Who is Astoria Company?
Astoria Company LLC is a lead generation company with a network of websites designed to collect information on a person that may be looking for discounted car loans, different medical insurance, or even payday loans.
Users volunteer personal information to any of their lead generation sites, which is then collected and sent to a number of partner sites (such as insurance or loan agencies), that pay per lead referral.
Database Sale on Darkweb Markets
On January 26, 2021, our threat intelligence team became aware of several new breached databases being sold on the Dark0de market by hacking group Shiny Hunters. The data listed for sale included 400 million Facebook users, a database allegedly containing Instagram users, and a 300 million user database allegedly from Astoria Company. The details of the Astoria Company data sale included, most notably, 40 million U.S. social security numbers (these numbers were later proven to be inflated).
Nearly one week later, these databases were published for sale on the Dark0de forum by user ShinyHunters.
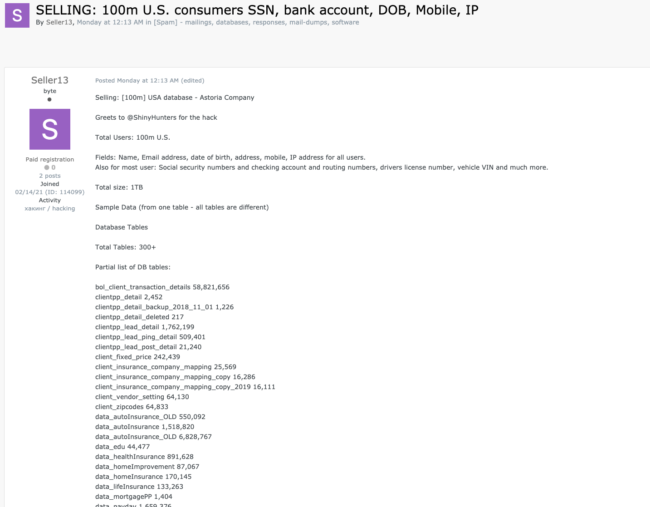
In addition to Dark0de, Astoria’s data later appeared for sale on two additional darkweb forums, this time by “Seller13”. The following screenshot shows the data being sold on Exploit (a popular Russian cybercrime forum). The posts list additional user samples complete with full user information.
Seller13 and ShinyHunters
In a recent blog post, DarkOwl attributes Seller13 to hacking group ShinyHunters. Our own interactions with Seller 13 suggest that he is also “Yousef”, the original broker of nearly 400 million stolen Facebook accounts. DarkOwl’s analysis shows several instances where Seller13 leverages ShinyHunter’s name.
At this time it is unclear whether Seller13 is using the ShinyHunters name as a type of misdirection, or if the two actors are actually working together. Our conversations with Seller13 seem to indicate that he and ShinyHunters are working together.
How The Hack Happened
Trying to understand how this breach could have occurred, our threat intelligence teams began investigating the Astoria Company. Using the Domain Tools IRIS engine, we quickly found a list of more than 400 domains registered to Astoria Company, LLC.
Given ShinyHunters’ tendency to hack sites using leaked credentials, our next step was to use the HiddenWWW search engine to look for publicly accessible code with potentially leaked credentials or AWS keys. The HiddenWWW search engine returned a list of potentially vulnerable URLs across a number of different Astoria domains. We then leveraged an OSINT telegram bot to ping each of the URLs and return a list of any that were valid.
