other stores are allowing credit cards to buy gift cards?
The article also says stolen credit and debit cards so they might be using the credit cards to buy expensive electronics and the debit cards to buy gift cards.
In addition to what Bob said, there’s the issue of “manufactured spending”, where someone buys gift cards with a credit card to accumulate the points one receives for spending on the credit card. For instance, I received $400 for spending $5,000 on my card.
Brian,
“.[…] I will add another one absolute virgin fresh new zero-day db with 100%+1 valid rate. Read latest news on http://krebsonsecurity.com/ – this new huge base will be available in few days only at Joker’s Stash.”
That site really has balls to use *you* as a reference; *wry grin* Go get ’em tiger!
Cheers,
Shy
Someone should run a search service so your readers can learn if our names, SSNs, specific card numbers. etc., are on those web sites. Is anyone doing that? It would be worth a small fee, if the hits were credible/verifiable, so we would know which cards to cancel/get re-issued.
For email addresses, there’s:
https://haveibeenpwned.com/
Let me explain first how money is created- first. Banks can not print money just like they want they need you to be promise to work to make this printed peace of paper worted!! Only way is that they must lend money this is only wAy to avoid inflation! Reason why Russia has currency money worth nothing because too much money coming into Russia !! So basecly Russia is officially money loundring country and second to keep money circleratin on going banks need to print money but only way if money is given out as loan ! So banks and financial institutions are very interested about the fact that people use credit cards and for them is not matter who are the users actual holders or criminals couse they make money of credit anyways. Let’s not be so naive here !! How ever even that banks will put some tought security in place soon ! the next method in UK banks allready working it will be voice recognition and no more online banking password needed how ever criminals allready have tools to bypass this! How ever after this next step will be rfied microchips becouse internationals fraud hit will be so high that people must take this rfied chips – ok I hope that’s clearing all the questions here why and how !
“What’s more, switching domain names all the time puts carding shop customers in the crosshairs of phishers and other scam artists.”
It looks like that old adage about how there is “no honor among thieves ” is true.
“….none of the partner traffic from any of the custom three-word domains is encrypted by default on its way to the Tor version of the site. ”
Oh my goodness! – does the PCI Standards Council know about this?
*snort* good one
No way I’m taking that “mark-of-the-beast”!
Great beginner scammer guide, thanks Brian!
But hey, as long as it sells ad space and brings clients, who cares huh?
I see on screenshot, they are selling Canada and Latin American cards too, which is 100% (or close to it) on CHIP/PIN… How they still selling this?
Please, don’t tell me that is why on USA you can still swipe a “anywhere in the world chipped card”, because this is not how the credit card system works. If someone from Chile (example) or UK, just swipe the card in US territory, obviously it will be blocked transaction.
For one second I think that EMV is not secure at all.
I don’t have good numbers wrt swipe/dip/tap (the best I can find is from Visa [3], which claims ~4/5 are chip transactions), but I certainly can’t point to many merchants who refuse swipe in Canada (the only merchant I know of that did that was PF Changs in the US after their breach)…
“While Canada is migrating to Chip technology, magnetic stripes will remain on some Visa cards and will continue to provide a safe, reliable and convenient method of payment. In addition, Chip-reading terminals will be able to process Visa cards with a magnetic stripe. Likewise, Chip cards can be processed by non-Chip-reading devices via the magnetic stripe. Use of a Chip card’s magnetic stripe in a magnetic stripe terminal may result in a Liability Shift to the merchant for fraudulent transactions.” [1]
“… your magnetic stripe RBC credit card continues to be a safe, reliable and convenient method of payment. …
… It will take time for all stores and restaurants to be set up with chip-enabled terminals. To ensure your RBC Chip and PIN credit card continues to be accepted everywhere, it will contain a magnetic stripe in addition to the chip. You can therefore expect to experience two types of transactions with your RBC Chip and PIN credit card for some time to come.
Swipe and Sign — the magnetic stripe is swiped and authorized by a signature …
… For the time being, all RBC Chip and PIN credit cards must also include a magnetic stripe to ensure continued acceptance everywhere (including locations that have not converted to Chip and PIN technology). Without the magnetic stripe, cards could not be used at non-chip-enabled terminals. Rest assured that transactions completed with the magnetic stripe on your RBC Chip and PIN credit card are as safe and secure as ever.
… 16. If RBC Chip and PIN credit cards are more secure, why don’t you just give them to all cardholders right now?
As there are still a limited number of chip-enabled terminals in North America, not all cardholders would benefit from having an RBC Chip and PIN credit card right away. While each financial institution will have its own timelines for conversion to Chip and PIN technology, we are all working in cooperation to set the standards that will result in the best experience for you.” [2]
“… 83 per cent of transactions processed in Canada are now ‘chip-on-chip’ (a chip card processed at a chip terminal) …” [3]
So, nearly 1 in 5 Visa transactions weren’t chip as of ~6 months ago.
“Visa’s Ericksen points out that 60% of the transactions Visa handles already don’t require a signature or PIN of any kind. Those are typically everyday purchases under $25, grocery purchases under $50 or — in countries including Australia, Canada and the U.K. — any contact-free payment from a mobile device of $100 or less. She also notes that fraud involving lost, stolen or skimmed PINs accounts for roughly 9% of all card fraud, while counterfeit fraud involving a card’s magnetic stripe is roughly two thirds of all fraud Visa sees in the U.S. Though unattended payment points around the world, including train ticket terminals and bicycle rental kiosks, are being upgraded this year to accept both chip and PIN and chip and signature cards, it doesn’t mean we’ve seen the last of the magnetic stripe.” [4]
“All Visa chip cards around the world also have magnetic stripes on them, so even in countries where chip is a prevalent form of payment, they still have a mag stripe on the back,” … “Even in countries that have been doing chip for 15 years or more, there’s still the occasional small business merchant in a small town who hasn’t upgraded their terminal. In order for the consumer to get the best and most accessible experience at home or when they travel to other countries where chip may not be as pervasive yet, the mag stripe is still on the card, so it can be accepted and the payment can go through.” [4]
[1] http://www.visa.ca/chip/merchants/resources/downloads/VisaChipPIN-FactSheet-En.pdf
[2] http://www.rbcroyalbank.com/credit-cards/chip/questions.html
[3] http://www.visa.ca/en/aboutcan/mediacentre/news/security-over-convenience.jsp
[4] https://www.mainstreet.com/article/why-are-we-not-rushing-to-adopt-chip-and-pin-credit-cards/page/5
They could be selling ‘CVVs’ – all the card information required to perform online transactions, but not enough to produce counterfeit cards.
And no, mag stripe transactions are not automatically blocked on chip cards (that’s why they usually still have the mag stripe as a backup). It’s up to the issuing FI whether they want to block mag stripe transactions or not, and under what conditions. For example, many US merchants will still have old non-chip terminals – is an overseas bank simply going to tell its customers they won’t be able to transact in the US?
Implemented correctly, EMV is plenty secure – and moving core security from hardware to software means its upgradeable too. And don’t take my word for it – Google around and find one fraud case that’s down EMV counterfeit (and doesn’t involve lax implementation by the issuer or acquirer).
Phishers going after criminal credentials when a carder web service is in flux!?! Ironic.
Like this post, looking forward to the deeper dive.
The people running Joker’s Stash (https forcing issue aside) sound like they are pretty good at what they do… a shame their skills aren’t being applied to something better than credit card fraud.