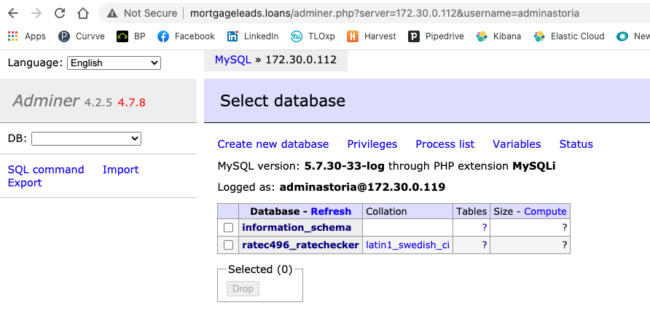
MortgageLeads.loans – Web Shell & Adminer Discovery
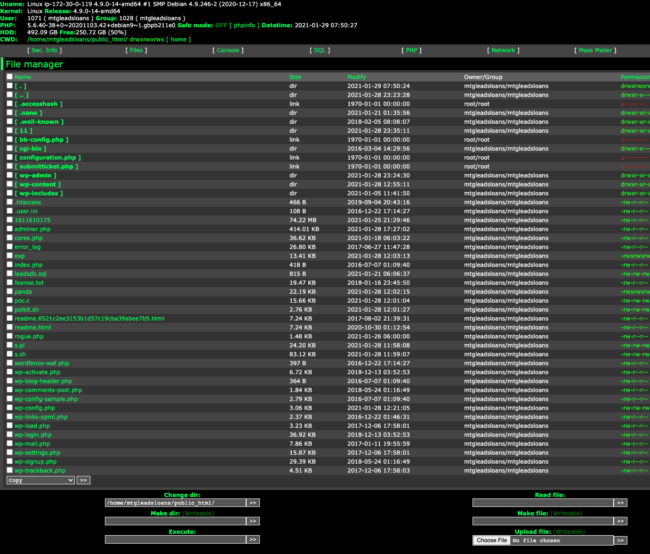
Within the list of returned vulnerable URLs, we identified several web shells and malicious scripts on Astoria’s MortgageLeads.loans domain, including Corex.php and Adminer.php.
Looking at the Corex web shell URL, we can see a number of other exploit tools that were left on the system, including the adminer.php script.
Note: We did not progress any further into the web shell – we only took this single screenshot.
What is Adminer?
Adminer is a database management tool designed to simplify the process of managing any online database type, including MySQL, SQLite, MS SQL, PostgreSQL, and many more.
Visiting the http://mortgageleads.loans/adminer.php URL, we noticed immediately that the admin credentials for user “adminastoria” were pre-saved, allowing anyone complete access to the database from a public URL — no authentication needed.
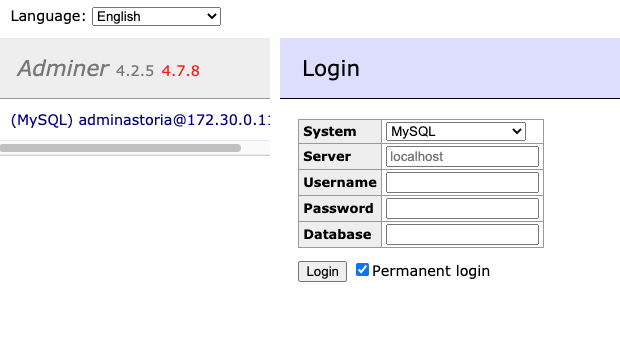
Adminer’s File Disclosure Vulnerability
Night Lion’s counterintelligence team contacted Seller13, who freely volunteered information on how they were able to access Astoria’s database.
As initially reported in 2019, older versions of Adminer are vulnerable to a file disclosure vulnerability. The Sansec.io blog describes a condition with Adminer where an attacker can enter their own remote MySQL server into the Adminer connection window.
Once a connection is established between the two servers, an attacker can read any file on the victim’s server by issuing exploiting a misconfiguration in MySQL allowing the use of the LOCAL INFILE command. This includes any system files including MySQL configuration files and WordPress PHP files which often contain hard-coded passwords.
The above screenshot of the Corex web shell shows the presence of “configuration.php”, which most likely contained the necessary credentials for the attacker to steal the Astoria database.
Disclosure to Astoria
On January 29, 2021, Night Lion Security’s CEO, Vinny Troia, contacted Astoria Company to report the open hole in their database. Troia received a call back from Scott Thompson, Astoria’s CEO, and Randall Box, Astoria’s IT manager. Astoria was unaware that their data had been listed for sale on a dark web marketplace.
Upon being notified of the active Adminer URL, Mr. Thompson made reference to a “former developer from India” that was most likely responsible for maliciously, and intentionally, saving the credentials to the site.
While on the phone with Troia, Astoria’s IT manager identified and confirmed the presence of the malicious scripts, and ultimately took the entire site offline.
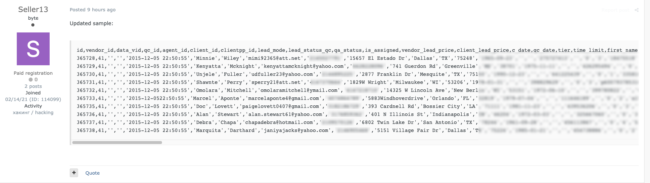
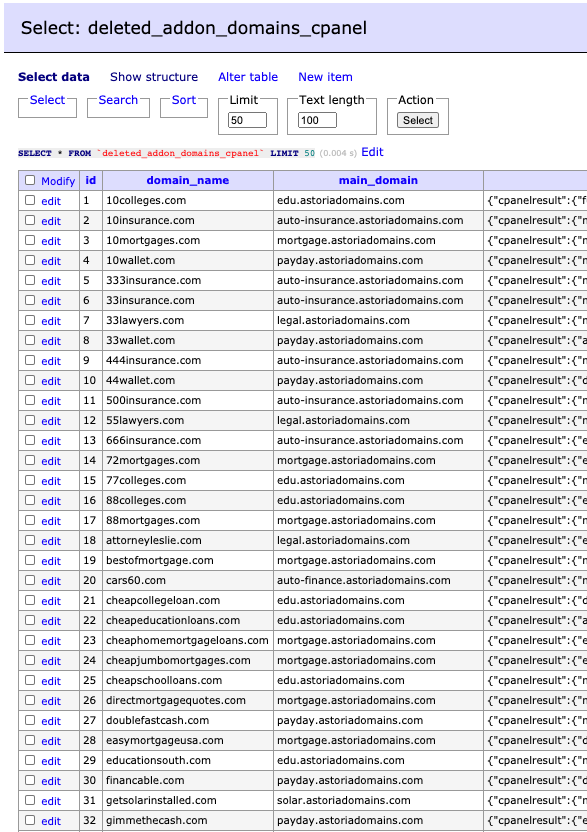
This next screenshot, taken from one of Astoria’s database tables, shows a partial list of deleted “cpanel” sub-domains, all part of astoriadomains.com. Each domain pointing to an astoriadomains.com subdomain is further evidence that the domain (and data) in question belongs to Astoria Company.
19 Vulnerable Astoria Domains
The data provided by PublicWWW search engine shows a total of 19 Astoria-owned domains using the same Adminer script. Each of these servers have been taken down since Night Lion disclosed the leak to Astoria.
- https://beautifulfuture.com/adminer.php
- https://lawsuit-funding-cash-advance.com/adminer.php
- https://limosandtowncars.com/adminer.php
- https://easystudentloanconsolidation.com/adminer.php
- https://globetravel.com/adminer.php
- https://emailunsub.org/adminer.php
- https://pokharatemples.com/adminer.php
- https://nepalrestaurants.com/adminer.php
- https://nepaltravelguides.com/adminer.php
- https://resourcebusinessnetwork.com/adminer.php
- https://thompsonprod.com/adminer.php
- https://mortgageleads.loans/adminer.php
- https://phewalake.com/adminer.php
- https://freequotes.loans/adminer.php
- https://easystudentloanconsolidation.com/adminer.php
- https://educallcenter.com/adminer.php
- https://globetravel.com/adminer.php
- https://beautifulfuture.com/adminer.php
- https://freequotes.contractors/adminer.php
Given that any one of these sites provided a gateway into Astoria’s main database, it is impossible to know which site was used to initially compromise Astoria.
Analysis of Astoria’s Data
The Astoria Company database contained more than 2TB of data across hundreds of tables. The most important user data appeared to be collected in the tables labeled data_ and lead_, for a total of more than one hundred million records (many of which are duplicated).
| Table Name | Record Count |
| archived_accepted_leads | 1,621,130 |
| data_auto | 581,815 |
| data_autoInsurance | 8,636,126 |
| data_autoInsurance_OLD | 7,000,554 |
| data_autoRefinance | 0 |
| data_edu | 44,813 |
| data_edu_direct | 0 |
| data_finalInsurance | 0 |
| data_healthInsurance | 980,022 |
| data_homeImprovement | 318,857 |
| data_homeInsurance | 480,426 |
| data_lifeInsurance | 175,332 |
| data_mortgagePP | 1,657 |
| data_payday | 2,355,962 |
| lead_auto | 46,147,122 |
| lead_autoInsurance | 31,739,270 |
| lead_autoLoanRefinance | 284 |
| lead_edu | 9,813 |
| lead_edu_direct | 66 |
| lead_finalInsurance | 1,388,930 |
| lead_healthInsurance | 46,335,533 |
| lead_homeImprovement | 8,654,618 |
| lead_homeInsurance | 1,776,602 |
| lead_installmentLoan | 660 |
| lead_legal | 458,228 |
| lead_lifeInsurance | 12,968,124 |
| lead_mortgagePP | 247,436 |
| lead_newcar | 1,419 |
| lead_payday | 1,434,855 |
| verified_data_detail | 8,447,007 |
Sensitive User Records and Data Fields
Every lead within the database contains, at a minimum, the following fields:
- Name
- Email address
- Date of Birth
- Mobile Phone
- Physical Address
- IP Address
In addition to the base fields, many of the different lead types included additional information such as social security numbers, full bank account information, and even medical history.
| Auto Leads, Auto Insurance & Payday Loans |
|
| Health Insurance |
|
| Mortgage |
|
Records Sent Via Email
In addition to the raw data tables, the leaked Astoria data also contained email transaction logs showing sensitive user information being transferred, unencrypted, via email.
The following is an example of a single redacted email sent to a gmail address (the original record is not redacted):
(40657,'2016-07-01 06:01:23','VENDOR_POST_REJECTS','EMAIL_SENT',1,260,0,0,0,'SYSTEM','/cronfiles/ews-alert-for-vendors-with-high-rejection-rate-on-post.php\n\nTo: piavadwa@gmail.com\nHeaders: From: tech@astoriacompany.com\r\nReply-To: tech@astoriacompany.com\r\nMIME-Version: 1.0\r\nContent-Type: text/html; charset=ISO-8859-1\r\n\nSubject: Payday POST Error Summary For payday60\nBody:\n SENT TO: pia*****@gmail.com \n(Please let us know if this should be sent to a different email(s)) \n The following is a summary of POST errors for Payday leads you have sent us over the past 24 hours. \n Please check our posting specs to help resolve any issues: https://astoria.com/postingspecs/ \n
| Error | Count | Example |
| Unspecified Error \n \n | 1 | lead_mode=1&lead_type=1&vendor_id=260&sub_id=6&universal_leadid=&tcpa_optin=1&origination_datetime=2016-06-30 15:23:59&origination_timezone=2&tcpa_text=&user_agent=Mozilla%2F5.0%20%28Macintosh%3B%20Intel%20Mac%20OS%20X%2010.10%3B%20rv%3A37.0%29%20Gecko%2F20100101%20Firefox%2F37.0%0D%0A& first_name=Michael& last_name=B****& gender=& dob=1958-06-12& email=b****@gmatc.****& primary_phone=41****& address=39****& zip=53215& city=& state=& mobile=& residence_type=0& months_at_residence=0& years_at_residence=7& employer=Timber ****& job_title=Staff&employment_in_month=5& employment_in_year=2& work_phone=414****& monthly_income=****& income_type=1&income_payment_type=1& income_cycle=1& ssn=3******& in_military=0& bank_name=Tcf National Bank& bank_account_length_months=10& account_type=2& bank_account_number=****& license_number=B****& bank_routing_number=****& license_state=**& loan_amount=***& bank_phone=& ipaddress=**.**.**.**& comments=Mozilla/5.0 (Windows NT 6.1; rv:28.0) Gecko/20100101 Firefox/28.0&tier=ALL&url=https://fastpaydayworld.com/&actual_url=http://api2.astoriacompany.com/cc/payday_cc_v4/ |
Please rectify these issues so we are able to accept more of your leads. If you require further assistance, please email tech@astoriacompany.com
The thousands of emails contained in this log file included similar sensitive information sent to a number of different domains, including (but not limited to)*:
- excelimpact.com
- fusedleads.com
- leadsbarter.com
- gmail.com
- godirectleadgen.com
- jmadvertising.com
- mediaalpha.com
- quotebound.com
- revimedia.com
- match-media-group.com
- suitedconnector.com
* This is only a sample of domains included in the email logs.
Total Exposure Count: 30 Million U.S. People
Astoria’s database contained a significant number of duplicate records. The main concentration of user data was stored in the lead_ tables.
The data_ tables also contained a significant amount of user data, however, this data was not included in the total exposure count because the name and email fields were replaced with null values.
Note: Even though the names were replaced with null values, the data still contained the user’s full mailing address, IP address, and data of birth, as well as additional information like driver’s license number, vehicle information, and extensive medical information such as cancer status, medications, and pre-existing conditions.
Our analysis of the data shows:
- 10 million people with social security numbers, bank accounts, and drivers license numbers
- 10 million+ people with other exposed fields, such as credit history, medical data, home, and vehicle information.
The following redacted screenshot shows one of Astoria’s data tables containing exposed social security numbers and bank account information.
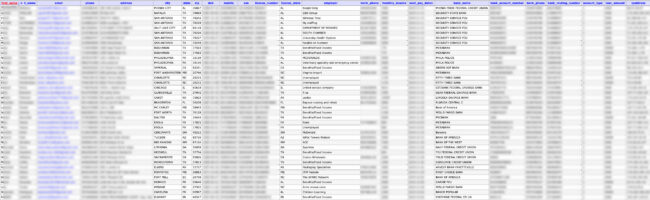
Lead Activity and State Exposure Counts
Based on the information contained in this table, the following is a list of the number of exposed records per U.S. state*:
| TX | 2,301,048 |
| CA | 2,058,865 |
| FL | 1,904,959 |
| PA | 994,893 |
| NY | 982,406 |
| IL | 926,815 |
| GA | 905,784 |
| OH | 788,183 |
| NC | 660,705 |
| MI | 650,980 |
| VA | 559,007 |
| NJ | 518,420 |
| MO | 492,731 |
| IN | 487,279 |
| AL | 475,023 |
| AZ | 469,239 |
| TN | 468,732 |
| MD | 461,643 |
| WA | 442,756 |
| SC | 414,532 |
| CO | 372,676 |
| WI | 345,375 |
| LA | 341,353 |
| MN | 287,196 |
| OK | 280,389 |
| NV | 245,609 |
| OR | 233,345 |
| KY | 224,286 |
| MA | 206,968 |
| AR | 199,444 |
| CT | 190,613 |
| MS | 189,251 |
| KS | 184,373 |
| IA | 172,353 |
| UT | 152,111 |
| NE | 110,959 |
| NM | 107,527 |
| WV | 107,291 |
| ID | 92,625 |
| DE | 80,942 |
| RI | 63,203 |
| NH | 62,486 |
| MT | 56,881 |
| ME | 56,649 |
| DC | 42,787 |
| HI | 35,131 |
| WY | 32,445 |
| SD | 27,774 |
| VT | 25,909 |
| ND | 25,245 |
| AK | 21,987 |
* An additional 8 million user records have not yet been categorized due to the complexity of the data encoding.
Closing Thoughts: Time for A U.S. Federal Standard?
Each U.S. State has its own breach notifications laws, all of which require timeline notification of information disclosure. While none are specific like GDPR’s 72-hour breach notification requirements, there is still an underlying requirement to contact all affected parties. Several proposed standards have been submitted to Congress intended to act as an over-arching Federal standard for breach requirements and notification. However, at the time of this disclosure, those discussions seem to have been shelved.
Perhaps lawmakers involved in privacy discussions will use this disclosure as ammunition to restart those discussions, as well as to revisit the laws around the collection, storage, and distribution of sensitive user data.
NIGHT LION SECURITY
Night Lion Security was founded by Vinny Troia to provide discreet pre- and post-breach security services, including penetration testing, IT audit, and digital forensic investigations. Troia holds a Ph.D. in cybersecurity and is a published author of “Hunting Cyber Criminals”, a book on digital investigations and threat intelligence. In 2020, Hunting Cyber Criminals went to #1 on Amazon’s top networking books.

